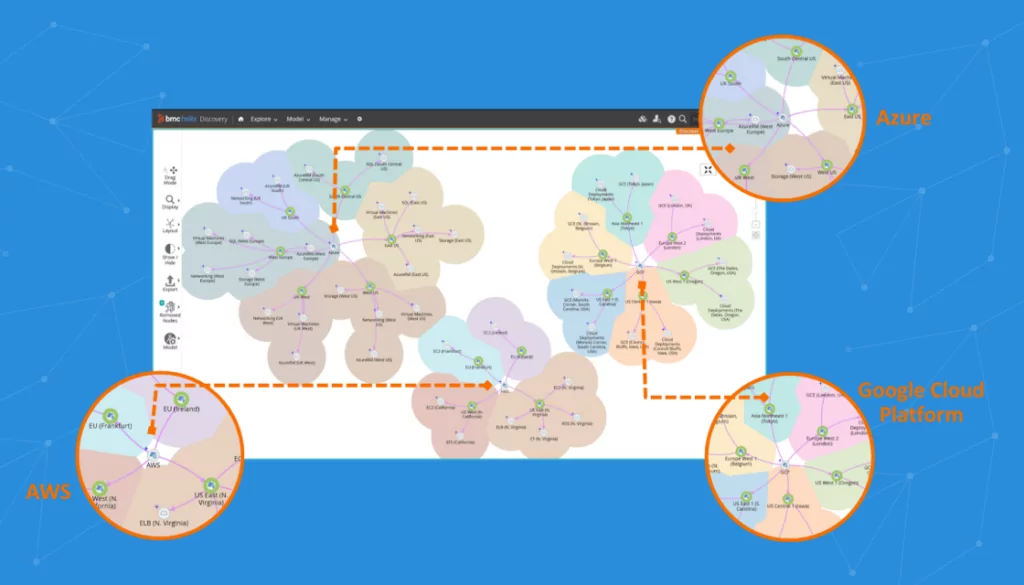
What is IT Asset Discovery?
IT asset discovery is the process of discovering, classifying, and managing an organization’s IT assets. In addition to on-premise servers, today, these assets may include the cloud, virtual servers, and mobile devices in addition to on-premise servers. Organizations keep track of their network’s active and inactive assets through IT asset discovery.
IT asset discovery helps IT managers create data sets that provide essential information about who is logged in to which device at any given moment, which devices require rebooting, which programs are installed on a device, and which software licenses need to be renewed. Because of this, IT asset discovery—frequently included as a component of a specialized ITAM solution—is crucial for safeguarding a business’s IT assets.
This is part of a series of articles about Application Discovery
Table of Contents
ToggleExamples of IT Assets
Hardware
The hardware category includes all the physical components of your IT infrastructure. This typically includes servers, desktops, laptops, printers, routers, switches, and other networking equipment. In the era of IoT, this category also includes smart devices like smart speakers, smart TVs, and even smart refrigerators.
Hardware assets often represent a significant investment for businesses, so keeping track of them is crucial. IT asset discovery can help you manage hardware lifecycles, optimize usage, and prevent theft or loss.
Software
The software category includes all the applications and operating systems running on your IT assets. This can range from productivity apps like Microsoft Office to complex enterprise software like ERP systems.
Software asset discovery is crucial for several reasons. It can help you ensure software license compliance. Software vendors often conduct audits, and if you’re found to be using more licenses than you’ve purchased, you could face hefty fines. Software asset discovery can also help you optimize software spending, by identifying unused or underutilized software.
Cloud
The cloud category includes all the IT resources hosted on public, private, or hybrid cloud platforms. This can include virtual machines, containers, databases, storage, and software as a service (SaaS) applications.
With the rise of cloud computing, many businesses have shifted significant portions of their IT infrastructure to the cloud. However, this shift has also introduced new challenges in terms of visibility and control. With cloud asset discovery, you can gain insight into your cloud resources, ensure they are secure, and optimize cloud spending. Moreover, asset discovery can help identify shadow IT—cloud services used without IT’s knowledge or approval.
Learn more in our detailed guide to asset discovery tools
Benefits of IT Asset Discovery
IT asset discovery provides a number of benefits, most importantly asset and report harmonization, streamlining and simplification of assets, and enhanced compliance and security.
Related Content: Discover more about IT Documentation
Harmonized Assets and Reports
IT asset discovery combines data from several tools into a single database. In addition to providing reports—like device utilization statistics and software licensing compliance data—the database also contains up-to-date system information and a history of software or hardware installations.
Such information can help in eliminating unused and duplicate assets, and reduce the time required to handle any network issues. It can also reduce the volume of work required to execute an IT infrastructure upgrade or a network audit, since redundant software deployed in the network is periodically identified and eliminated. Decisions about purchasing IT assets may be made with relative ease, since current capacity and needs are known.
Streamlined and Simplified Asset Management
Automatic asset discovery speeds up IT asset management’s procurement and reporting components. For example, identifying licenses for unused software products helps businesses avoid unnecessary purchases and allocate that money to more crucial business needs. Thus, automatic IT asset discovery helps organizations optimize their asset management processes.
Visibility for Improved Security
IT asset discovery provides the visibility required to prevent intrusions into a business’ IT assets. As such, IT asset discovery aids in ensuring compliance with corporate security standards in two important ways. Firstly, it seizes unlicensed software, which frequently serves as a backdoor for phishing attacks and security flaws. Utilizing this knowledge facilitates efficient management of patches. Secondly, it uncovers malware that may be covertly installed on external devices utilized by the company. This reduces the most significant risk associated with using the bring-your-own-device (BYOD) approach.
Ensuring Software License Validity
Using unlicensed and non-compliant software can cause unsuccessful external audits and result in expensive fines. Fortunately, software license validity is routinely checked as part of IT asset discovery. By monitoring all software applications, IT asset discovery enables the discovery of illegitimate applications, thus allowing a business to take a proactive approach to software licensing and compliance.

Lanir specializes in founding new tech companies for Enterprise Software: Assemble and nurture a great team, Early stage funding to growth late stage, One design partner to hundreds of enterprise customers, MVP to Enterprise grade product, Low level kernel engineering to AI/ML and BigData, One advisory board to a long list of shareholders and board members of the worlds largest VCs
Tips from the Expert
In my experience, here are tips that can help you get the most out of IT asset discovery:
-
Choose the right discovery method
Use passive discovery for broad, low-impact scans and active discovery for real-time visibility. Combining both methods can provide comprehensive coverage.
-
Implement automated discovery tools
Automate asset discovery to ensure real-time updates and accuracy. This reduces manual errors and keeps your asset inventory current.
-
Map dependencies between assets
Understanding the relationships between applications, devices, and networks is crucial for impact analysis and troubleshooting, especially in hybrid environments.
-
Regularly audit and update your inventory
Periodically review your asset data to identify outdated or unused assets. This helps optimize costs and ensures compliance with security and licensing requirements. -
Integrate discovery tools with ITSM systems
Link your asset discovery tools with IT service management systems to streamline processes like incident management and change control, enhancing operational efficiency.
IT Asset Discovery Methods
Passive Asset Discovery
A prerequisite for a passive asset discovery technique is the ability of every device in a business to send syslogs. A log management program then stores these and continuously refreshes the live data to generate an asset.
The passive asset discovery method offers more coverage and uses less bandwidth than its alternative (active asset discovery, see below.) It enables businesses of all sizes to produce assets using current and archived data. For instance, a company with multiple locations can sync old logs from its local syslog to a central repository. This allows the network’s main office to spot security gaps across the organization’s branches.
Active Asset Discovery
The active asset discovery method involves pinging every device that interfaces with the network. Because it demands live activity, archived processes or functions cannot sync or be detected. Active asset discovery uses more bandwidth than passive asset discovery, and typically requires substantial effort to set up.
Active asset discovery is a complicated method. Since it permits extensive bi-directional network queries, there is also potential for harm and network congestion.
IT Asset Discovery Tools: Key Capabilities
IT asset discovery tools are software solutions designed to automatically identify and inventory all digital assets within an organization’s network. These tools are crucial for IT asset management (ITAM), as they facilitate a comprehensive understanding of the assets an organization possesses, their configurations, and how they are utilized.
IT asset discovery tools should provide the following capabilities:
1. Network Scanning
This function allows you to automatically discover and catalog all devices connected to your network, whether wired or wireless, on-premise or remote.
Learn more in our detailed guide to application inventory template
Network scanning not only identifies the devices but also gathers essential information about them, such as their IP addresses, operating systems, installed software, and hardware configurations. This data is invaluable for network management, troubleshooting, and security.
2. Software License Management
This feature helps you keep track of all the software licenses in your organization, ensuring you’re in compliance with the license terms and avoiding costly fines.
Software license management can also help you optimize software spending. By monitoring software usage, you can identify unused or underused licenses and relocate them where needed. This can reduce wastage and save money.
3. Inventory Management
Inventory management involves maintaining a complete and up-to-date inventory of all your IT assets, including hardware, software, and digital assets.
With inventory management, you can easily locate any asset, monitor its status, and manage its lifecycle. This can improve asset utilization, reduce downtime, and prevent asset loss or theft.
4. Security Monitoring
Security monitoring allows you to continuously monitor your IT assets for signs of security incidents, such as unusual behavior, unauthorized changes, or potential vulnerabilities.
With security monitoring, you can quickly detect and respond to threats, minimizing the damage they can cause. This can enhance your overall security posture and protect your business from costly data breaches.
5. Compliance Reporting
Compliance reporting features enable you to generate reports that demonstrate your compliance with various regulatory standards, such as GDPR, HIPAA, or PCI DSS. Compliance reporting can simplify the audit process and help you avoid penalties for non-compliance.
Considerations When Choosing an Asset Discovery Tool
Scope of Discovery
When selecting an IT asset discovery tool, it’s important to consider the scope of discovery it supports. The tool should be capable of identifying and inventorying a wide range of assets across different environments, including on-premise, cloud, and hybrid infrastructures. This ensures comprehensive visibility into all IT assets.
Usability
Usability is another critical factor. The tool should be user-friendly, with an intuitive interface that allows for easy navigation and operation. This ensures that IT staff can efficiently utilize the tool without requiring extensive training, making it easier to integrate into existing workflows and processes.
Accuracy
The accuracy of the asset discovery tool is paramount. It must reliably identify and inventory assets without significant errors or omissions. High accuracy ensures that IT managers have confidence in the data provided by the tool, which is essential for effective decision-making and planning.
Integrations
Integration capabilities are important to consider, as the tool should seamlessly integrate with other IT management and security systems. This allows for the sharing of asset information across platforms, enhancing the organization’s ability to manage, secure, and optimize its IT environment.
Meet Faddom: Automated Discovery for All Your IT Assets in Minutes
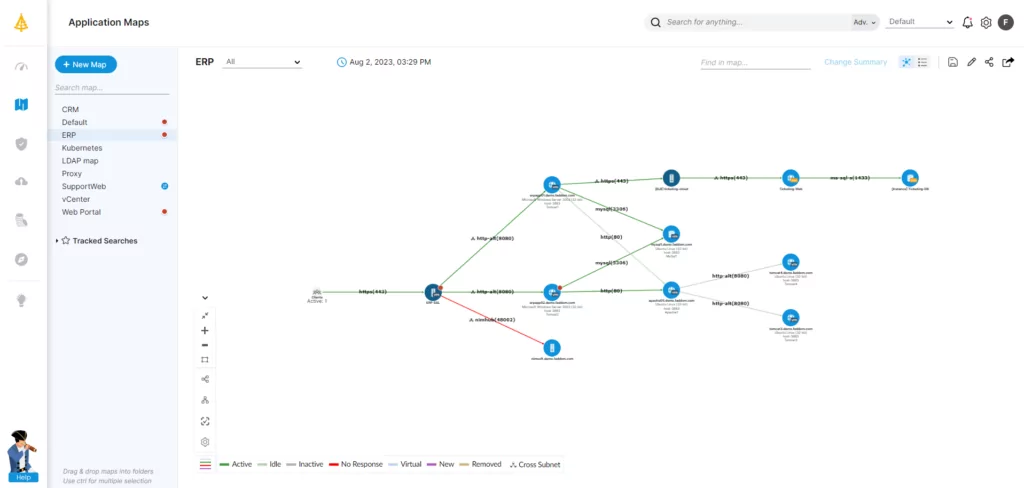
Effective IT asset discovery is a prerequisite for superior IT asset management. Although there are two methods for discovering IT assets, the passive approach is preferred because it covers a more extensive scope and consumes less bandwidth. Organizations can benefit from IT asset discovery in various ways, such as asset and report harmonization, simplification of asset management, and protection of compliance and security parameters. Best practices for effective asset discovery, such as implementing a solid inventory management framework, ensure the full benefits of IT asset discovery may be obtained.
For a detailed and granular view of all your assets and dependencies, an agentless, cloud-based IT infrastructure and application mapping software is essential. Faddom helps organizations worldwide with IT asset management by mapping their entire hybrid IT environments—both in the cloud and on-premise—in as little as one hour.
Start a free trial today by filling out the form on the sidebar!