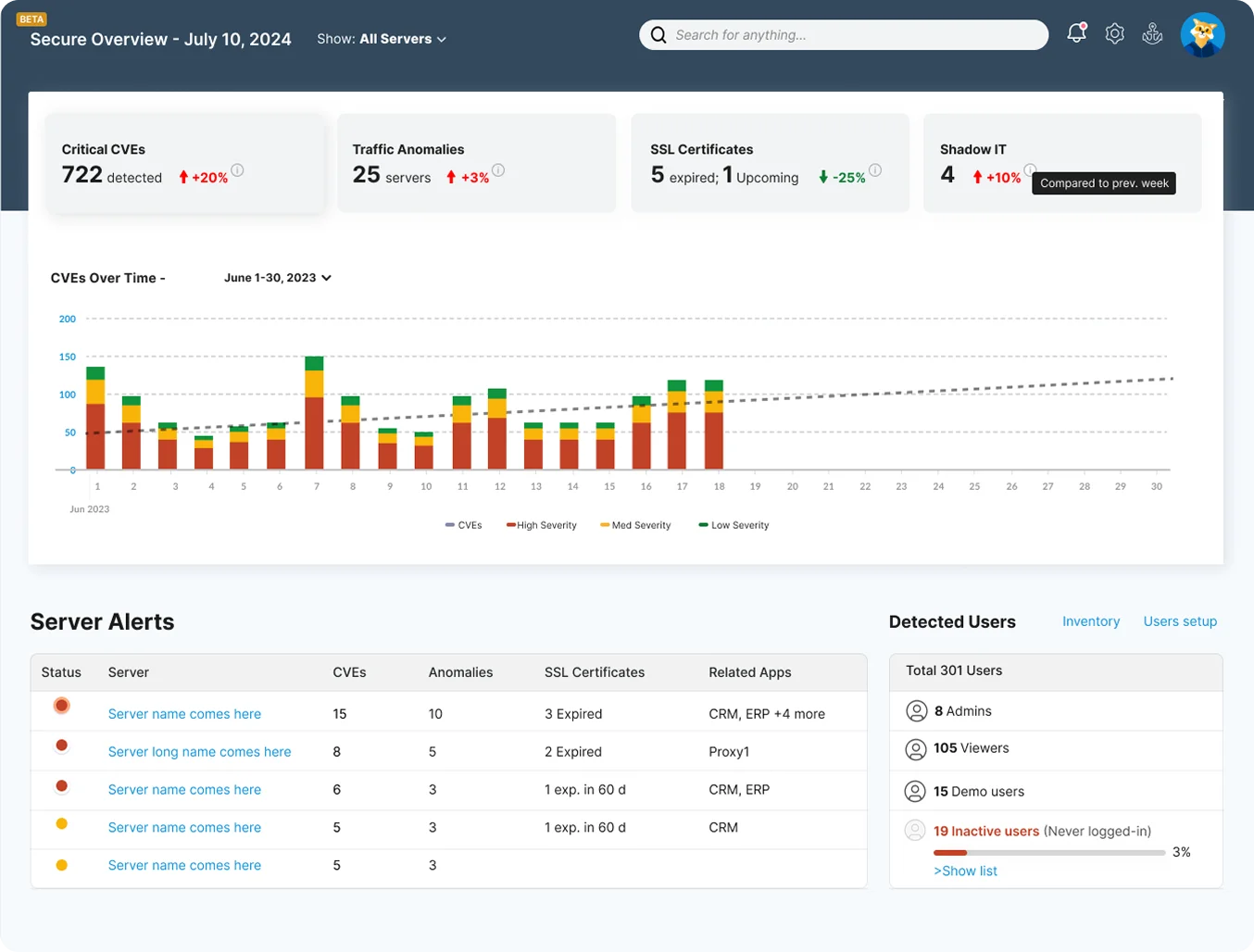
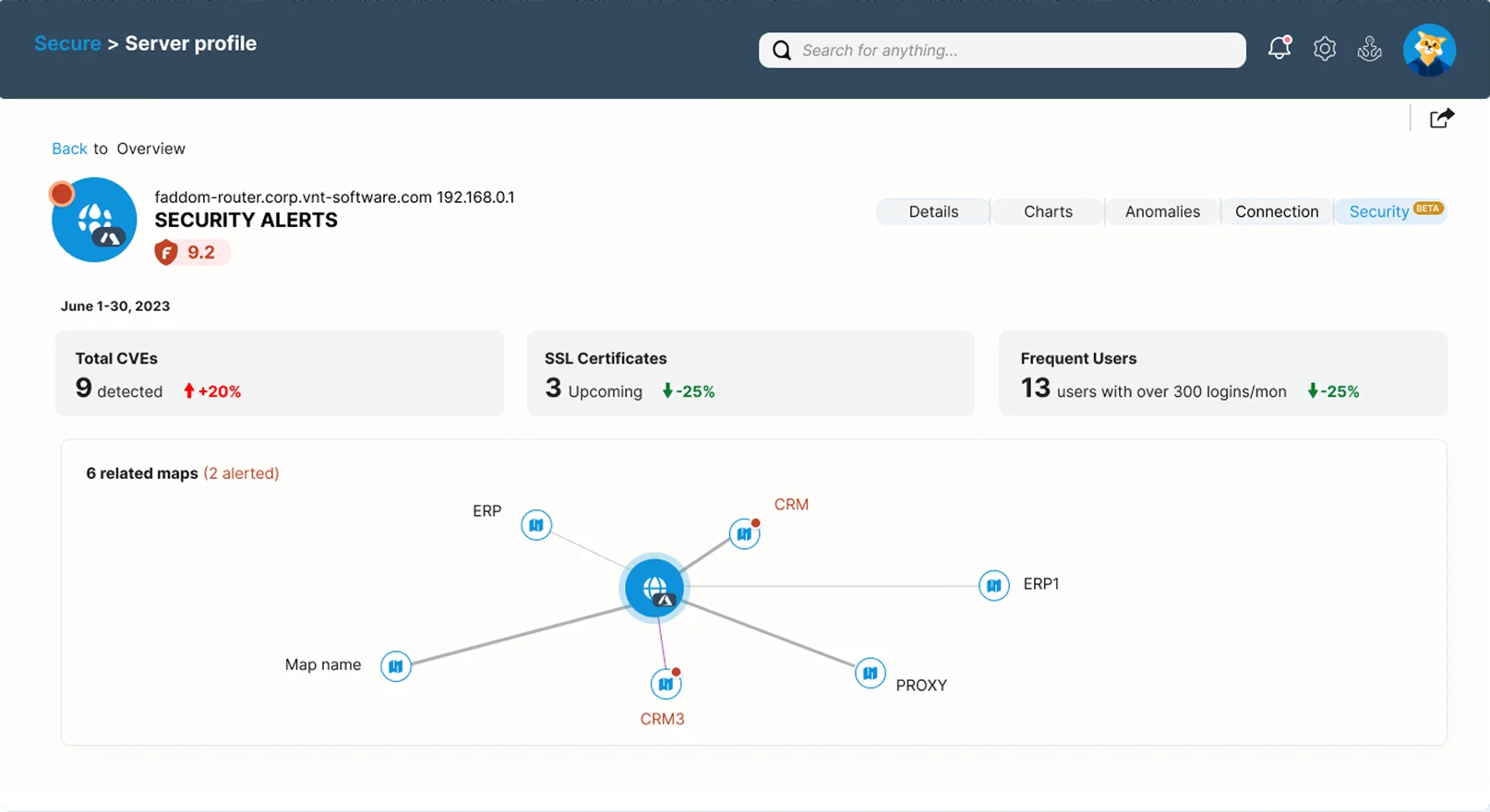
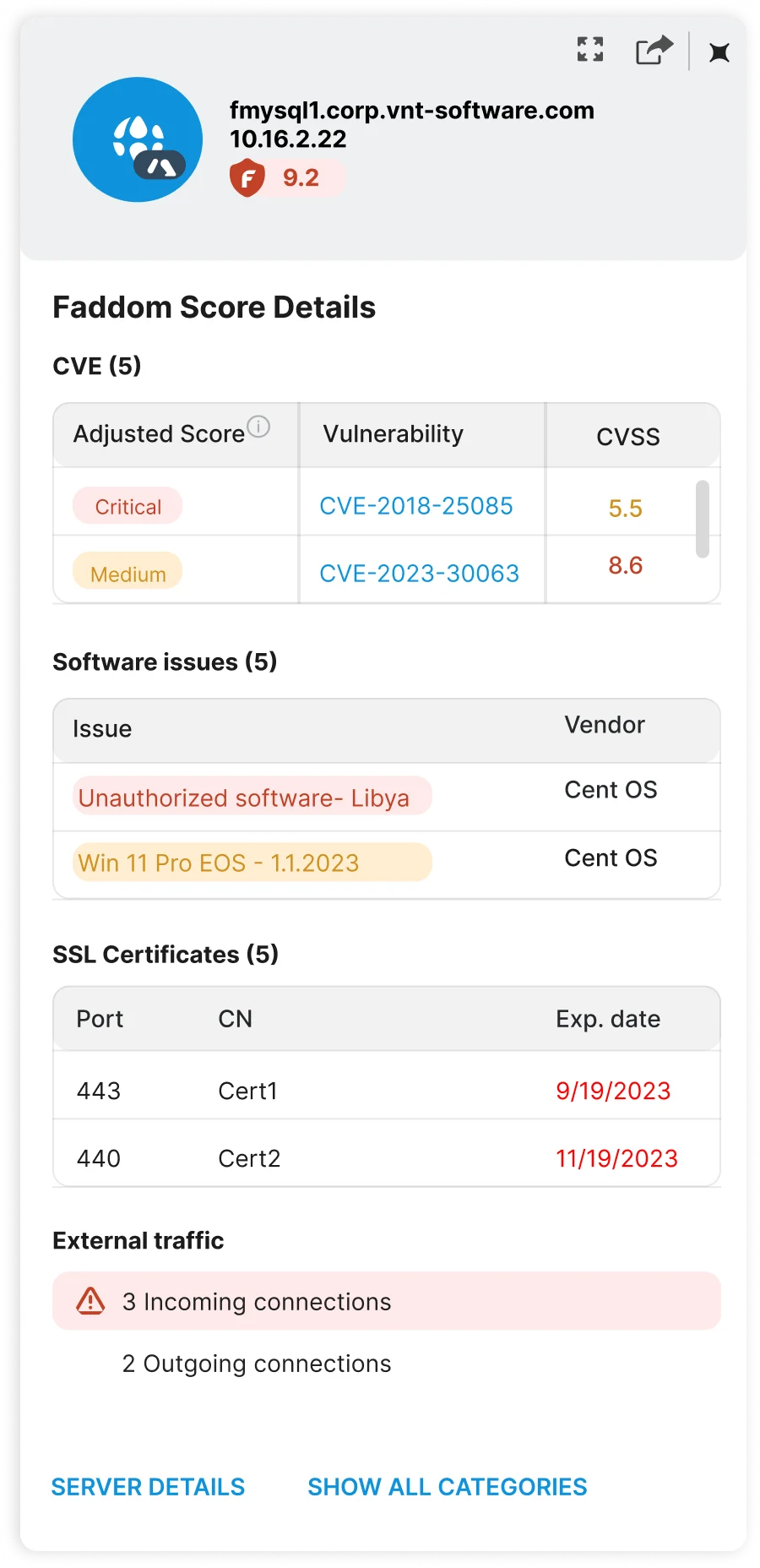
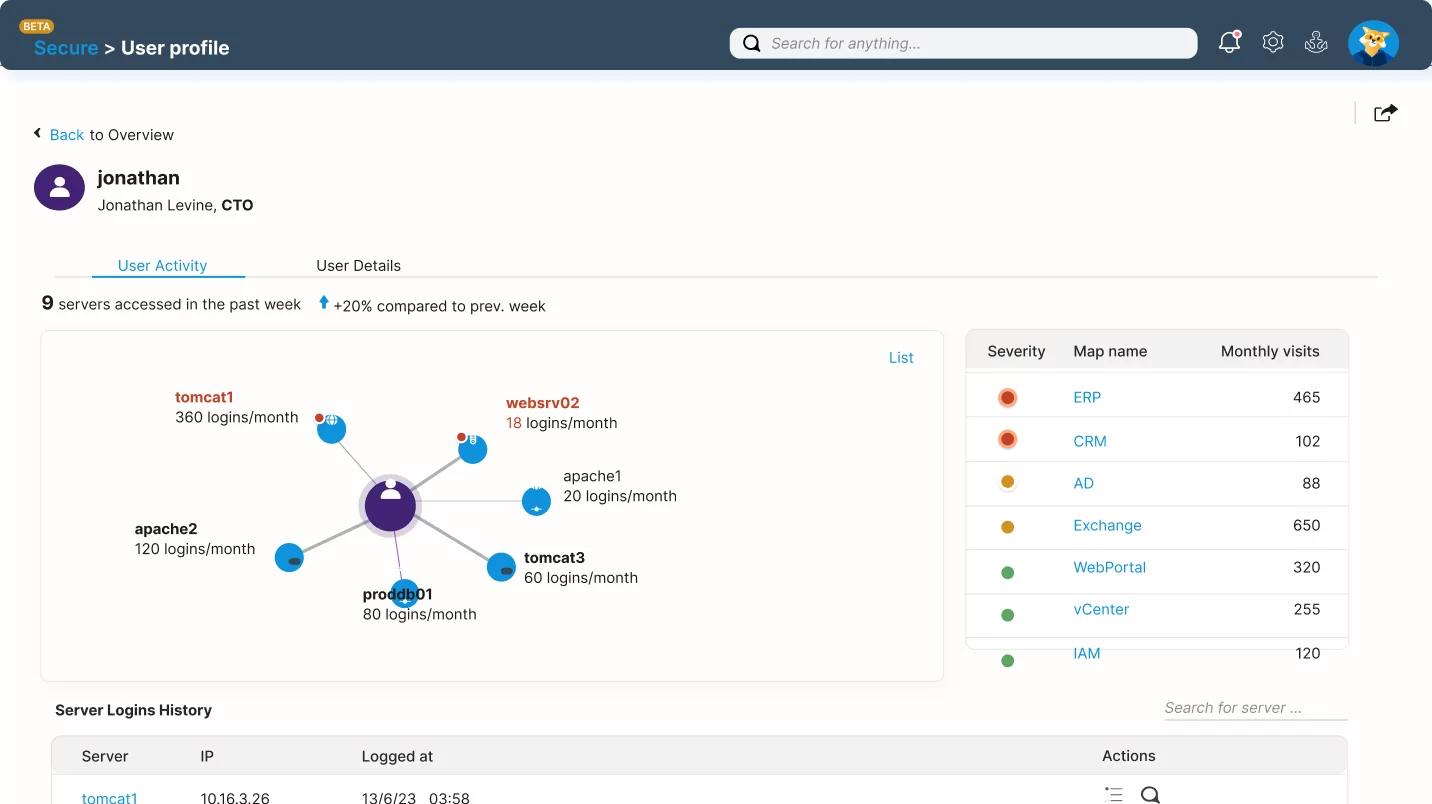
Faddom Delivers Real ROI: Save time, optimize costs, and stay compliant! 📈
- Product
- Faddom AI ✨
- Learn
- IT Academy
- Application Dependency Mapping
- Network Topology Mapping 101
- IT Service Mapping
- Application Migration Best Practices
- IT Documentation: Examples & Best Practices
- Application Assessments: Process and Deliverables
- Application Discovery Challenges and Solutions
- IT Infrastructure Mapping: Process & Tools
- Active Scanning vs. Passive Scanning
- Agentless Scanning vs. Agent-Based Scanning
- Setting up NetFlow in VMware
- Guides & whitepapers
- Complete Guide: Application Dependency Mapping
- IT Mapping in Your Environment
- How to Map a Hybrid IT Infrastructure
- Successful Cloud Migration Plan in 2025
- VMware Migration Playbook
- Disaster Recovery and Business Continuity Guide
- Microsegmentation for IT Infrastructure
- IT Asset Management Best Practices
- Get DORA&NIS2 Compliant by Tomorrow
- Faddom Blog
- IT Academy
- Company
- Customers
- Pricing
- Book a Demo
- 2 min Tour
- GET FREE TRIAL