Enterprises today use a combination of SaaS products alongside on-premises software and networking systems to keep their businesses running smoothly. From small businesses to large multinational corporations, maintaining and keeping track of a growing number of IT resources is a major endeavor. One way to keep these resources organized is through a process known as IT configuration management.
What Is IT Configuration Management?
TechTarget defines configuration management as “a governance and systems engineering process used to track and control IT resources and services across an enterprise.” In addition, configuration management ensures that systems are consistent and perform as expected at all times.
Table of Contents
ToggleThe idea of configuration management began in the 1960s as a project within the United States Department of Defense as a form of hardware management. In the years that followed, IT business leaders saw value in configuration management as the popularity of enterprise computing grew; they brought these principles to the private sector. In addition to IT, configuration management is today an important component of software engineering, civil engineering, and other disciplines.
This post will address:
- The benefits of IT configuration management
- The purpose of an IT configuration management policy
- IT configuration management process and procedures
- How to develop an IT configuration management plan
Why Is IT Configuration Management Important?
IT operations leaders often work according to the following four foundational purposes of IT configuration management: Security, compliance, service delivery, and consistency. In this section, each purpose will be discussed in detail.
Security
Declaring that IT security is important is an understatement! The ever-growing number of security breaches and vulnerability exploits shows that enterprise security should be a top priority for business leaders. Configuration management and security go hand in hand. Login credentials, secrets management, and rules around firewalls and ports are all a part of enterprise configuration. Keeping these rules well documented and up to date can diminish the ability of malicious actors to exploit vulnerabilities.
Compliance
Government regulations and industry groups alike often require businesses to prove that they have a configuration management practice in place. This is frequently a precondition to meeting compliance regulations or receiving a certification. Maintaining standards set by a third party also shows that a business can follow universally accepted principles. This, in turn, creates opportunities for contracts with potential customers and entities that require certifications, regulatory compliance, and adherence to certain business norms.
For example, companies who want to sell software to the federal government of the United States must provide a complete software bill of materials (SBOM). While a SBOM is not configuration management in and of itself, it is a prerequisite for creating an accurate configuration management practice.
Service Delivery
While IT teams work hard to prevent errors and outages, sometimes they are inevitable. In these situations, having a configuration management practice is key to getting systems back online as quickly as possible. Being able to trace past steps from a recent point in time, rather than trying to figure out what happened manually, can save hours in unplanned downtime; it can also save money that would otherwise be spent on unnecessary IT resources. IT teams can also spend more time doing meaningful work, rather than fixing preventable issues.
Consistency
In the case of configuration management, consistency means doing the same task in the same manner every time. When a new device is added to the network or needs to be replaced, IT teams know that there is already a defined way to do it. Consistency also sets a baseline for what is “normal” within a system. This makes it easier to troubleshoot, because configuration issues may be more obvious if they are deviating from the known baseline.
What Are the Risks of Not Using Configuration Management?
The risks of not using configuration management are multiple, and could present significant issues to an organization. Note that all are directly related to the previously mentioned principles of security, compliance, service delivery, and consistency.
- Compromised security: Without documentation of all software, systems, and their dependencies, it is impossible to be certain of what is running in an IT environment. Businesses are thus left exposed to attacks via unauthorized software.
- Difficulty performing root cause analysis: It will be challenging to get to the root cause if the baseline IT environment is unknown. This leads to lots of guesswork and wasted time.
- Unknown knock-on effects: A seemingly innocuous software update could lead to unplanned downtime if its wide-reaching effects are not identified in advance. Having a configuration management practice in place prevents this.
- Increased manual work: With a configuration management policy, IT teams have a source of truth to work from whenever there is an issue. Without it, teams would essentially have to start from scratch whenever attempting to troubleshoot an issue. This also wastes time and money.
IT Configuration Management Process and Procedures
So what does IT configuration management actually look like in practice? Adherence to the following steps is essential to developing a successful policy.
- Identification
- Baseline
- Version control
- Auditing
- Testing
In this section, each step will be discussed in turn.
Identification
Step one is gathering all available information about configuration data. This information should be compiled from all application environments, and should include encryption keys and passwords. Once this data is organized, it should be considered an organization’s single source of truth for anything pertaining to configuration.
Baseline
Once all software and hardware components of a system have been identified, a baseline can be established. In this context, baseline refers to a known state that will operate without error.
Note that the baseline is not static. In order to keep the baseline up to date, administrators must log all changes, regardless of how minor they may seem.
Version Control
Using a version control system (VCS) as a part of the configuration management process helps IT administrators more easily, and allows them to roll back to the baseline if necessary. Caution should be taken when including passwords or encryption keys in a version control system. If this information is accidentally committed, an organization’s security may be compromised.
Auditing
Configuration management tools allow ongoing comparison of the hardware and software that is actually present, versus what the tool thinks is present. It is important to ensure that the tool’s model and actual practice match up, and to correct any differences. Trusting—and maintaining—a configuration management tool is crucial.
Testing
Testing the configuration management tool will reveal whether it is up to the task. It is ideal to test in a small segment of the IT environment—something like a software update. The configuration management tool should be able to identify dependencies.
IT Configuration Management Plan
Configuration management includes not just the active steps discussed previously, but also the development of a comprehensive plan that an organization can follow. The National Institute of Standards and Technology (NIST) of the United States Department of Commerce defines an IT configuration management plan as “a comprehensive description of the roles, responsibilities, policies, and procedures that apply when managing the configuration of products and systems.”
According to the NIST’s guide, a configuration management plan should include the following:
- Configuration control board: Also known as a change control board, this is a group of individuals that has the responsibility of controlling and approving changes to products and systems. The group should be established with a charter, and comprise two or more individuals.
- Configuration item identification: This refers to developing a methodology for identifying and naming configuration elements that need to be under management control.
- Configuration change control: Creating a process for managing updates and changes to the baseline configuration.
- Configuration monitoring: Ensuring there is a process of testing a configuration against the baseline, and a process for reporting on configuration status.
IT Configuration Management Policy
Taking into account the above information, it is clear that any business without a written IT configuration policy should begin preparing one. Such a document is intended to ensure that all IT assets are documented with their known interdependencies and relationships, so that change management, impact analysis, and compliance activities can be executed.
What should this look like? Here is the NIST’s configuration management policy outline that it encourages organizations to adapt to their specific needs.
Examples of Configuration Management Policies
IT configuration management policies are found at organizations of all sizes across industry types. Below, four publicly available, real-world examples illustrate different ways that this document can be developed:
- Georgetown University (higher education)
- State of Maine (US state government)
- Environmental Protection Agency (US federal government agency)
- Procter & Gamble (multinational corporation)
While these documents are of varying length, they all include the basic elements recommended by the NIST.
Configuration Management with Faddom
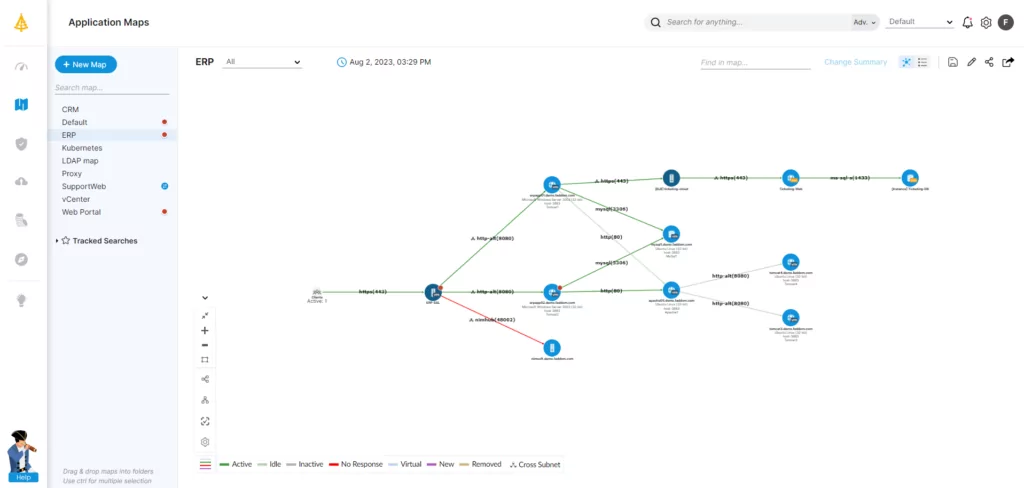
Developing a configuration management policy is an essential step for responsible business practice, offering benefits in the realms of security, service delivery, consistency, and compliance. It may seem like a daunting task initially, but it is not something that your organization has to do alone.
Faddom can work with you to map all your hybrid infrastructure both on premise and in the cloud — without agents and in less than 60 minutes, helping you to undertake configuration management efficiently and effectively. Just start a free trial today today!








