Visualize Your
Hybrid IT Infrastructure Interdependencies in Minutes
Gain complete visibility by automatically mapping your on-premises, cloud, or hybrid servers in real-time and grouping them by business applications—no agents required.
No sales call or credit card required
Trusted by:




Gartner® Recognized Faddom as a Sample Vendor in the 2025 Hype Cycle™
for ITSM’s Technology Dependency Hub Category
Faddom's Solutions for Complex IT Environments
Start Mapping with Faddom!




Start a quick walkthrough of FADDOM
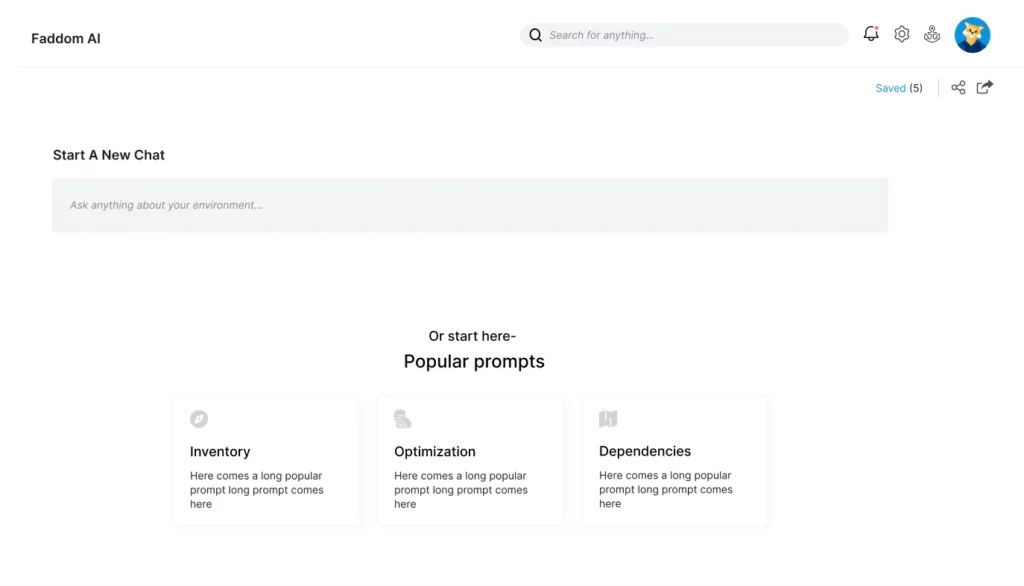
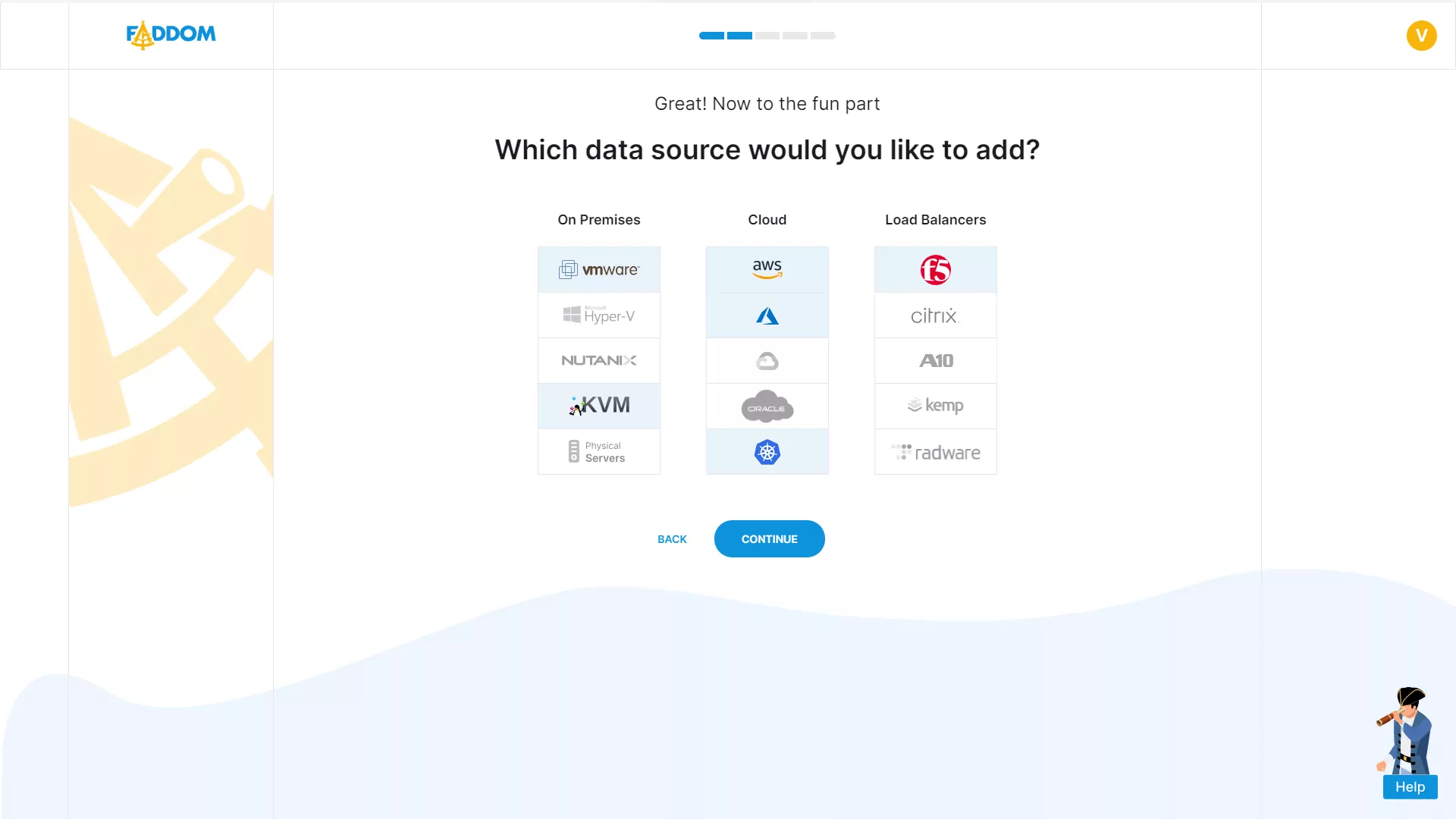
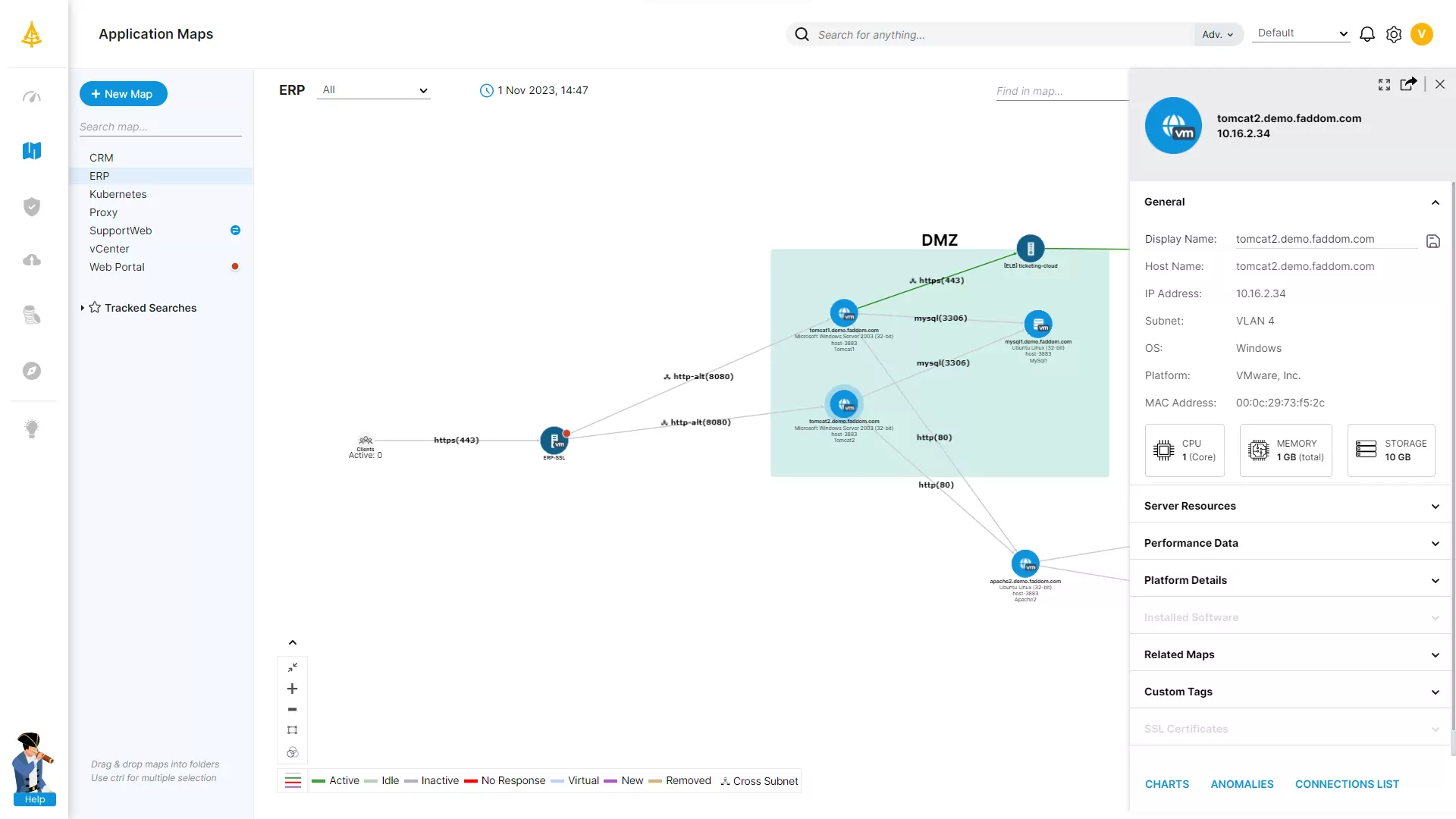
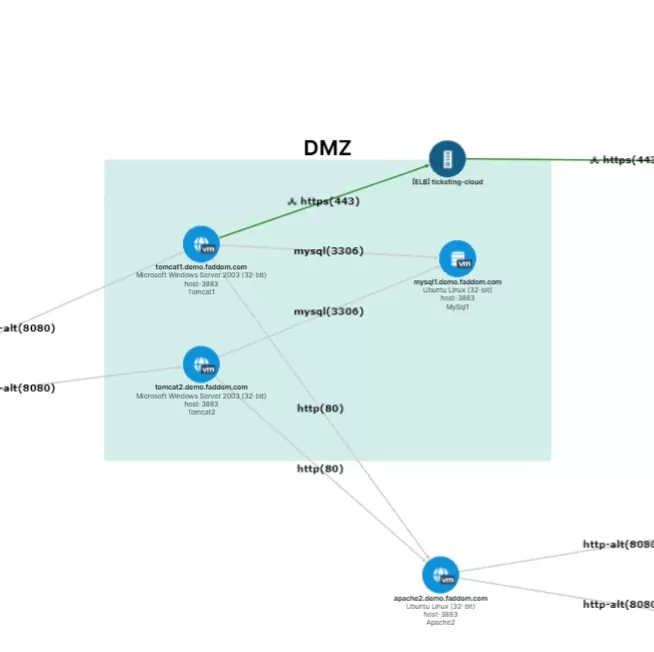
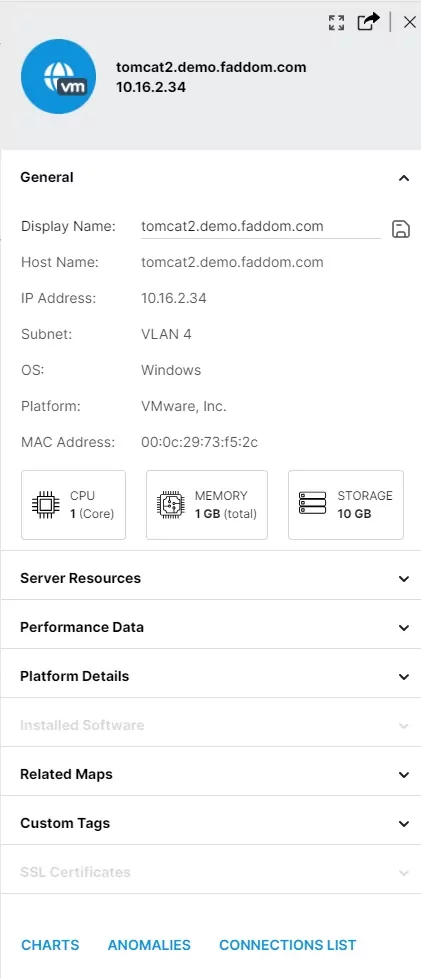
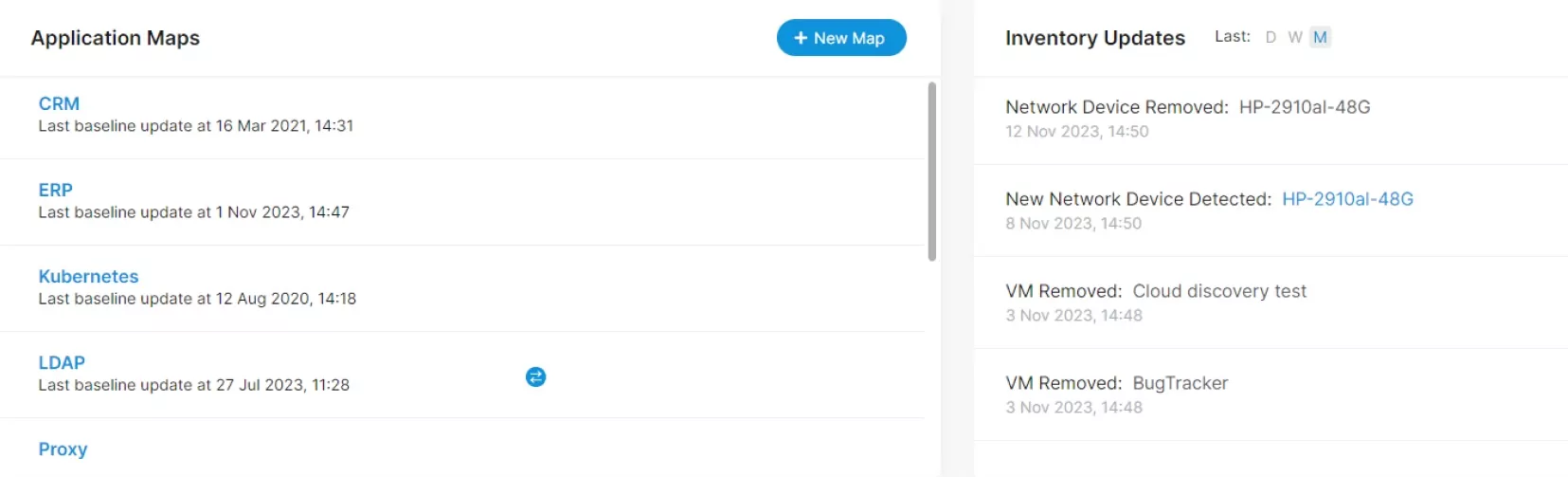
Map all types of data sources
No more guesswork with understanding dependencies
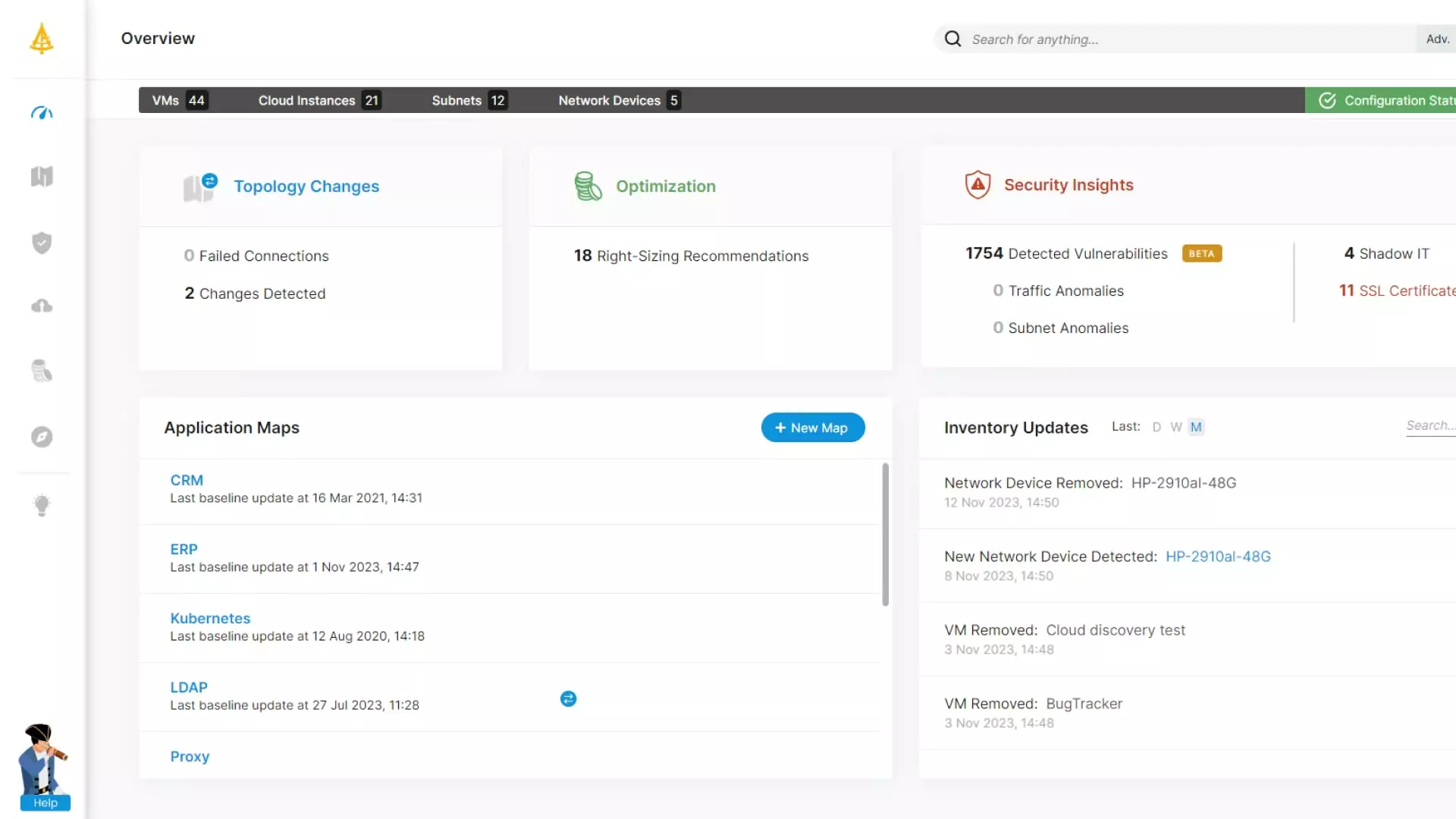
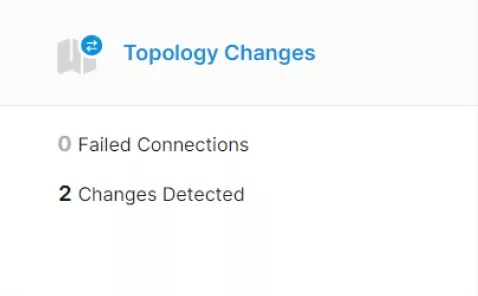
Always know what changed and why
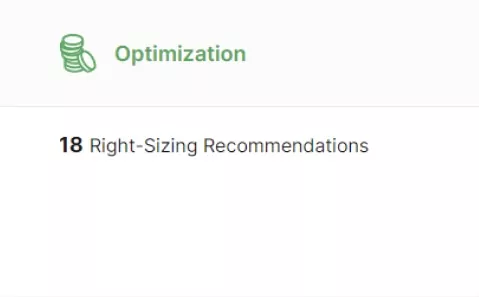
Run your IT operations efficiently and securely
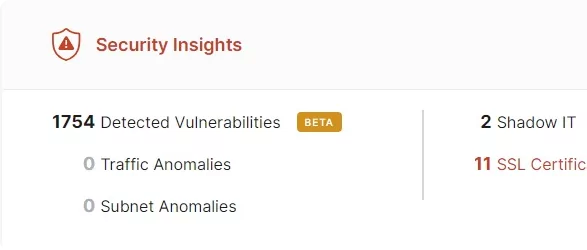
You can't protect what you can’t see
You are 60 minutes away from mapping
your first business application
Get your 14-day FREE trial now!



“Infrastructure & Operations leaders find that conventional, manual and centralized IT service management practices do not support the necessary speed of delivery and the pace of change in hybrid digital environments, resulting in increased cost and toil, as well as diminished effectiveness.”
Gartner® A Blueprint For Modernizing Your ITSM Practice to Drive Digital Transformation, July 2024.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
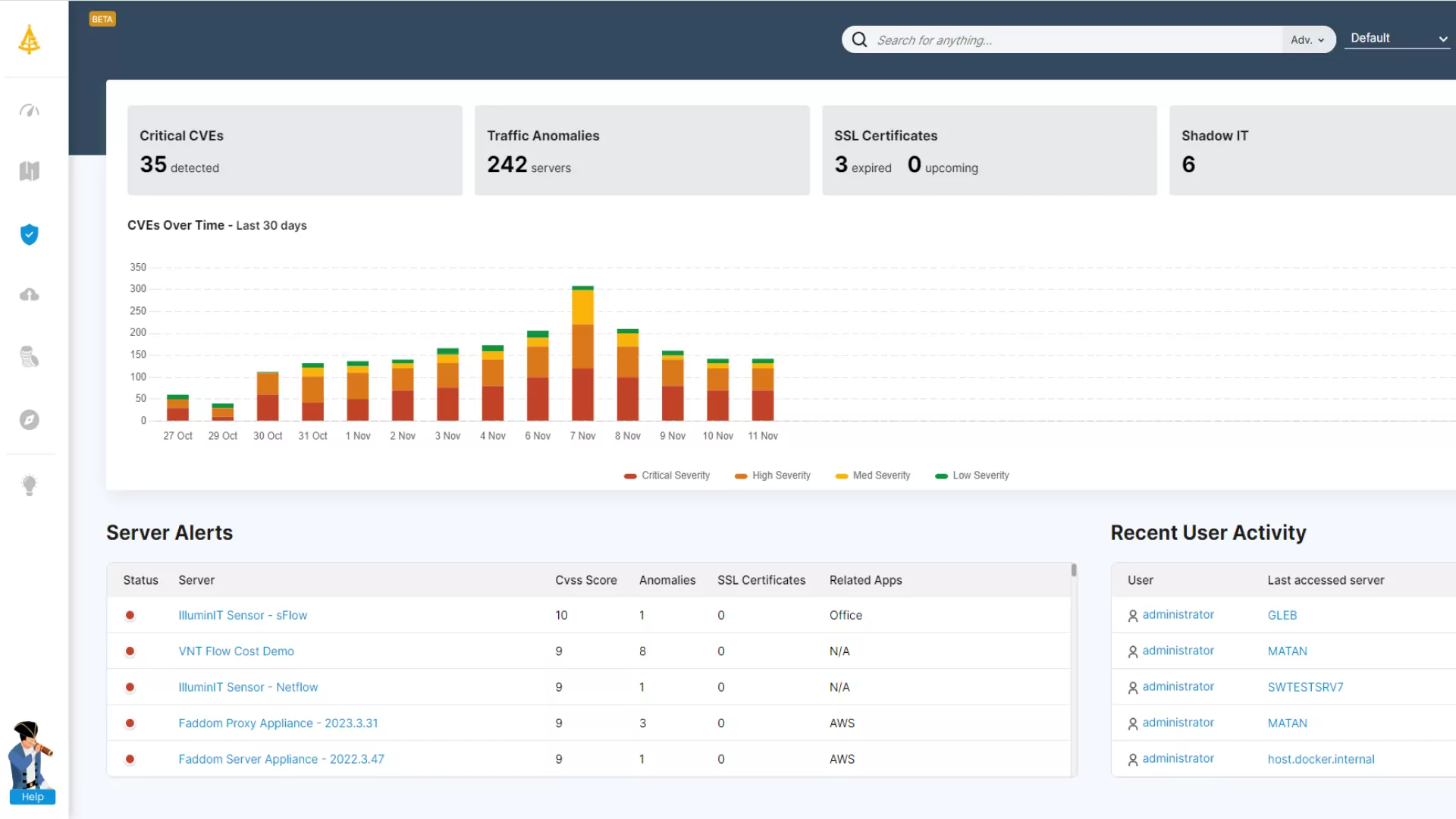
How Faddom Makes a Difference?



“Infrastructure & Operations leaders find that conventional, manual and centralized IT service management practices do not support the necessary speed of delivery and the pace of change in hybrid digital environments, resulting in increased cost and toil, as well as diminished effectiveness.”
Gartner® A Blueprint For Modernizing Your ITSM Practice to Drive Digital Transformation, July 2024.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
What Our Customers Have to Say

Faddom has been a massive asset to our business, enabling us to have all our application interfaces neatly mapped and ready to view. This clarity is essential for maintaining a comprehensive view of our application roadmap.

Head of IT Governance

It’s amazing how quickly we can visualize both on-premise and cloud infrastructure, and it only took about an hour to get started. Using Faddom, we gained valuable insights into all dependencies between servers and applications.

Brad Waller
Infrastructure Manager
The infrastructure is constantly changing because of microservices and the system helps us track all the changes that happen on a daily basis.

The agentless application dependency mapping tool is incredibly intuitive to use and has become a strategic asset in understanding the dependencies between servers and applications. I can now confidently make changes to our IT infrastructure without worrying about any disruptions to our business applications and revenue generation. Highly recommended for anyone in the IT and cybersecurity field!

Steven Poot
Cyber Security Architect

Faddom’s application dependency mapping tool is powerful and eloquent in its ability to gather the facts and present them in graphical and textual format. Great tool to assess your network and traffic flows.

Troy Clavel
CTO
Faddom is an excellent tool to help see what devices are talking to each other on your network. From application mapping to data center diagraming it really has a lot of value in one tool.
Faddom’s solution is super lightweight and gives value in record time. The planning stage for performing a migration was cut substantially because of Faddom’s quick and easy tool.
Faddom has done exactly what it was bought for, far cheaper than anything else we could find on the market.

The easy to use graphical interface and intuitive functions mean that it is a short learning curve to derive real value from the investment in the software.
The solution offers us an in-depth insight into our environment. Show communication flows and all dependencies of our in-house applications, even shadow-it applications, don’t have any secrets anymore.

We had been looking for a cost effective tool for sometime that would show us application dependencies allowing us to use it to inform change control and strategy.

Darren Bolton
Enterprise Architect
It is the only product where I actually can request new features or get immediate support feedback to implement my query.

The software is extremely easy to setup, very user friendly, easy to update. Support received from the company is great.

Faddom has greatly increased my understanding of the dependencies between our servers and applications, allowing me to make changes confidently without fearing a negative impact on our business applications.

Michelle Corbett
Cyber Security Specialist
After half an hour of configuration, we already saw traffic coming in. The great thing about Faddom is that it uses a copy of the traffic, so we started to see traffic initiated from the source that where blocked by the firewall. This made it easy for us to map applications, troubleshoot flows, and detect changes in the environment.


It’s intuitive, promotes proactivity, and the real-time visualization ensures strategic decisions are made with confidence. The customer-focused support and security aspects are icing on the cake.

Kyle Wetzel
Senior IT Architect
Navigate With Dynamic Maps
Use faddom to gain 24/7 visibility in the rocky seas of it
Fast
Be proactive and see your first maps within one hour of deploying Faddom in your environment
Secure
Lightweight. No agents. No credentials. No firewall changes needed. Works offline
Affordable
No sales call needed. No Credit Card Needed
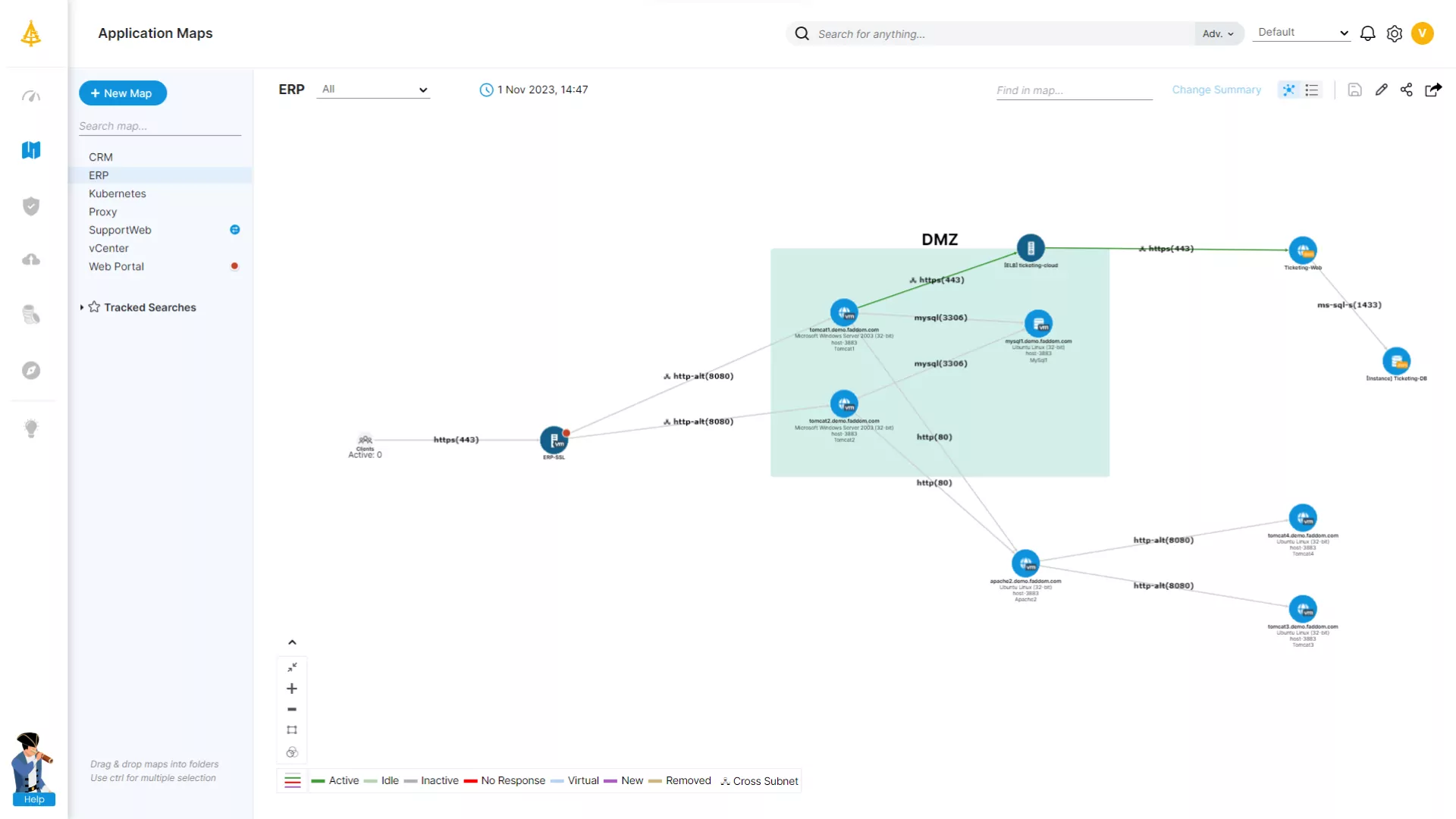
Hybrid Mapping of All Types of Data Sources
Just connect your environments and discover your hybrid business applications in a few minutes.









Application Dependency Mapping
Comparative Analysis
Agentless, passive, works in real-time
Agent-Based Tools
Agentless But With Active Scanning
Native or Freemium Cloud Tools
Security Considerations
No open firewalls, server credentials, or internet needed; all data stays within your environment
Provides full access to a 3rd party
Open firewalls and server credentials
All your data is online
Ease of Deployment
Automated lightweight deployment; takes less than 60 minutes
Installing agents on every servers
Giving all server credentials and reconfiguring firewalls
Agent-based or active agentless, with all its implications
Accuracy
Map the entire environment in real-time, updating 24/7
Accurate where installed, but doesn’t offer a complete view
Blind spots between scans, aren’t real-time, FWs can interfere
Inherently don’t support other platforms