The idea behind microsegmentation is to segment the enterprise network based on workloads. This type of logical breakdown of workloads allows companies to define appropriate data security policies, security services, and data management based on the use cases and needs of each workload.
The microsegmentation methodology can classify the segments in different ways. Techniques include segmentation by application, environment, process, and user. Different organizations can choose different angles for the segmentation based on their needs and the dominant approaches within their organization. (This is part of an extensive series of guides about information security.)
Table of Contents
Toggle- The Benefits of Microsegmentation
- How Microsegmentation Works
- Types of Microsegmentation
- Tips from the Expert
- Applications and Use Cases of Microsegmentation
- The Challenges of Microsegmentation
- Best Practices for Effective Microsegmentation
- Network Architecture Mapping Made Easy
- Learn More About Microsegmentation
- See Our Additional Guides on Key Information Security Topics
The Benefits of Microsegmentation
The security benefits of microsegmentation cover a large variety of potential problems that enterprises face today.
- Improved Threat Containment: By isolating workloads and applications, microsegmentation limits the lateral movement of attackers within a network. If one segment is compromised, the breach is contained, preventing further damage.
- Granular Security Controls: Microsegmentation allows security policies to be tailored at the workload level. This granularity ensures that security measures are specific and effective for each segment’s unique requirements.
- Enhanced Visibility: With microsegmentation, organizations gain detailed insights into network traffic and application dependencies. This visibility helps identify vulnerabilities and optimize security configurations.
- Simplified Compliance: Microsegmentation makes it easier to align with regulatory requirements by creating isolated zones for sensitive data, ensuring that only authorized users and applications have access.
- Reduced Attack Surface: By limiting communication paths to what is strictly necessary, microsegmentation minimizes the opportunities for attackers to exploit vulnerabilities.
- Flexibility Across Environments: Microsegmentation supports hybrid and multi-cloud environments by providing consistent security policies regardless of the underlying infrastructure.
How Microsegmentation Works
Microsegmentation works by identifying segments in a logical way. Rather than looking at a specific data center, server, or hyperscaler, microsegmentation identifies data flows and functional segments of an enterprise’s operations.
When implemented effectively, microsegmentation creates protected areas within the data centers or across data centers. These protected areas represent a specific function, application, or group that can be trusted internally. Each one of these microsegments is isolated from other areas of the data center, which means that if malware affects one area of the data center, the contagion is limited to that specific microsegment.
By containing a threat, microsegmentation provides a safer overall enterprise environment, minimizing the potential damage that can be done by any one breach of security. This proactive approach to security not only reduces risk but also enhances compliance with industry regulations and fosters greater trust within the organization, as sensitive data and critical systems remain safeguarded against lateral attacks.
Types of Microsegmentation
To illustrate how microsegmentation works, it can be helpful to examine the four subcategories of this practice, each of which presents different benefits and shortcomings.
Environment-Based Microsegmentation
Environment-based microsegmentation focuses on where the data is stored and access to the network. The environment-based approach differentiates between development, testing, and production environments. It can be quick to implement, using data management tools that identify the types of data stored in each environment. The downside of environment-based microsegmentation is that it doesn’t consider the actual workflows. Also, it doesn’t identify the software or API accessing the different network segments, so it provides less protection than application-level segmentation (discussed below). Finally, environment-based microsegmentation is static and requires more maintenance overhead compared to other microsegmentation approaches as business processes change.
User-Based Microsegmentation
User-based segmentation focuses on the endpoints to delineate workflow behavior. Microsegmentation based on users can be easier to implement because it does not require any infrastructure changes. However, it does not provide the highest level of protection because of the potential for infiltration to a user’s account, and situations in which an employee or contractor takes malicious action. User-based microsegmentation may also fail to identify cases where a user is regularly accessing data they don’t actually need, because security protocols generally work based on anomalies, which may not be obvious when analyzed on the basis of a particular user’s activity.
Application-Based Microsegmentation
Application-based microsegmentation focuses on the application, which means that the segment includes the data and services used by a particular application. To identify application flows, tools such as network sniffing can follow the logic of how the data flows within an application, including the ways in which the application accesses data from other services. Generally, application-level segmentation focuses on the applications which have the most exposure to sensitive data.
A more granular approach is application tier-level segmentation, which divides workflows by roles, separating tiers such as web apps, load balancer, data, and APIs. This approach passes only the minimum required data between microsegments.
Instead of using IP addresses and VLAN affiliations, microsegmentation tags the resources that host the workloads and applications. When applications are updated, policy changes are automatically propagated across the different resources serving those applications, instead of needing to be implemented on a location-based individual basis.
Nanosegmentation
The most granular form of microsegmentation is process-based nanosegmentation, which segments based on the processes within workloads. This level of segmentation is generally applied only to the most sensitive applications within a network. More information can be found in microsegmentation guide and our beginner’s guide to microsegmentation as well as our answer to “What is SNMP?“.

Lanir specializes in founding new tech companies for Enterprise Software: Assemble and nurture a great team, Early stage funding to growth late stage, One design partner to hundreds of enterprise customers, MVP to Enterprise grade product, Low level kernel engineering to AI/ML and BigData, One advisory board to a long list of shareholders and board members of the worlds largest VCs
Tips from the Expert
In my experience, here are tips that can help you better adapt to the topic of microsegmentation:
-
Start with a comprehensive inventory
Conduct a thorough inventory of all assets, applications, and data flows in your network. This baseline is crucial for identifying what needs to be segmented and ensuring all critical elements are accounted for.
-
Implement adaptive segmentation
Use dynamic policies that can adapt to changes in the network environment, such as new applications or changes in user roles. This helps maintain security without requiring constant manual updates.
-
Leverage behavioral analytics
Incorporate behavioral analytics to monitor and understand normal traffic patterns. This allows you to detect anomalies and adjust microsegmentation policies proactively.
-
Combine with endpoint security
Integrate microsegmentation with robust endpoint security measures to provide comprehensive protection against threats originating from compromised devices.
-
Use encryption within segments
Encrypt data not only between segments but also within each segment to add an extra layer of security against internal threats.
Applications and Use Cases of Microsegmentation
Segmenting Dev / Test / Production
The most obvious and straightforward implementation of microsegmentation is the creation of separate segments for development, testing, staging, and production systems in software development environments. At the development stage, software can be more vulnerable to attack compared to software that has been deployed and battle tested. Separating these systems creates a clean environment for the live software.
Segmenting Based on Asset Sensitivity
Another area where segmentation is useful is in identifying and differentiating from one another sensitive materials (soft assets), such as customer data, financial data, and intellectual property. Companies moving towards microsegmentation should start by identifying the most tempting processes for malicious actors, and setting up the security policies for the relevant workflows that handle sensitive data.
Segmenting in Hybrid Environments
Network microsegmentation offers a boost for any hybrid cloud environment by creating a more logical representation of how the cloud is being used, rather than visualizing based on vendors and the location of the clouds. Applications typically access multiple cloud resources and data centers. Setting security policies based on an application-oriented microsegmentation mapping is an effective way to implement a uniform policy across multiple environments, based on the actual usage of the data. This type of policy improves the efficiency of the company by implementing more stringent policies only where they are necessary.
The Challenges of Microsegmentation
Microsegmentation offers powerful benefits, but comes with its share of drawbacks and implementation tradeoffs.
- Mapping the communications flows for each application and user to be segmented. Documentation of these processes requires heavy lifting in the form of expertise, time, and money—which is why most companies turn to automated tools for mapping their communications flows.
- Granular segmentation provides better security but takes more time to implement. High levels of microsegmentation can require specific security policies on a per-user or per-device basis, which is not just time consuming, but can lead to internal resistance or debates about departments’ capabilities and roles assigned to people. If poorly implemented, employees may be impaired in their ability to do their job due to restrictions on their access to company resources.
- Compatibility issues if segmentation needs are difficult to impose on the existing infrastructure. In such a case, implementation may also include some form of cloud migration. Even for networks that are well-suited for microsegmentations, reconfiguration and architecture changes on the network takes a large amount of time and effort. Needless to say, re-architecting and configuring the network comes with implementation costs.
- Microsegmentation increases network complexity. By definition, the security team will be dealing with a large number of security policies applied to different applications, users, and environments. With this increased complexity come increased overheads. Improved security and transparency can lower overall costs once microsegmentation is fully implemented, but there may be an initial period of adjustment before the savings are seen.
Best Practices for Effective Microsegmentation
1. Understand Your Environment
Before implementing microsegmentation, it is essential to have a complete understanding of your network’s architecture. Start by conducting a comprehensive inventory of all applications, devices, data flows, and users. Map out how traffic moves across the network, identifying dependencies between components and connections to external resources such as third-party APIs or cloud services.
Use tools like network discovery and flow analysis to visualize the topology and uncover patterns that are not immediately apparent. Pay special attention to high-risk areas such as applications that handle sensitive data or devices with known vulnerabilities. This step should also involve categorizing assets based on their function, sensitivity, and risk level.
By documenting these insights, you can create an accurate baseline that will guide the segmentation process. Failure to properly understand the environment could lead to misconfigurations that disrupt workflows or leave critical vulnerabilities unaddressed.
2. Start Small and Expand
Microsegmentation is complex, so it’s wise to start with a pilot project rather than trying to overhaul the entire network at once. Focus on a small, high-priority area, such as an application containing sensitive customer data or a frequently targeted service. This controlled approach allows you to develop a repeatable framework, refine your policies, and troubleshoot potential challenges in a less risky environment.
During the pilot, monitor the performance of your segmentation strategy closely. Validate whether the policies effectively limit access without impeding legitimate workflows. Gather feedback from stakeholders, including IT teams and end users, to identify gaps and ensure that your implementation balances security and usability.
Once the pilot succeeds, use the insights gained to expand microsegmentation gradually. Prioritize other critical areas, such as production environments or systems with high regulatory compliance requirements, before extending to less critical segments. This incremental approach reduces disruption and builds confidence in the process.
3. Use a Zero Trust Approach
A zero trust approach to microsegmentation assumes that no user, device, or application is inherently trustworthy, even within the network perimeter. Implement strict access controls for every segment, requiring explicit permissions for any communication to occur. This approach ensures that even if a segment is breached, the attacker cannot move laterally to other parts of the network.
The principle of least privilege is central to zero trust. Each user, device, and application should only be granted the minimum level of access necessary to perform its function. For example, a web application server should only communicate with its associated database and load balancer, and not with other unrelated systems.
To enforce this, adopt granular security controls such as multi-factor authentication (MFA), session-based access permissions, and continuous monitoring for anomalies. Zero trust policies are especially critical in hybrid and multi-cloud environments where traditional perimeter defenses are insufficient. By embedding zero trust principles into microsegmentation, you can significantly reduce your risk exposure.
4. Use Identity-Based Policies
Traditional microsegmentation methods often rely on static identifiers like IP addresses, VLANs, or subnets to define policies. However, in modern environments with dynamic workloads, these methods can be inflexible and error-prone. Instead, use identity-based policies tied to attributes such as user roles, device profiles, or application identities.
For example, policies can be configured to allow only authorized users in the HR department to access employee records or restrict communication between applications based on their verified identities. This approach ensures that policies remain consistent across different environments, whether the workloads are on-premises, in the cloud, or in a hybrid setup.
Identity-based policies are also easier to adapt to changes in the network. For instance, if a user changes roles or an application is updated, the policies can adjust automatically without requiring manual reconfiguration. By leveraging identities, you can enforce security in a more dynamic and scalable manner.
5. Automate Policy Management
As networks grow, managing microsegmentation policies manually becomes impractical. Automation is essential for maintaining consistency, reducing errors, and responding quickly to changes. Automated tools can handle tasks such as creating and enforcing policies, detecting anomalies, and updating configurations when new workloads or devices are added.
For example, when a new application is deployed, automation tools can automatically classify it, assign the appropriate security policies, and propagate those policies across the network. Similarly, when vulnerabilities are detected, automation can isolate affected segments to contain the threat while security teams investigate.
Automation also makes it easier to integrate microsegmentation with other security practices, such as endpoint protection or threat detection systems. By eliminating the need for constant manual intervention, automation improves operational efficiency and ensures that policies remain aligned with the organization’s security objectives.
6. Leverage Mapping and Visibility Tools
Visibility is the foundation of effective microsegmentation. Without a clear understanding of how data flows through your network, it’s impossible to implement or maintain meaningful security policies. Visibility tools provide deep insights into application dependencies, traffic patterns, and potential vulnerabilities, enabling you to design segmentation strategies based on real-world usage rather than assumptions.
For instance, monitoring tools can reveal unexpected data flows, such as an application accessing resources it shouldn’t or unusual communication between segments. These insights can help you identify misconfigurations, detect threats, and refine policies over time.
In addition, visibility tools can help with compliance reporting by providing detailed documentation of data flows and security controls. For example, auditors may require proof that sensitive customer data is only accessible to authorized personnel. Visibility tools make it easy to generate this type of evidence, reducing the administrative burden on security teams.
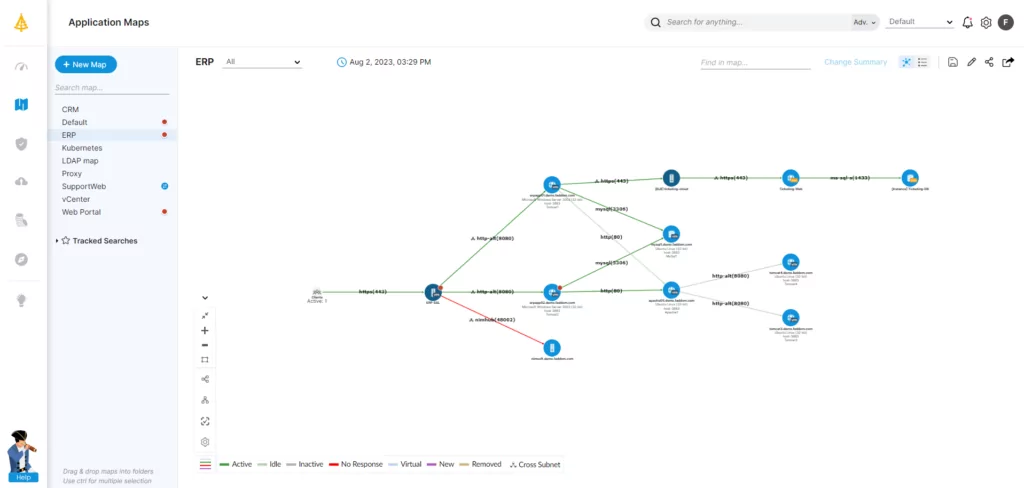
Network Architecture Mapping Made Easy
The foundation of successful microsegmentation starts with understanding your network architecture—both on-premises and in the cloud. This is where Faddom makes all the difference.
With our agentless, automated network mapping technology, you gain instant visibility into your infrastructure, including applications and their dependencies. Faddom helps you:
- Accelerate microsegmentation projects by providing a clear and dynamic map of your current environment.
- Reduce guesswork with real-time, accurate insights into data flows and traffic patterns.
- Save time and resources with a deployment process that takes less than 60 minutes.
Get started today with a free trial and see how Faddom simplifies the path to effective microsegmentation and beyond.
Learn More About Microsegmentation
How Network Microsegmentation Can Protect Data Centers
Cloud migration comes with challenges, but sound strategy and planning will help overcome these obstacles in order to reap the benefits.
Read more: How Network Microsegmentation Can Protect Data Centers
A Beginner’s Guide to Network Microsegmentation
Those who might move to the cloud must start with full visibility of their applications and dependencies to get it right the first time.
Read more: A Beginners Guide to Network Microsegmentation
A Beginner’s Guide to Understanding Microsegmentation
Let’s take the complexity out of application migration. Here’s common approaches, and the application migration that they suit.
Read more: A Beginner’s Guide to Understanding Microsegmentation
What is SNMP?
Cloud implementation gives your organization an edge. Moving workload from on-premises to cloud is convenient and cost-effective.
Read more: What is SNMP?
How to Check SSL Certificates on Servers
What Is data center migration? Learn about the benefits, types of migrations, and best practices for migrating to a new data center.
Read more: How to Check SSL Certificates on Servers
VMware Networking Basics
Cloud trends to look out for in 2023: What you need to know about cloud computing, technology adoption, and market trends.
Read more: VMware Networking Basics
An Introduction to Network Address Translation
Migrating data between locations or applications? Here’s what you need to think about when starting a new data center migration project.
Read more: An Introduction to Network Address Translation
See Our Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
User Management
Authored by Frontegg
Information Security Core Concepts
Authored by Exabeam
Disaster Recovery Guide
Authored by Cloudian