What is Application Migration?
Application migration is the process of transferring a software application from one computing environment to another, such as from an on-premises server to a cloud provider or from one cloud environment to another. This involves moving the application code, data, and any associated infrastructure to the new environment.
The primary reasons to migrate applications include improved performance and scalability, cost reduction, improved security, simplified management, and improved disaster recovery options.
There are several types of application migration, including:
- On-premises to cloud: Moving applications from on-premises servers to a cloud provider’s environment (public cloud, private cloud, or hybrid cloud).
- Cloud to cloud: Moving applications from one cloud provider to another.
- Data center to data center: Moving applications from one data center to another (within the same organization or to a different provider).
- Public cloud to private or hybrid cloud: Moving applications from a public cloud to a private or hybrid cloud.
Key steps in application migration include:
- Planning and assessment: Determine the scope of the migration, assess the current infrastructure and application dependencies, and choose the appropriate migration strategy.
- Migration strategy selection: Choose the best approach for migrating the application, such as re-hosting, re-platforming, rearchitecting, rewriting, or replacing.
- Testing and validation: Rigorously test the migrated application to ensure functionality, data integrity, performance, and compatibility with the new environment.
- Data migration: Transfer the application data to the new environment, ensuring data integrity and security.
Post-migration monitoring and support: Monitor the application’s performance and provide ongoing support.
This is part of a series of articles about Application Migration
Table of Contents
Toggle- What is Application Migration?
- Why Migrate Applications? 6 Key Benefits Migration
- Types of Application Migration
- Steps Involved in Application Migration
- Application Migration Risks
- Top 7 Use Cases of Application Migration
- How to Prepare for Application Migration: Key Stages
- Tips from the Expert
- Understanding Application Migration Strategies (The 6 Rs)
- Application Migration Tools
- Application Migration Best Practices
- Reduce Migration Risks with Application Dependency Mapping
- See Additional Guides on Key Application Security Topics
Why Migrate Applications? 6 Key Benefits Migration
Migrating an application to a new environment can offer several benefits, which include:
- Improved performance and scalability: Cloud environments offer more flexible and scalable infrastructure, allowing applications to be scaled up or down based on demand.
- Cost reduction: Migrating to a cloud provider can reduce the need for on-premises hardware and infrastructure, leading to cost savings.
- Improved security: Cloud providers often have robust security measures and tools to protect applications and data.
- Simplified management: Cloud platforms offer centralized management tools, making it easier to manage and monitor applications.
- Disaster recovery and business continuity: Migrating to the cloud can improve disaster recovery and business continuity capabilities.
- Cloud modernization: Migration can also be a step towards modernizing applications and adopting new technologies.
Types of Application Migration
On-Premises to Cloud
This type of migration involves moving applications from traditional on-site servers to a cloud provider’s infrastructure. It typically requires evaluating the existing workloads, identifying dependencies, and selecting the right cloud deployment model (public, private, or hybrid). Common methods include “lift-and-shift” (re-hosting without changes) or re-platforming to take advantage of cloud-native features.
Challenges in this migration include ensuring data consistency, handling latency-sensitive workloads, and adapting security models to the shared responsibility model of cloud providers. Organizations often use tools like AWS Migration Hub or Azure Migrate to streamline the process.
Cloud to Cloud
Cloud-to-cloud migration transfers applications and data from one cloud provider to another. This may be driven by cost optimization, better service offerings, compliance requirements, or avoiding vendor lock-in. The process involves mapping services between providers, such as replacing AWS S3 with Google Cloud Storage or Azure Blob Storage.
Key considerations include compatibility of APIs, differences in service configurations, and potential downtime during the transition. Using containerization (e.g., Docker, Kubernetes) can simplify portability across cloud platforms.
Data Center to Data Center
In a data center to data center migration, applications move between physical facilities, either within the same organization or to a third-party provider. This often occurs during mergers, acquisitions, or consolidation efforts to reduce operational costs and improve efficiency.
The process may involve replicating workloads using tools like VMware vMotion or employing data replication techniques to minimize downtime. Careful network planning is essential to handle bandwidth limitations and ensure seamless cutover.
Public Cloud to Private or Hybrid Cloud
This migration shifts applications from a public cloud environment to a private or hybrid cloud. Organizations often make this move for regulatory compliance, greater control over sensitive workloads, or performance optimization for specific use cases.
It requires redesigning network configurations, implementing private connectivity options like AWS Direct Connect or Azure ExpressRoute, and addressing data residency concerns. Hybrid cloud architectures allow splitting workloads between environments while maintaining interoperability.
Steps Involved in Application Migration
Here’s an overview of the typical application migration process.
1. Planning and Assessment
In this stage, teams perform a detailed analysis of the existing application architecture, dependencies, and infrastructure. This includes identifying components that require refactoring and determining which workloads are suitable for migration. Tools like application dependency mapping and performance baselining help create a comprehensive migration plan.
Risk assessment and compliance reviews are also critical at this stage. Organizations should evaluate regulatory requirements, data privacy constraints, and security postures in the target environment to avoid issues later.
2. Migration Strategy Selection
Choosing the right migration strategy depends on the application’s complexity and business requirements. Common approaches include re-hosting (lift-and-shift), re-platforming (making minor optimizations), and rearchitecting (redesigning the application for cloud-native features).
For legacy applications, replacing with a SaaS solution or rewriting the application entirely may be more cost-effective. Each strategy has trade-offs in terms of cost, timeline, and technical effort that must be carefully weighed.
3. Testing and Validation
Before going live, it’s essential to test the migrated application in the target environment. This includes functional testing, performance benchmarking, and validating data integrity to ensure the application behaves as expected.
Simulating user traffic and load testing can help uncover potential bottlenecks or compatibility issues. A rollback plan should be prepared in case the migrated system fails to meet acceptance criteria.
4. Data Migration
Data migration involves securely transferring application data to the new environment while maintaining integrity and minimizing downtime. Techniques such as database replication, incremental syncing, or bulk transfers are selected based on data size and sensitivity.
Encryption during transit and at rest is critical for protecting sensitive data. Teams must also verify that data formats, schemas, and access controls are compatible with the target environment.
5. Post-Migration Monitoring and Support
After migration, continuous monitoring helps ensure application stability, performance, and security in the new environment. This includes tracking metrics such as response times, error rates, and resource utilization.
Support processes should address any post-migration issues quickly, including optimizing configurations and scaling resources as needed. Implementing automated alerts and health checks can prevent disruptions and improve operational efficiency.
Application Migration Risks
Application migration comes with several risks that need to be carefully managed to ensure a successful transition. Some common risks include:
- Downtime: A migration can result in unplanned downtime, causing disruptions to business operations and potentially affecting customer satisfaction.
- Data loss or corruption: During migration, data may be lost or corrupted due to technical issues, human error, or compatibility problems between the old and new environments.
- Cost overruns: Unforeseen challenges or complexities during migration can lead to higher costs than initially estimated, impacting the budget and return on investment.
- Performance degradation: In some cases, migrating an application to a new environment may result in reduced performance if the application is not properly optimized for the target platform.
- Security vulnerabilities: The migration process may inadvertently introduce new security vulnerabilities or expose sensitive data, putting the application and its users at risk.
- Insufficient testing: Inadequate testing of the migrated application can result in undetected errors, which may affect performance, security, and overall user experience.
- User resistance: Users may resist adopting the migrated application, particularly if they are not adequately trained or informed about the benefits and changes resulting from the migration.
- Project management challenges: Coordinating and managing the various stages and stakeholders involved in the migration process can be complex, potentially leading to delays or miscommunications.
To mitigate these risks, organizations should develop a comprehensive migration strategy, conduct thorough planning and assessment, allocate sufficient resources, perform adequate testing, and engage in effective communication and change management practices.
Top 7 Use Cases of Application Migration
Application migration is not a one-size-fits-all process. Organizations undertake it for a variety of strategic, operational, or technical reasons. Below are some of the most common use cases that drive the decision to migrate applications to a new environment.
- Data center consolidation: Organizations with multiple on-premises data centers often migrate applications to consolidate infrastructure. This reduces operational complexity and cost by centralizing systems, improving utilization, and simplifying management.
- Cloud adoption and digital transformation: Enterprises aiming to modernize IT operations migrate applications to the cloud to leverage its scalability, elasticity, and on-demand services. This is a core part of broader digital transformation efforts, enabling faster deployment cycles and better integration with modern technologies.
- Mergers and acquisitions: During mergers or acquisitions, businesses migrate applications to unify IT environments. This ensures consistency across systems, reduces redundancy, and streamlines operations between the merged entities.
- End-of-life infrastructure: When hardware or software reaches end-of-life and is no longer supported, organizations migrate applications to newer platforms to maintain support, security, and performance.
- Compliance and regulatory requirements: Applications may be migrated to environments that meet updated compliance standards (e.g., HIPAA, GDPR, PCI-DSS). This ensures adherence to legal requirements and reduces the risk of penalties.
- Performance optimization: If existing infrastructure can’t meet performance requirements, applications may be moved to environments with better resource availability, such as high-performance cloud environments or regional data centers closer to users.
- Disaster recovery and business continuity: Applications are sometimes migrated to create or enhance disaster recovery setups. This ensures data and services remain available during outages or disasters, minimizing business disruption.
How to Prepare for Application Migration: Key Stages
Here are the primary stages involved in preparing for an application migration:
Application Identification and Assessment
The first step is to identify and assess the application you want to migrate. You need to understand the application’s architecture, dependencies, data flows, and performance characteristics. Place a special emphasis on the following criteria:
- Complexity: Applications with a complex architecture or numerous dependencies and integrations can pose significant challenges during migration. Therefore, it’s essential to assess the complexity of your applications before you decide to migrate them.
- Criticality: The criticality of an application refers to its importance to your business operations. Applications that are critical to your business should be carefully evaluated before migration. Any disruption to these applications during migration can have a significant impact on your business.
- Availability: Applications that require high availability may need special considerations during migration. For instance, you may need to schedule the migration during a maintenance window to minimize downtime.
- Compliance: If your applications handle sensitive data, you need to ensure that the migration process complies with the relevant data protection laws and regulations.
Total Cost of Ownership (TCO) Assessment
Before you embark on the migration process, it’s essential to assess the total cost of ownership (TCO) of the application in the new environment. This involves considering the cost of the migration process itself, the cost of running the application in the new environment, and any potential cost savings.
The TCO assessment will help you decide whether the migration is financially viable. If the costs outweigh the benefits, it might be better to reconsider the migration.
Overall Risk and Project Duration Assessment
Another crucial stage in the migration process is evaluating the potential risks associated with the migration and estimating how long the migration will take.
The risk assessment should consider both technical and business risks. Technical risks could include data loss, application downtime, or performance issues. Business risks could include impact on customers, loss of business, or regulatory compliance issues.
The project duration assessment should take into account applicable technical best practices, the level of skill of those carrying out the migration, expected technical challenges, and benchmarks of similar migrations carried out at other organizations.

Lanir specializes in founding new tech companies for Enterprise Software: Assemble and nurture a great team, Early stage funding to growth late stage, One design partner to hundreds of enterprise customers, MVP to Enterprise grade product, Low level kernel engineering to AI/ML and BigData, One advisory board to a long list of shareholders and board members of the worlds largest VCs
Tips from the Expert
In my experience, here are tips that can help you successfully manage application migration projects:
-
Conduct a thorough pre-migration assessment
Evaluate application dependencies, complexity, and criticality to determine the most suitable migration strategy.
-
Choose the right migration strategy
Select from the 6 Rs (Rehost, Refactor, Replatform, Repurchase, Retire, Retain) based on your specific needs.
-
Leverage automated migration tools
Use tools to streamline the process, reduce errors, and minimize downtime.
-
Ensure robust testing and validation
Test extensively pre- and post-migration to identify issues early.
-
Prioritize stakeholder communication
Keep stakeholders informed and provide training for a smooth session.
Understanding Application Migration Strategies (The 6 Rs)
Rehost (Lift and Shift Application Migration)
This approach means simply moving an application from one location to another, without any changes. You just redeploy the application in question to the new environment. Think about migrating VMs to a public cloud account, or moving applications from one secure on-premises data center to another. It’s the fastest approach, and will have the least impact on other applications.
Learn how you can gain full network visibility in virtual environments
Of course, there are downsides to this approach to application migration, too. As you have simply rehoused them without any changes, they won’t get any of the benefits of cloud computing, and they won’t be optimized for cloud costing, either. In the long run, these may need some modifications to make the processes more efficient and cost-effective in their new environment.
Refactor (Rip and Replace Application Migration)
This one has a few names, such as re-architecting or replacing, but it’s about changing the application so that it’s ready for the cloud, by changing code or architecture to something more effective for the new environment. Here you need to be more aware of the application dependencies, something Faddom works with every day – your can grab a free trial and test it out yourself.
Simply put, when you make changes to one application, you need to make sure that it won’t impact the behavior of the application or any others. If you’re moving this application to the cloud so that you can add scale, features, or flexibility – it will likely need some refactoring along the way. Faddom can help you to work out your ‘minimum viable refactoring’, the amount of change you need to make to get the results that you need, with the least impact on the rest of your environment.
Replatform
Replatforming involves making some changes to the application’s architecture to take advantage of the capabilities of the new environment. However, unlike refactoring, the core architecture of the application remains the same.
This strategy allows you to gain some of the benefits of the new environment, such as improved scalability or performance, without the extensive code changes required by refactoring. Replatforming is a good option if you want to strike a balance between speed, cost, and performance improvements.
Repurchase (Drop and Shop Application Migration)
Sometimes, it’s just going to be too complex to refactor your applications to get them ready for migration, or you won’t get the end results that you’re looking for. In this case, it would make sense to simply drop, or “Retire” the systems in question, and then use a subscription or an outright purchase to meet the gap. Third party systems are often much more efficient, cost-effective and simple to manage, with the vendor handling a lot of the behind the scenes maintenance and support.
For SMBs, this could be a smarter way to access all the functionality that they need, without building in-house applications from scratch. It can also allow organizations to move away from legacy complexity or on-premises systems that are impossible to refactor or rehost.
You may find this useful – Faddom’s Cloud Migration Tool
Retain (Keep and Consider Application Migration)
Of course, if the right solution isn’t out there for replacement, or you aren’t ready to retire certain applications, you can always retain them, just keep them as they are, either on-premises or on a different cloud environment, and then reconsider your situation further down the line. Reasons for retaining your applications in their current environment could be that it’s an unaffordable project right now, it’s too large to be migrated as a whole, or you can’t afford the application downtime at this point in your business process.
Retire
Retiring is a migration strategy that involves decommissioning applications that are no longer needed. This could be because the applications are outdated, redundant, or not aligned with your business goals.
Retiring applications can free up resources and reduce complexity in your IT landscape. However, it also requires careful planning to ensure that the decommissioning process doesn’t disrupt your business operations or result in data loss.
Application Migration Tools
What Are Application Migration Tools?
Application migration tools are software solutions that assist in moving applications from one environment to another. They automate many of the tasks involved in migration, reducing the risk of errors and speeding up the process.
Application migration tools provide a range of functions including discovery and assessment, migration planning, data transfer, post-migration testing, and monitoring. Some tools focus on specific types of migrations, such as cloud-to-cloud, while others are more versatile and can handle a variety of scenarios.
Discovery and assessment is the first step in any migration project. These tools will scan your current environment to identify all applications and their dependencies. They can also assess the suitability of an application for migration, helping you to decide which applications to move and in what order.
Features of Application Migration Tools
Key features of application migration tools include:
- Application inventory: Helps you understand the complexity of your environment and make informed decisions about your migration strategy.
- Migration planning: Design a migration plan that minimizes downtime and disruption. They can also suggest the most efficient migration path, taking into account factors such as network bandwidth, data transfer costs, and application performance characteristics.
- Data transfer: Enabling secure, high-speed data transfer, ensuring that your data is moved safely and quickly. Some tools can synchronize data between the source and target environments, capturing changes made during the migration process.
- Post-migration testing: These tools can verify that your applications are functioning correctly in the new environment. They can also monitor performance and provide alerts if any issues are detected.
Examples of Application Migration Tools
There are many application migration tools on the market, each with its own strengths and weaknesses. Here are a examples of free migration tools offered by the leading cloud providers:
- AWS Migration Hub provides discovery, planning, migration, and post-migration monitoring capabilities. It supports migrations from on-premise environments to the AWS cloud, as well as between AWS regions and accounts.
- Microsoft Azure Migrate provides integrated discovery, assessment, and migration capabilities for moving applications to the Azure cloud. It also offers advanced features such as application dependency mapping and performance-based sizing.
- Migrate for Google Compute Engine is a tool designed to make it easy to move and run applications in Google Cloud. It automates many of the tasks involved in migration and provides a high-performance, highly reliable data transfer service
Application Migration Best Practices
To ensure a successful application migration, consider implementing the following best practices:
- Assess and plan: Thoroughly assess your current application environment, including dependencies, performance, and security requirements. Develop a detailed migration plan outlining objectives, timelines, resource allocation, and potential risks.
- Choose the right migration strategy: Select a migration strategy based on your application’s complexity, requirements, and desired outcome.
- Prioritize security: Ensure that security measures are in place throughout the migration process. Assess the security capabilities of the target environment and implement necessary controls to protect sensitive data and maintain compliance with industry standards.
- Test and validate: Before executing the migration, perform comprehensive testing to identify potential issues and ensure compatibility with the new environment. Once the migration is complete, validate the application’s functionality, performance, and security to ensure a seamless transition.
- Communicate with stakeholders: Keep all relevant stakeholders informed throughout the migration process. This includes providing updates on progress, addressing concerns, and managing expectations.
- Leverage automation: Utilize automation tools to streamline the migration process, minimize human errors, and reduce downtime.
- Provide user training and support: Train users on the new environment, including any changes in functionality or user experience, and provide ongoing support to ensure a smooth transition.
- Monitor and optimize: Continuously monitor the migrated application’s performance, security, and resource usage. Use analytics and performance data to identify areas for optimization and make adjustments as needed.
- Establish a rollback plan: In case of migration failure or significant issues, have a rollback plan in place to restore the application to its original environment with minimal disruption.
- Learn from experience: After completing the migration, document lessons learned, and use this knowledge to improve future migration projects.
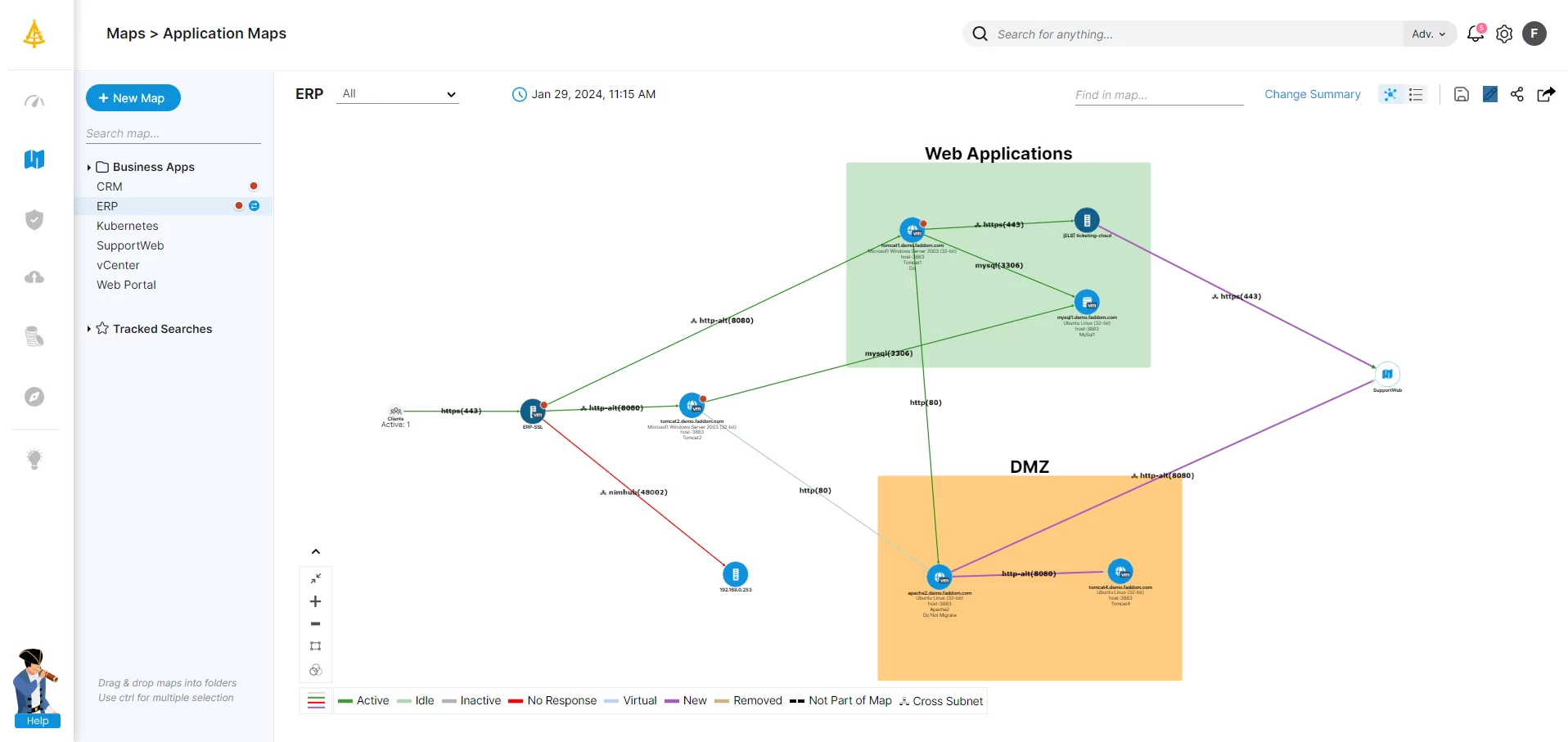
Reduce Migration Risks with Application Dependency Mapping
Faddom is an agentless, self-service application mapping solution that provides clear visibility into your on-premise and cloud infrastructure in just 60 minutes. By mapping applications and their dependencies, Faddom helps reduce risks, optimize resources, and ensure a smooth migration.
Start your free trial today and see how Faddom simplifies your application mapping and migration process.
See Additional Guides on Key Application Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of application security.
Cyber Attack
Authored by Imperva
- [Guide] What is a Cyber Attack | Types, Examples & Prevention
- [Guide] What Is an Insider Threat | Malicious Insider Attack Examples
- [Blog] CVE-2023-22524: RCE Vulnerability in Atlassian Companion for macOS
- [Product] Imperva Account Takeover Protection
API Security
Authored by Pynt
- [Guide] API Security: Threats, Tools, and Best Practices
- [Guide] API Attacks: 6 Common Attacks and How to Prevent Them
- [Product] Pynt | Offensive API Security Testing Platform
API Security Testing
Authored by Pynt