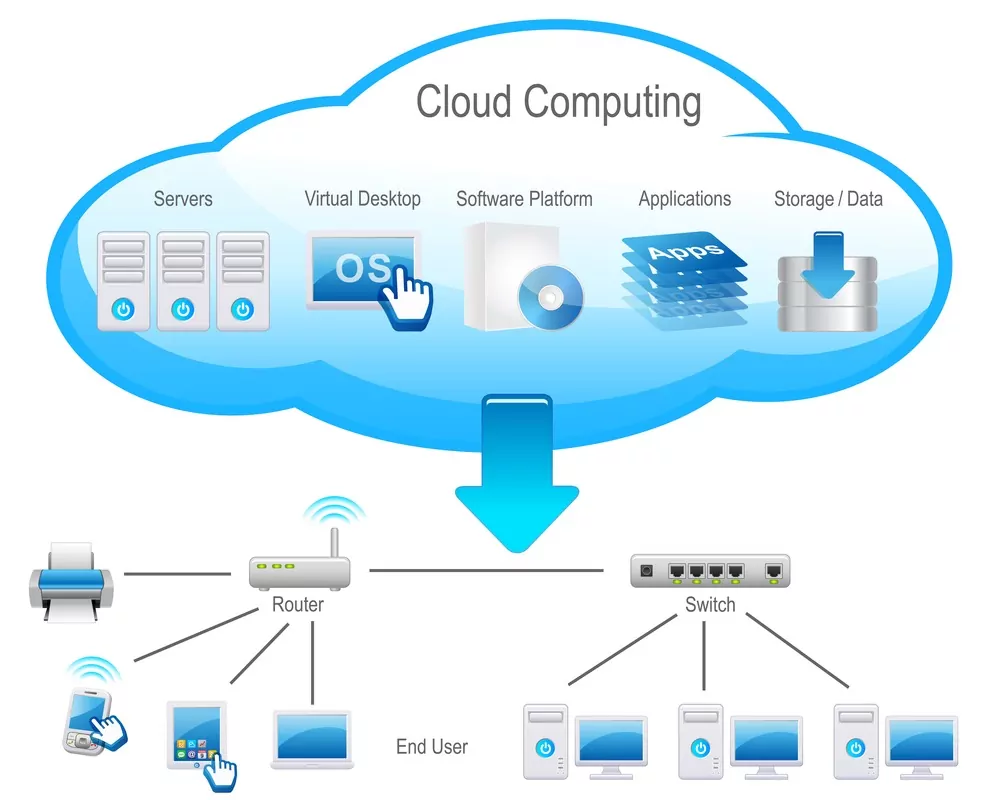
What is Micro segmentation?
Micro segmentation and network microsegmentation is a foundational security strategy for any complex data center in today’s increasingly digital world. If you’re not sure what micro segmentation is, and how you could benefit from it – consider this your micro segmentation for dummies cheat sheet.
Table of Contents
ToggleWhy Do Companies Need Micro Segmentation Solutions?
Traditionally, the perimeter firewall was the hero of the data center. It was like the guard and the moat on the outside of a castle, making your network an impenetrable fortress. Traffic would travel North-South in and out of your network, and it could only enter if it had the right permissions. Simple.
Since the advent of the cloud, things have become a lot less simple. Many security experts believe that the traditional perimeter is dead, and they’re right – it is. The vast majority of traffic is no longer going North-South, it’s travelling East-West, that is – inside the data center itself. Going back to our castle analogy, it’s like the guard standing point outside the door, while the intruders are already moving around inside. This traffic is made up of third-party cloud services, software, BYOD, and more. On the cloud, microsegmentation is more important than ever. (For more information, see our Guide to Microsegmentation.)
This is part of a series of articles about IT Mapping
How Does Network Microsegmentation Help?
Microsegmentation is about protecting what’s inside your network from attacks that could already be inside, or have the power to move East-West, and won’t be stopped by your perimeter firewall. The concept is simple, you segment parts of your data center away from the rest of the network, like an additional internal firewall, sometimes called a next-gen firewall, and as such, that keeps your network protected. Even if an attacker was to be inside your network, and the best-practice is to always assume access, they wouldn’t be able to steal data or cause critical damage. They would be stuck within a segment, unable to make any lateral moves to elsewhere in the network.
Related content: Read our guide to IT system mapping
What Are Some Micro Segmentation Examples?
There are many ways of approaching a microsegmentation security project. Here are a few of the most popular options:
Environment Segmentation: On a basic level, your first step when approaching microsegmentation might be to separate environments, such as separating out development and production. This is a low-hanging fruit option that can reduce risk fast.
Ring-fencing Crown Jewels: Another option is to start from your most critical assets or sensitive data, your crown jewel applications if you like, and ring-fence these away from the rest of the data center. This allows you to protect your most important assets or most sensitive data first and foremost.
Micro Segmentation by User or Role: Segmenting by user or role in line with the principle of least privilege
Micro Segmentation for Compliance: Segmenting all the information that’s in scope for any relevant compliance regulations.
Some solutions will even allow you to separate data that shares the same tier, all the way down to the process level, Layer 7.

Lanir specializes in founding new tech companies for Enterprise Software: Assemble and nurture a great team, Early stage funding to growth late stage, One design partner to hundreds of enterprise customers, MVP to Enterprise grade product, Low level kernel engineering to AI/ML and BigData, One advisory board to a long list of shareholders and board members of the worlds largest VCs
Tips from the Expert
In my experience, here are tips that can help you better implement microsegmentation and maximize its benefits:
- Utilize behavioral analytics for segment definition
Instead of relying solely on static criteria, leverage behavioral analytics to define and refine your segments. By analyzing typical patterns of application behavior, you can create more effective and adaptive microsegmentation rules that reduce false positives and improve security. - Implement microsegmentation gradually
Start with non-critical environments or less complex parts of your network to test and refine your segmentation approach. This phased rollout reduces the risk of disruptions and allows your team to gain confidence with the technology before applying it to more critical areas. - Incorporate microsegmentation into CI/CD pipelines
Integrate microsegmentation policies into your continuous integration and continuous deployment (CI/CD) pipelines. This ensures that new applications or updates are automatically segmented according to your security policies without requiring manual intervention. - Use endpoint detection and response (EDR) in conjunction
Pair microsegmentation with robust endpoint detection and response solutions. This combination allows you to not only restrict lateral movement but also quickly identify and mitigate threats within a segment before they spread. - Establish clear communication channels between security and application teams
Ensure that security teams and application developers work closely together when planning and implementing microsegmentation. Clear communication helps in aligning security requirements with application performance and functionality, avoiding conflicts and ensuring smoother deployments.
Starting with Visibility is Key for Network Microsegmentation
The most important thing to remember when looking at microsegmentation solutions is that you just can’t secure what you can’t see. Without true visibility from the start, you’re left using trial and error to create micro segmentation policies, or remembering from memory what exists and where. To see the benefits of micro segmentation, you want to start with a complete application map, including all dependencies within the network, and use this as the foundational step in forming a micro segmentation strategy.
That’s exactly what we do at Faddom. We have vast experience providing that visibility, and helping companies get the vital insight and control that they need to start their micro segmentation journey off right.
Ready to get that visibility? Speak to an expert today.
Ready to improve your cloud costs and make the most of best-practice network optimization tools and techniques? Start for free.