What Is Disaster Recovery Software?
Disaster recovery software helps organizations restore critical systems and data after events like hardware failures, cyberattacks, natural disasters, or accidental data deletion. Its main goal is to ensure business continuity by minimizing downtime and data loss.
With the increasing dependency on digital infrastructure, disaster recovery solutions are essential parts of modern IT strategies for organizations of all sizes. Unlike basic backup tools, disaster recovery software typically automates failover processes, orchestrates system restorations, and ensures rapid resumption of operations.
Table of Contents
ToggleThese solutions may include features for continuous data protection, virtual machine recovery, and integration with cloud infrastructure. The combination of automation, orchestration, and backup capabilities differentiates disaster recovery platforms from standard backup solutions.
Key Components of a Disaster Recovery Software Stack
Orchestration and Automation
Orchestration and automation in disaster recovery remove manual intervention from complex recovery processes, significantly reducing the risk of human error during critical incidents. These features automate workflows such as system failover, VM recovery, network configuration, and application mapping. By embedding runbooks or scripts directly into the software, organizations can respond to disasters consistently and predictably, regardless of pressure or personnel availability.
Automation further benefits testing and validation, which are vital for disaster recovery readiness. Regular, automated drills can simulate disaster scenarios, ensuring that procedures work as expected and that recovery time objectives (RTOs) are met. This approach also accelerates response times by codifying best practices into repeatable actions.
Backup and Replication Engines
Backup and replication engines are the backbone of any disaster recovery strategy. Backup engines create point-in-time copies of critical data at regular intervals, allowing organizations to restore systems to a known-good state following a disruptive event. These backups may reside on-premises, offsite, or in the cloud, providing redundancy in case a primary site becomes compromised.
Replication engines take data protection a step further by continuously or periodically synchronizing real-time data to secondary sites, often with minimal lag. This means recovery points are more current, enabling organizations to resume operations with almost no data loss.
Failover and Failback Capabilities
Failover capabilities enable the swift transfer of workloads and services from a primary to a secondary infrastructure when the original environment becomes unavailable. This process needs to be fast to minimize business disruption and meet strict recovery time objectives. Most modern disaster recovery solutions provide automated failover for critical applications.
Failback is equally important. Once the primary systems or data centers are restored, organizations must safely transition operations back from the recovery site. This process involves synchronizing changes made during the failover period, ensuring no data is lost or overwritten.
Monitoring and Alerting Systems
Monitoring and alerting systems provide continuous oversight of the disaster recovery environment, notifying IT teams instantly of anomalies, failures, or risks. Dashboards, health checks, and real-time metrics ensure visibility into backup success rates, replication status, and potential bottlenecks. Automated alerts enable teams to react quickly, reducing the time required to identify and respond to incidents.
Recovery platforms offer customizable thresholds and integrated escalation policies. This granularity ensures the right personnel are contacted at every incident severity level. Proactive monitoring extends to infrastructure, network, and application health, creating a holistic safety net that improves system reliability and disaster readiness.
Compliance and Audit Readiness
Compliance and audit readiness functions embedded in disaster recovery software help organizations align with regulatory mandates such as GDPR, HIPAA, or SOX. These features generate detailed logs documenting backup and recovery actions, user access, and data movement. Audit trails strengthen accountability and enable IT teams to prove compliance quickly during inspections or reviews.
Regular reporting, policy management, and automated checks help organizations continuously validate their disaster recovery posture. Some platforms allow for the simulation or testing of compliance scenarios, ensuring controls remain effective as infrastructure or regulations change. Integrated compliance tools reduce manual documentation efforts and lower the risk of costly fines.
Notable Disaster Recovery Software
1. Veeam

Veeam’s disaster recovery software offers orchestration capabilities to ensure rapid recovery from disruptions with minimal data loss. It provides automated workflows for system failover, failback, and recovery, allowing organizations to maintain operational continuity during catastrophic events.
Key features include:
- Automated recovery orchestration: Simplifies and automates failover and recovery processes with workflows for business continuity.
- Validated clean recovery: Continuously scans for threats and ensures recovery from the latest clean backup to avoid ransomware impact.
- Automated testing: Conducts non-disruptive recovery tests to validate recovery objectives and ensure systems are ready to meet RTOs and RPOs.
- Dynamic compliance documentation: Generates automatic recovery reports for compliance verification and auditing purposes.
- Cloud recovery: Supports recovery to cloud environments, including direct restores to Microsoft Azure.
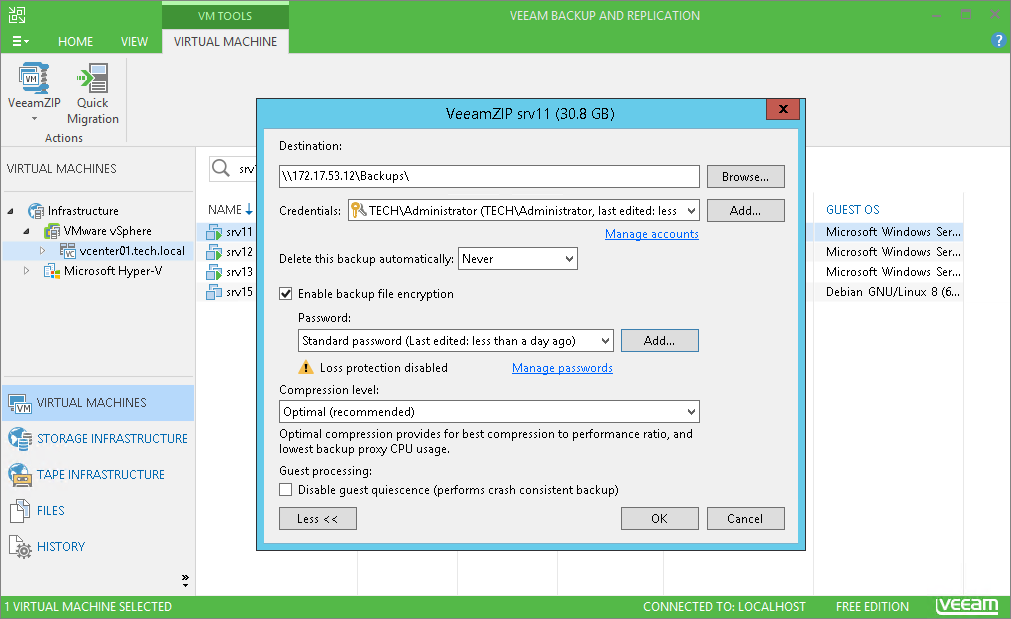
Source: Veeam
2. HPE Zerto

HPE Zerto offers a disaster recovery and continuous data protection solution to minimize downtime and data loss across IT environments. It uses continuous data protection (CDP) technology to ensure that data is constantly replicated, providing organizations with fast recovery point objectives (RPOs) and recovery time objectives (RTOs).
Key features include:
- Continuous data protection: Provides real-time replication to minimize data loss and ensure business continuity.
- RPOs and RTOs: Enables rapid recovery with low data loss, helping organizations maintain operations during disruptions such as cyberattacks or natural disasters.
- Ransomware detection and recovery: Detects encryption attacks and enables rapid recovery using immutable, secure data copies.
- Non-disruptive testing: Allows organizations to test disaster recovery plans without affecting production systems.
- Migration: Supports automated, orchestrated migration of workloads between on-premises and cloud environments.
Source: Zerto
3. Commvault

Commvault offers a disaster recovery solution that integrates forensics and AI to ensure rapid, secure data recovery in the event of a cyberattack or natural disaster. It validates clean recovery points, preventing reinfections and ensuring that only safe data is restored.
Key features include:
- AI-driven automation: Uses artificial intelligence to automate and accelerate the recovery process, verifying clean data points to prevent reinfection.
- Clean recovery point validation: Ensures only safe, uncorrupted data is restored by validating recovery points through AI.
- Cloudburst™ recovery: Enables recovery from cloud environments with AI-driven automation.
- Cleanroom recovery: Provides cloud-based recovery environments with clean backups.
- Cyber resilience integration: Improves cybersecurity by embedding data recovery as a core component.
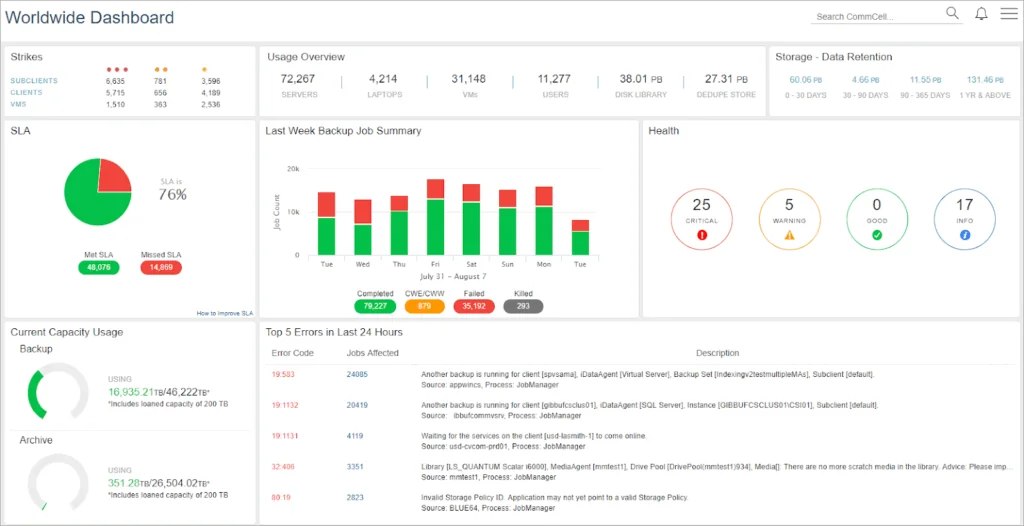
Source: Commvault
4. Rubrik

Rubrik offers disaster recovery solutions for hybrid identity infrastructure, ensuring rapid recovery of Microsoft Active Directory and Entra ID environments. With its focus on cyber resilience, Rubrik helps organizations protect their identity services against ransomware, insider threats, and operational failures.
Key features include:
- Immutable backups: Protects against ransomware and other cyber threats by ensuring that backup data cannot be altered.
- Clean room recovery: Enables secure recovery in isolated environments, reducing the risk of reinfection.
- Unified hybrid identity recovery: Delivers full visibility and recovery orchestration across on-premises and cloud environments, ensuring business continuity.
- Active Directory forest recovery: Simplifies AD Forest recovery with a unified workflow, eliminating manual steps and speeding up the recovery process.
- Granular object-level restoration: Enables quick recovery of individual AD and Entra ID objects such as user accounts and groups, minimizing downtime from accidental deletions or cyberattacks.
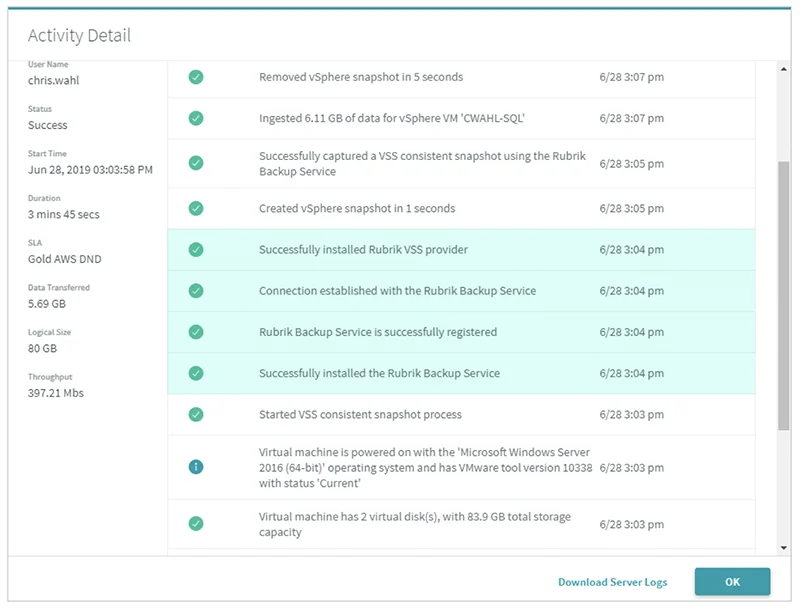
Source: Rubrik
5. Druva

Druva provides an automated cloud disaster recovery solution to protect workloads in AWS and VMware environments. With Druva’s cloud-native platform, organizations can rapidly recover from ransomware attacks and data loss, ensuring minimal downtime with an RTO of minutes and an RPO of an hour.
Key features include:
- One-click cloud recovery: Provides simple, fast recovery for on-premises VMs to AWS with minimal effort.
- Automated disaster recovery testing: Automatically tests disaster recovery plans for Amazon EC2 and RDS environments, ensuring readiness across regions and accounts.
- Failover and failback: Supports quick failover and failback between VMware environments and AWS.
- No hardware or software management: Eliminates the need for managing hardware, software, or additional DR sites.
- Global recovery across AWS regions: Enables recovery of AWS and VMware workloads across any AWS region.
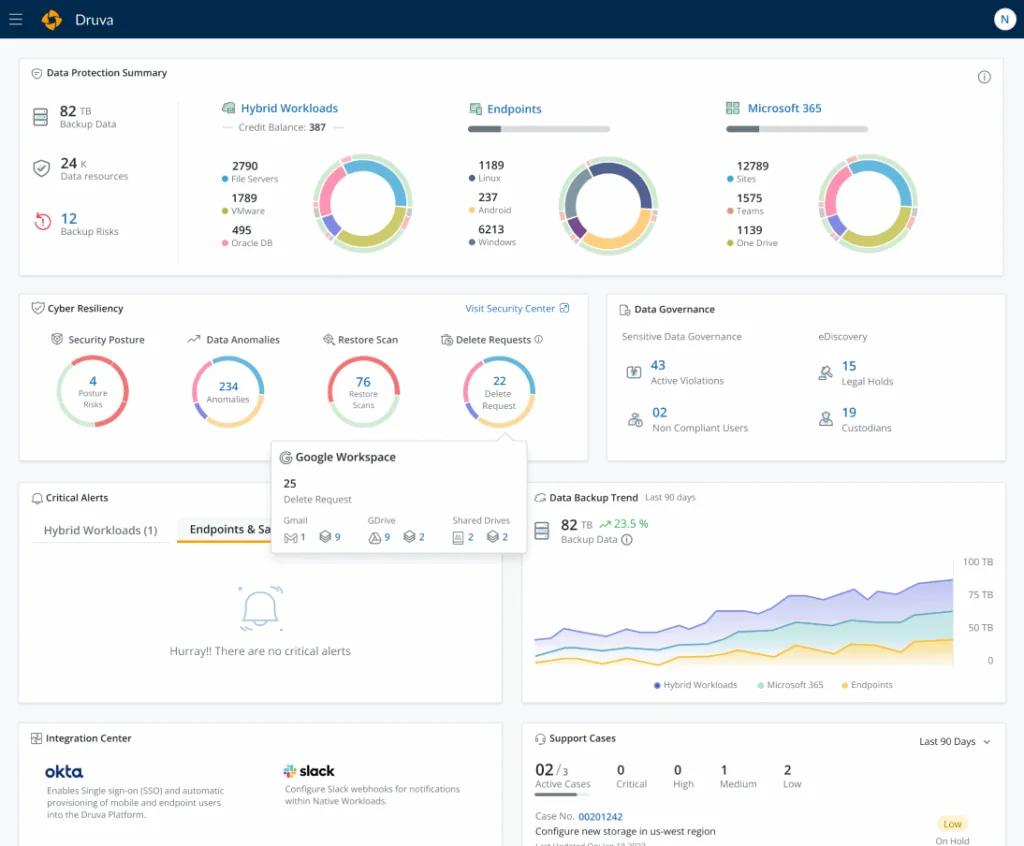
Source: Druva
6. Arcserve

Arcserve offers disaster recovery solutions that minimize downtime and ensure the rapid recovery of critical systems, applications, and data. Designed to protect organizations from cyberattacks, accidental data loss, and system failures, the platform provides protection for both on-premises and cloud environments.
Key features include:
- Disaster recovery: Protects systems, storage types, and applications (e.g., Exchange, SQL Server, Office 365) across physical, virtual, and cloud environments.
- Arcserve replication and high availability: Eliminates downtime with LAN and WAN replication for on-site, off-site, and cloud-based data.
- Data protection: Provides monitoring, data rewind, and automated redirection to prevent sensitive data loss.
- Cloud-native backup as a service (BaaS): Arcserve Cloud Direct offers cloud-native, hardware-free backup solutions.
- Ransomware protection: Incorporates continuous third-party vulnerability scans, SSL encryption, and data rewind features to protect against the impact of ransomware.
Source: Arcserve
7. Acronis

Acronis offers a disaster recovery solution that allows organizations to recover from cyberattacks, outages, and other disruptions. With Acronis Disaster Recovery, organizations can spin up production environments in minutes, without the need for extra hardware. The platform simplifies recovery by using a single console to manage backup and disaster recovery.
Key features include:
- Recovery integration: Enables disaster recovery with the same agent and console used for backups.
- Multi-cloud failover: Provides the flexibility to choose between Acronis Cloud, Microsoft Azure, or hybrid setups for failover.
- Failover to clean recovery points: Ensures malware-free recoveries by failing over to a clean, secure recovery point, preventing ransomware reinfection.
- Automated runbooks: Orchestrates disaster recovery procedures using runbooks, automating failovers and recovery processes to reduce manual effort.
- Physical and virtual workload support: Supports disaster recovery for a range of workloads, including Windows, Linux, and major hypervisors.
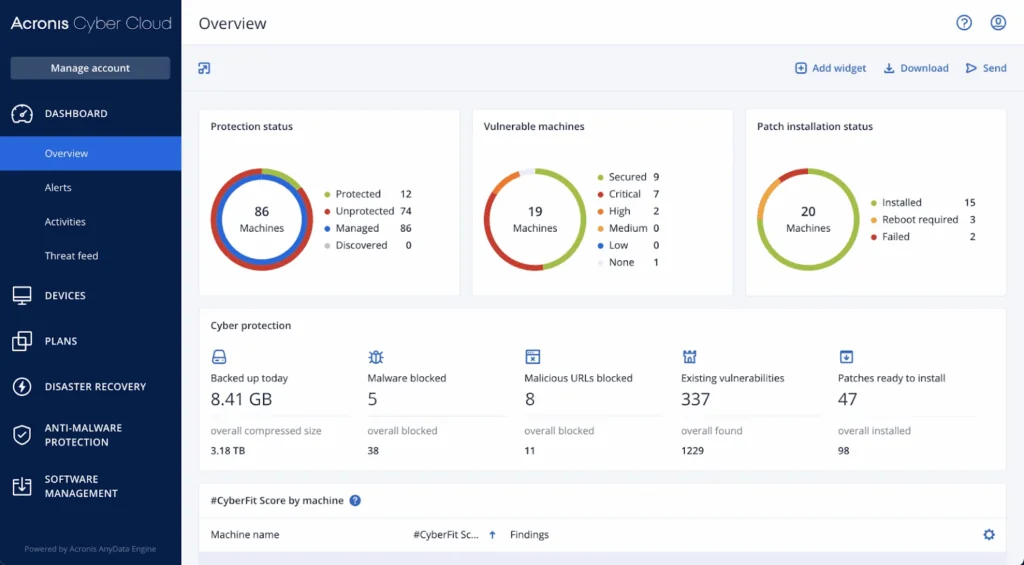
Source: Acronis
Supporting Disaster Recovery with Faddom Dependency Mapping
Disaster recovery goes beyond backups and failover; it requires a clear understanding of how your systems, business applications, and dependencies are interconnected to ensure that recovery plans work effectively when put to the test. This is where Faddom stands out. By continuously mapping all servers, applications, and traffic flows across on-premises, cloud, and hybrid environments, Faddom provides IT teams with the visibility needed to design reliable recovery strategies and avoid overlooked dependencies that can lead to downtime.
With real-time, agentless discovery and continuously updated maps, Faddom eliminates blind spots, ensures that application interdependencies are documented, and helps prioritize critical services for recovery. This context shifts disaster recovery from guesswork to a well-orchestrated and predictable process that adheres to strict Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs). By aligning technical visibility with business continuity goals, Faddom empowers organizations to recover more quickly, reduce disruption, and strengthen resilience.
Schedule a demo today to discover how Faddom can enhance and streamline your disaster recovery strategy!