The business case for migrating to the cloud is compelling, whether creating a hybrid environment by augmenting an on-premises installation with cloud services, or deploying the entirety of IT infrastructure—data, servers, applications, and assets—to one or more clouds. Moving to the cloud enables companies to maintain a competitive edge and respond quickly to market fluctuations. Building a multi-cloud architecture can extend these benefits.
This blog post examines the potential advantages and drawbacks of multi-cloud architectures—not only for the migration process but the day-to-day operation and management.
Table of Contents
ToggleThe Benefits of Multi-Cloud Architecture
Adopting a cloud infrastructure provides agility, scalability, and cost efficiency. It can help companies improve compliance and governance, as well as provide speedy application development and better application performance—especially when deploying cloud-native applications.
However, when it comes to the cloud, there is no one-size-fits all solution. Many companies, therefore, choose to implement a multi-cloud architecture, allowing them to create a blend of features from various cloud service providers to best serve the organization’s goals and needs.
This section explores the main benefits multi-cloud architecture solutions can offer.
1. Flexibility
The ability to use different cloud service providers offers greater flexibility and allows companies to take advantage of each of the provider’s strengths. For example, AWS may provide scalable computing resources and tools for data analytics; while Microsoft Azure can be used to support Windows workloads and integrate with the Bard AI engine. Companies planning to move toward containerization and Kubernetes might choose to add Google Cloud Platform to the mix as well.
2. Cost Reduction and Scalability
Success can be a double-edged sword. As a business grows, the burden on computing infrastructure increases as well. Offloading the purchase and maintenance of hardware to a cloud service provider can provide a great savings. Implementing a multi-cloud architecture allows businesses to take advantage of competitive pricing from different cloud providers and choose the most cost-effective service for their specific requirements.
Analyzing the overall cost benefits of the cloud, however, is no trivial task, and customizing a mix of services depends greatly on a business’ specific needs. As an example, a vendor that provides attractive pay-as-you-go (PAYG) pricing to allow elastic scaling capabilities to accommodate fluctuating demand may not be the best fit for hosting applications or processing large amounts of data.
3. Business Continuity and Disaster Recovery (BCDR)
It is the nightmare of any business to suffer a server crash or to go dark when a data center goes down. The natural solution is redundancy: duplication of critical services and assets. If the working version is lost, the backup takes over in a minimal amount of time.
Multi-cloud architecture provides an ideal solution to BCDR, since critical resources, data, and applications can be backed up in multiple clouds—preferably in geographically diverse regions—to reduce the risk of service disruption caused by a single point of failure or a local natural disaster.
The Challenges of Multi-Cloud Architecture
Many of the benefits provided by a multi-cloud architecture are accompanied by their own challenges to meet and overcome.
1. Security
Regardless of the computing environment, security against increasingly sophisticated attacks continues to be a daunting task. While it is true that the success of every cloud service provider depends on anticipating potential threats, mounting a defense, and speedily restoring full service, the protection provided by this kind of “herd immunity” only goes so far. Applications with security vulnerabilities, such as code injection or cross-site request forgery attacks, must be addressed by the developer before deployment, monitored during use, and patched, as necessary, if vulnerabilities are discovered.
Perhaps one of the greatest challenges to security in a multi-cloud architecture is acquiring the requisite in-house skills to understand and manage the features offered by each cloud provider. According to Valtix, while 95% of organizations are prioritizing multi-cloud architecture in 2023, only 58% feel confident that they can support multi-cloud security.
2. Vendor Lock-In
Many cloud service providers use customized data formats, specialized applications, proprietary code for APIs, or dependency paths that are specific to the structure of that particular cloud environment. Vendor lock-in can make it difficult to duplicate—or migrate—workflows to another cloud.
It is important to carefully analyze the degree of possible vendor lock-in in a current or prospective cloud service to better anticipate the future cost and effort of migration.
3. Maintaining Full Visibility
It can be challenging to monitor cloud resources, optimize cloud usage, and troubleshoot problems in an ever-changing dynamic environment—and a multi-cloud architecture can add to this complexity.
Every cloud provider has its own dashboard or management console—along with its own APIs and tools to integrate into the organization’s IT system—each of which demands scaling and has its own learning curve.
Multi-cloud also increases the risk of shadow IT—when systems, devices, software, applications, or services are being used within the organization without explicit IT department approval. This can result in lack of visibility and therefore increased security risk.
Planning for the Cloud
Whether planning for cloud migration, moving assets from one cloud to another, or adding another cloud service to the computing architecture, preparation is key.
This should be broken down into several steps.
1. Discovery
It is crucial to inventory all existing technological assets, applications, and services—which may number in the hundreds or thousands—to gain a complete understanding of the entire workload of each application, including storage requirements, networking needs, and dependencies.
Such an inventory must also include information about asset ownership, its current use, how much it costs, specifics about licenses and renewals, end-of-life and end-of-service details, and other administrative matters.
2. Assessment
Once discovery is complete, every asset must be assessed for suitability for the cloud, along with an evaluation about the level of effort required for a successful migration.
It is crucial to understand that different cloud providers are not interchangeable; even an open-source technology such as PostgreSQL is likely to have been modified to work better with a particular cloud service. This means that moving a database from one cloud to another may require some degree of rearchitecting. Moreover, migrating from an on-premises installation to the cloud cannot be done without some measure of time, expertise, and testing.
However, some legacy applications can continue to be used as is, on-premises, or by hosting them in a virtual machine on the cloud. While these solutions are quick and inexpensive, they provide no benefit in customer experience or efficiency.
Other legacy applications can be refactored: rearchitecting the code to use the features of the cloud environment. Others can be replatformed: leaving core architecture unchanged, but making necessary modifications for it to work in the cloud.
The effort to migrate some legacy applications, however, may be extensive, and it may be more cost effective to replace them with an agile and scalable SaaS that provides all of the benefits of cloud-native services—out of the box.
3. Prioritization
Based on the assessment of applications and assets, a prioritization work plan should be established. This should include which applications and services to move and which cloud service should host them. However, despite the best discovery and assessment, there are no guarantees that everything will go as planned, and it is important to minimize any possible disruptions due to miscalculations or errors.
Among the issues to consider are starting with applications and services with low complexity—those with minimal impact on the business—and scheduling internal-facing applications before customer-facing applications. Business realities may also influence prioritization; certain times of year may be best to initiate a major change.
The prioritization plan is not an all-or-nothing process. It may be best to continue to use a legacy application on-premises until it can be phased out when a cloud-native alternative has been deployed and tested.
4. Migration
Every cloud migration is specific to the source and target infrastructure, and it is implemented by each IT department according to its own professional standards and governed by company policies. However, there are a number of common guidelines for a successful cloud migration:
- Before migration, ensure that technology asset management tools are in place to manage cloud-based workloads.
- Prioritize less-critical applications so IT can build expertise and skills in the new cloud environment.
- Migrate workloads during non-business hours to avoid downtime.
- Migrate manageable chunks and test-drive them to ensure optimal performance and check for unforeseen problems.
Managing Multi-Cloud Architecture
In a multi-cloud architecture, IT requires visibility of the entire hardware and software infrastructure, including every asset, service, dependency, license, and configuration.
It is well known that documentation invariably lags behind development and deployment, so complete visibility is often lacking. Even a cloud service that provides discovery tools for mapping application resources does not see on-premises assets and cannot scan other cloud service providers.
A thorough understanding of what exists in infrastructure is required for successful migration, and afterward, to ensure reliable operation and management.
Whatever method is used to gather and compile information, visibility is required in the following areas:
1. Application Dependencies
Application dependency mapping (ADM) identifies and clarifies how all microservices, functions, subroutines, and integrations work together with other systems.
Such dependencies include in-house codebases, libraries and frameworks, proprietary software, files and database systems, underlying operating systems, servers and subnets, drivers, and specific versions of scripting languages.
Mapping all application dependencies is crucial to ensure that installing a new application or service—or making changes to existing applications—will not fail due to dependency issues that were not previously located and planned for.
2. Configuration Management
A configuration management database (CMDB) stores information related to all IT assets—hardware, devices, software, and networks—including their performance, configuration, location, licensing, and maintenance data.
Without a CMDB, it is difficult for a business to make informed IT decisions about problem resolution or incident response. This also makes it hard to evaluate where networks and infrastructure need updating, to prepare a good business strategy, plan budgets, or be certain of regulatory compliance.
However, maintaining a CMDB as a single source of truth for IT assets across every environment is challenging. IT environments are constantly changing, and even modern CMDB systems may only collect data based on a specific request or have a limited ability to see all changes in dependencies and services, hindering root cause analysis.
3. Application Performance
Application performance monitoring (APM) is designed to ensure that all applications across an organization’s application portfolio meet performance and reliability requirements. Real-time diagnostics and performance alerts can pinpoint problems within the application stack and help plan proactive remediation.
Many APM tools, however, require the installation of an agent for targeted infrastructure or specific applications. This can limit the effectiveness of the mapping, since it may be impossible to see real-time performance across dependencies.
Achieving Visibility in Complex, Multi-Cloud Environments
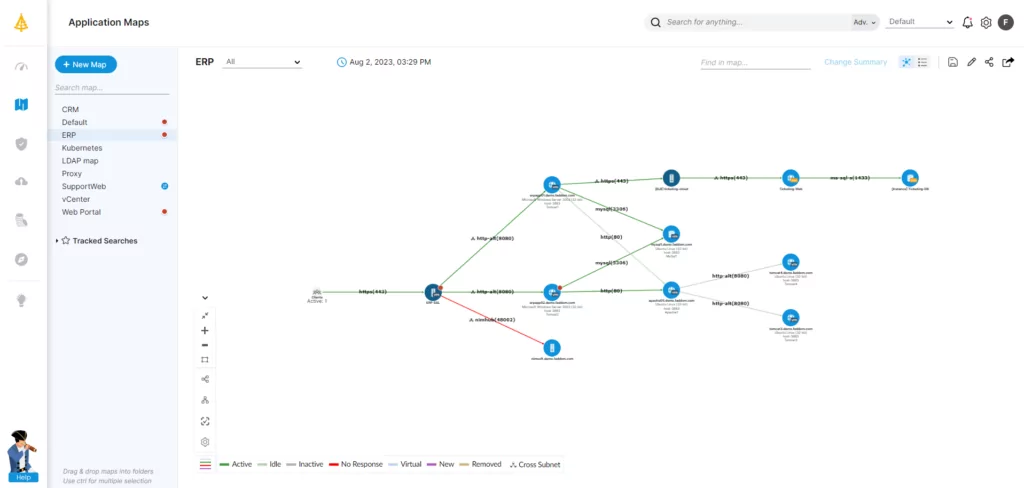
An increasing number of companies are adopting a multi-cloud architecture, looking to take advantage of the flexibility, cost savings, and improved performance it offers. Planning ahead is of great value: Many businesses have adopted a policy to rely on open-source services and platform agnostic applications to facilitate future cloud migrations and avoid—as much as possible—vendor lock-in.
Ensuring full visibility is key, but organizations often lack the necessary resources and expertise within the IT team. Automated tools can offer visibility into complex IT infrastructure and multi-cloud architectures. By searching the entire environment—including all interconnections and dependencies—the right tools will be able to identify shadow SaaS, incompatible applications and dependencies, and underutilized assets. These tools can also map network topology, physical network devices, help optimize license use, and continuously document all business applications.
An ideal application dependency mapping tool should traverse a multi-cloud architecture—in real time—to identify and map all instances, communications channels, applications, ports, services, VPCs, subnets, and security groups being used in an IT ecosystem across every cloud.
The benefits to multi-cloud architecture are attractive, and though the challenges are real, they can be met—and overcome—with planning, preparation, and the proper tools. Visualize your on-premises and cloud infrastructure with continuous, automatic updates—in as little as 60 minutes—with Faddom’s agentless, hybrid application dependency mapping tool. Start a free trial today!









