Managing IT inventory, sometimes known as IT asset management (ITAM), is crucial for any organization that wants to maintain control over its IT assets and safeguard its data. ITAM isn’t just about tracking laptops and desktops, though that may have been its primary focus in the past.
Today, smart IT managers understand that ITAM is about understanding the entire life cycle of the organization’s IT assets, from procurement to disposal. It’s about knowing what they have, where it is, who’s using it, and what software is running on it.
Table of Contents
ToggleWhy track this information?
Information from an accurate and up-to-date IT inventory helps organizations make informed decisions about asset management, resource allocation, and security. And all of these benefits can create cost savings, both directly, such as replacing the most high-maintenance systems with more modern and automated infrastructure, and indirectly, such as reducing the cost of a potential breach.
Efficient asset management generates ROI almost from the start. From streamlining procurement to minimizing data loss, it is one of the most powerful steps IT can put in place to keep costs under control.
In this post, we’ll explore everything organizations need to know to get started with IT inventory and asset management (ITAM), including benefits, challenges to putting an ITAM system in place, key features to look for in an inventory management system, and best practices every organization must be aware of to ensure a smooth transition.
What Is IT Inventory?
ITAM is a collection of processes and tools that organizations use to track, manage, and optimize the value of their IT assets.
All ITAM systems center around the IT inventory, a comprehensive list of all IT assets owned and managed by an organization. The list is essential in order to track and manage assets throughout their life cycle.
What is included in an IT inventory?
- Hardware: Computers, servers, laptops, printers, scanners, and other physical devices
- Software: Licensed software, open-source software, and cloud-based software
- Firmware: Embedded software that runs on hardware devices
- Data: Data stored on servers, laptops, and other devices, as well as data stored in the cloud
The IT inventory is just the beginning. A comprehensive ITAM system will use this information effectively to help an organization start saving money and operating more efficiently.
Benefits of Implementing an ITAM System
Direct benefits organizations may experience once they have implemented an ITAM system include…
Cutting Unnecessary IT Spending
By identifying and eliminating unnecessary IT spending, ITAM can directly reduce costs. For example, ITAM can help organizations identify unused software licenses, consolidate data centers, and maximize existing hardware to postpone new purchases.
Improving Security
ITAM can help organizations improve security by identifying and mitigating risks. For example, ITAM can help organizations identify vulnerabilities in software, track the movement of assets, and ensure that assets are properly disposed of.
Enhancing Compliance
With a complete inventory, IT teams can verify that all assets are being used in accordance with regulations. For example, ITAM can help organizations track the use of licensed software, check that mission-critical data is properly backed up, and protect confidential data.
Making Better IT Investment Decisions
ITAM can provide accurate and up-to-date information about organizations’ IT assets. For example, ITAM can help organizations identify underutilized assets, assess the risk of asset obsolescence, and make informed decisions about IT procurement.
Improving IT Service Delivery
By providing a better understanding of current IT assets, ITAM can empower organizations to identify and troubleshoot problems, prioritize IT projects, and allocate resources more effectively.
Streamlining Disaster Recovery
In the event of a physical or cyber disaster, having an up-to-date IT inventory helps identify the systems to prioritize and minimizes operational disruptions.
Challenges in IT Inventory Management
With all of the benefits explored above, it may come as a surprise that some organizations have still not transitioned to a comprehensive ITAM system. That’s because there are a few obstacles standing in the way:
Dealing with Diverse and Distributed Assets
Keeping track of assets can be difficult due to constant changes and a lack of clear documentation. In addition, asset discovery can be challenging without the right tools and processes in place.
Addressing Inaccuracies and Data Inconsistencies
Missing asset documentation can lead to a loss of knowledge about assets and their integrations.
Managing Shadow IT, End of Life, and Disposal of IT Assets
Shadow IT, the unauthorized use of IT systems, and software decay, the deterioration of software quality, both pose security risks and compliance violations. Unauthorized systems may lack security measures, while decayed software may contain vulnerabilities. ITAM also helps optimize IT asset disposal at end of life, letting organizations derive maximum value while minimizing risks. It can help verify that assets containing sensitive data are wiped or destroyed before disposal to ensure compliance with data privacy regulations like GDPR and HIPAA.
Key Features: What to Look For in IT Asset Inventory Systems
Once the decision has been made to adopt a comprehensive IT asset inventory system to transform the organization’s IT operations and improve efficiency, security, and compliance, there are a few key features to watch for.
Without these features, the organization’s asset inventory system may struggle to maintain an accurate and up-to-date inventory, leading to gaps in asset visibility and control.
- Comprehensive Discovery and Identification: The ITAM system should automatically identify and catalog all IT assets within an organization, including hardware, software, firmware, and network devices.
- Asset Tracking and Lifecycle Management: The ITAM system should continuously track the life cycle of each asset, from procurement to disposal, including warranty information, maintenance contracts, and end-of-life considerations.
- Asset Attribution and Ownership: The ITAM system should allow assigning of ownership and accountability for each asset to ensure clear responsibility for asset management and security.
- Asset Data Accuracy and Validation: The ITAM system must facilitate compliance by flagging unlicensed software and malware. It should also facilitate efficient patch management. It needs to maintain accurate and up-to-date asset information through regular data validation and reconciliation processes.
- Reporting and Analytics Capabilities: The ITAM system must provide a single source of truth for IT asset information, eliminating unused or duplicate assets and streamlining reporting. It must also generate insightful reports and analytics, providing visibility into asset usage, identification of potential risks, and informing strategic decision-making.
Beyond these essential features, the next section will explore best practices to help organizations ensure a successful rollout of the chosen ITAM system.
Best Practices in IT Inventory Management
Inventory management must become an innate part of IT operations. Without the right tools and procedures in place, the manual steps and drudgework involved mean it too often takes a back burner to more urgent concerns. By following these best practices, organizations can ensure that inventory management runs like a well-oiled machine.
Regularly Update and Audit Inventory
A comprehensive, standalone, and automated IT asset discovery and mapping tool is the best way to achieve transparent, efficient ITAM processes. Be sure to choose an ITAM tool that can…
- Effectively manage all types of IT assets, including hardware, software, firmware, and network devices
- Provide comprehensive asset discovery, tracking, reporting, and analytics capabilities
Quick Tip
“Ghost assets,” meaning assets that are still listed but are no longer physically present or used, make up 10% to 30% of the average organization’s inventory. Use audits to help clear out ghost assets, saving money on unnecessary licensing fees and maintenance.
Implement a Centralized Inventory Management System
This database will serve as a single source of truth for all IT assets and their dependencies. So it must be able to…
- Store and manage all asset information in a single, unified location for data consistency, accessibility, and disaster recovery
- Establish clear access controls to restrict access to asset data based on user roles and responsibilities
- Regularly incorporate updates from asset discovery tools, change management systems, and other sources of asset data
Quick Tip
Be proactive. Don’t wait until inventory audits to identify and correct data discrepancies. Implement automated data validation checks to ensure the accuracy and consistency of asset information on an ongoing basis.
Take Advantage of Tagging and Labeling
Organizations find asset management simpler and more efficient if they use asset identifiers, either physical or digital, for identification, tracking, and organizing IT assets. Here are a few ways to make this simpler.
- Use barcode labels, QR codes, or RFID tags to assign unique identifiers to each IT asset.
- Categorize based on asset type, function, and location, using standardized labels or naming conventions. A little planning can go a long way.
- Incorporate asset details, like serial numbers, purchase dates, and warranty information, into the tagging system for easy reference.
Quick Tip
Prioritize ITAM efforts by starting with the most critical assets, using the discovery and mapping tool to identify their life cycles, potential upgrades, and end-of-life considerations.
Standardize Processes and Procedures
Establishing consistent processes and procedures fosters efficiency, reduces errors, and facilitates collaboration around IT asset management. A few of the most important processes include
- Creating consistent and repeatable processes for identifying, locating, and capturing information about all IT assets across the organization.
- Assigning ownership of each IT asset to a specific individual or department, ensuring clear responsibility for the asset’s management and security.
- Establishing procedures for asset handovers, reassignments, and disposals.
- Performing regular data validation checks for the asset DB, including verifying asset details, cross-referencing with other sources, and resolving discrepancies.
Quick Tip
Integrate ITAM data with the service desk knowledge base to empower users. They’ll be able to resolve common issues independently, reducing the burden on service desk personnel.
Application Dependency Mapping for IT Asset Management
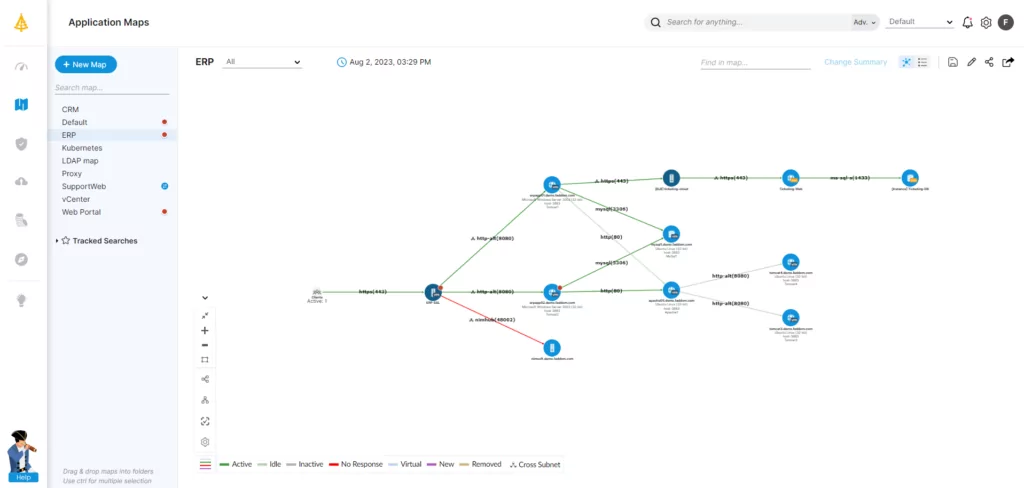
An application dependency mapping (ADM) tool helps organizations implement IT inventory management best practices by enhancing visibility and control.
ADM can reveal hidden connections and potential problems that could disrupt operations. And by automatically discovering and mapping application dependencies, it cuts the time and work involved in inventory management, freeing up teams to handle other critical tasks while also ensuring accuracy and consistency.
Faddom is an ADM tool that provides a comprehensive map of the entire IT infrastructure landscape.
It automatically discovers and maps dependencies between applications, servers, networks, and other components while integrating with ITAM systems for real-time asset updates and simplified inventory management. That, in turn, helps organizations prevent and resolve problems like outages, performance bottlenecks, and security vulnerabilities.
Faddom is simple to use, completely agentless, and it’s lightning fast, unearthing all these connections in under an hour with no manual installation, firewall configuration, or any other hands-on involvement.
And after the initial rollout, Faddom will continuously monitor the IT environment, providing real-time updates to ensure that the asset inventory is always up to date. It also provides actionable insights and reports for compliance and security, informing decision-making when it comes to IT infrastructure.
When you’re ready to take control of your IT infrastructure with seamless asset management, fill out the form on this page to start a free trial with Faddom today!









