Asset discovery tools are designed to automatically identify and catalog all the IT assets within an organization’s network. They scan networks to detect devices, software, and sometimes configurations or services, creating an inventory of digital (and occasionally physical) assets. This process aids in understanding the scope of an organization’s resources, enabling better asset management and security.
By providing real-time visibility into the assets on a network, asset discovery tools play a crucial role in IT asset management (ITAM). They help organizations keep track of asset performance, usage, and lifecycle.
Additionally, these tools can identify unauthorized devices or software, helping to mitigate potential security risks. Their ability to discover and document assets automatically saves time and reduces errors compared to manual inventory methods.
Table of Contents
ToggleKey Features of IT Asset Discovery Tools
IT asset discovery tools typically offer the following capabilities:
-
- Network scanning: Enables the automatic detection of all connected devices and software within an organization’s network. This allows for the identification of networked assets, including servers, workstations, printers, routers, and switches.
-
- Software license management: Tracks and manages the usage and deployment of software licenses within an organization. This helps ensure compliance with software licensing agreements, preventing legal issues and financial penalties associated with under-licensing or over-licensing software.
-
- Inventory management: Offers a centralized repository for tracking and managing all IT assets across an organization. This enables IT teams to maintain up-to-date records of hardware, software, and associated details such as purchase dates, warranty information, and configuration settings.
-
- Compliance reporting: Automates the process of generating reports that demonstrate adherence to various regulatory standards and internal policies. These tools collect data on software licenses, hardware configurations, and network activities to compile detailed documentation for audit trails. This capability is essential for organizations subject to GDPR, HIPAA, or SOX regulations.
Related Content: Read our guide about IT mapping and application discovery
Notable Asset Discovery Tools
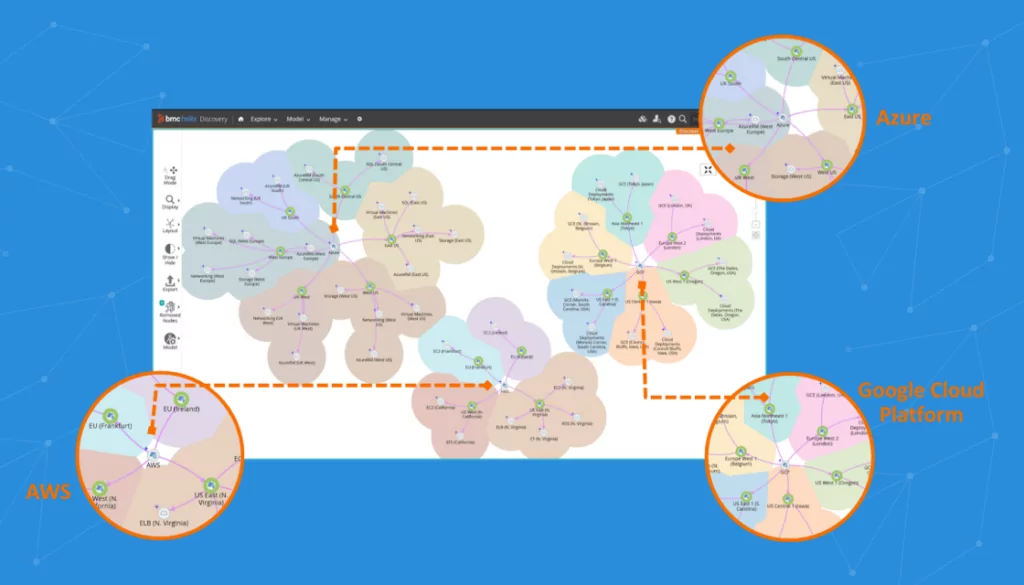
1. Faddom

Fadodm is a real-time Application Dependency Mapping tool that maps all your servers, both cloud and on-prem into the business apps they support.
Key features:
-
- Secure: Faddom is agentless and doesn’t require credentials
-
- Affordable: starting at $10K/year
-
- Real-time: Map the entire environment in real-time, updating 24/7
-
- Quick: One person can map the entire organization in an hour
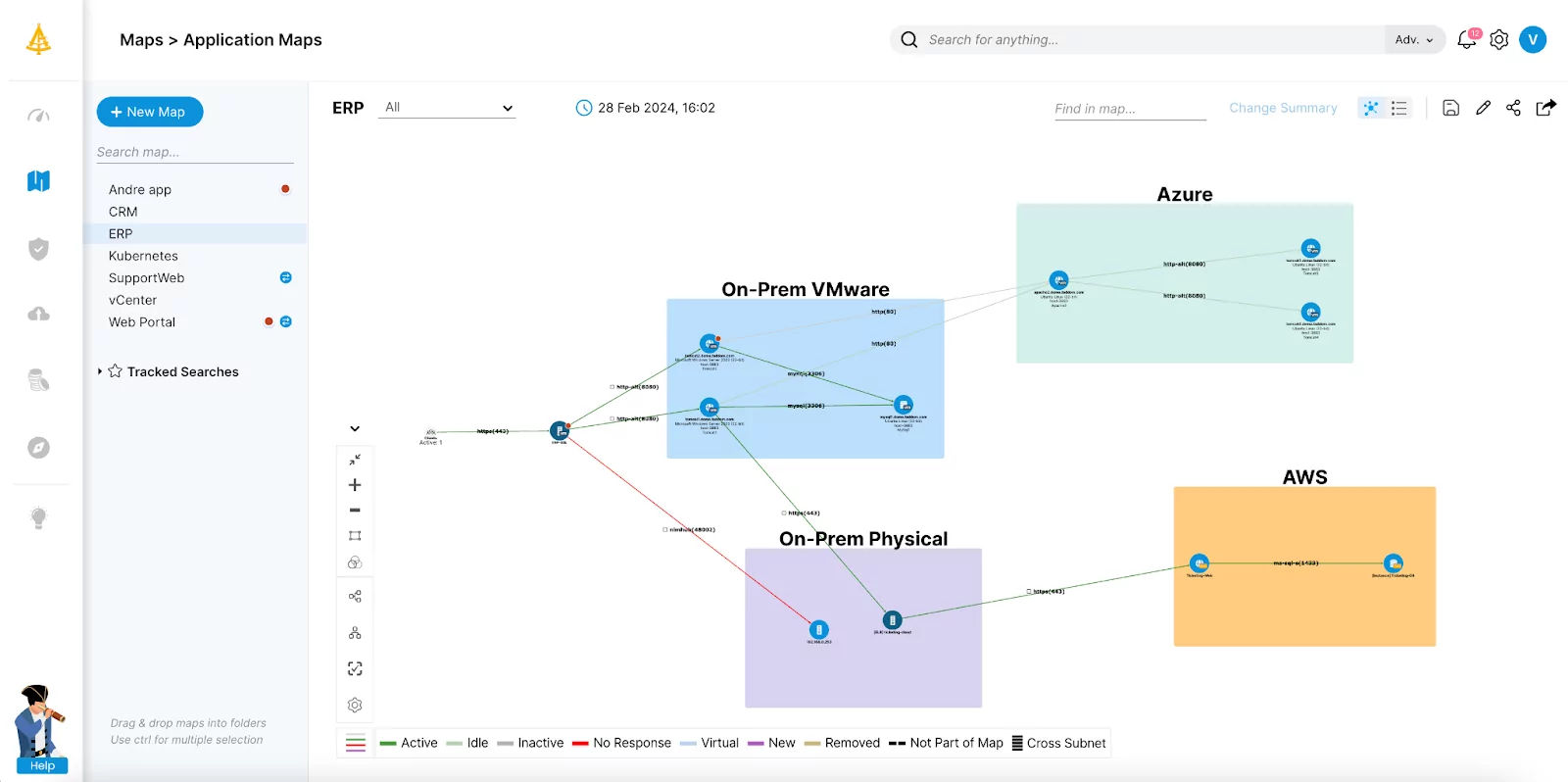
2. Lansweeper

Lansweeper is an IT asset discovery tool that automates the identification and inventory of IT, OT, IoT, and public cloud assets across an organization’s network. By providing visibility into technology assets, Lansweeper improves security, simplifies IT management, and provides insights into asset configurations and usage patterns.
Key features:
-
- Automated discovery: Automates the asset discovery process to ensure a constantly updated inventory without manual input. It scans for changes or additions in the IT landscape to provide real-time insights.
-
- Data breadth: Offers discovery capabilities across IT, OT, IoT, and Public Cloud assets including workstations (Windows, Linux, Mac), servers, printers, switches, routers, virtual machines, and cloud instances.
-
- Data depth: Delivers details on asset configurations and usage patterns for informed decision-making.
-
- Risk mitigation: Instantly identifies unmanaged and rogue endpoints upon connection to the network.
-
- Scanning methods: Combines active and passive scanning with agent-based or agentless options for a comprehensive view of the network’s assets.
-
- External discovery connectors: Integrates data from external sources like SCCM and Intune for a unified view of lifecycle information.
Source: Lansweeper
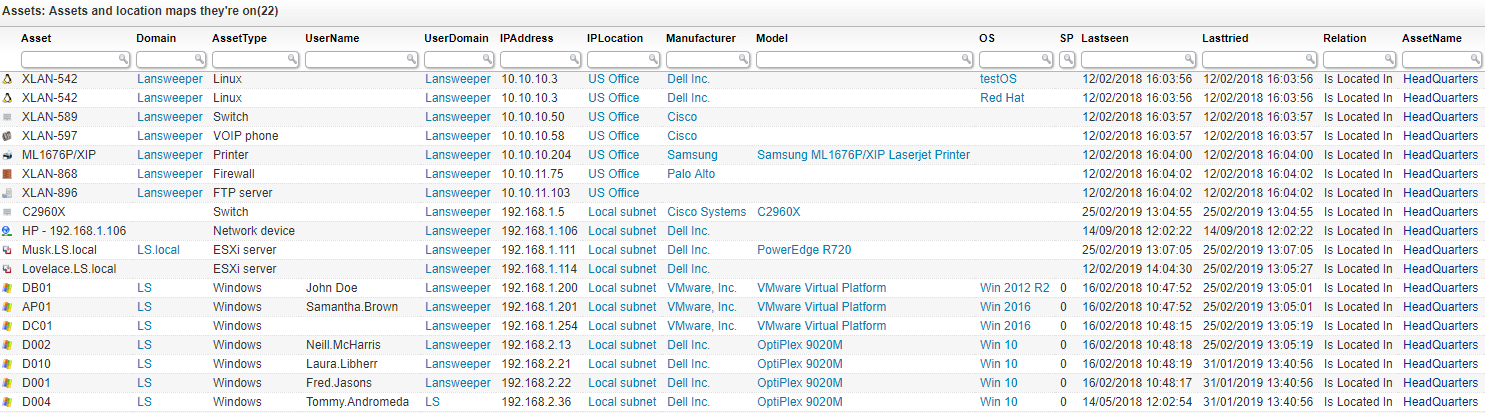
3. Asset Panda

Asset Panda is a configurable asset tracking platform. It offers a cloud-based solution that adapts to workflows and enables efficient tracking of IT assets. With its emphasis on customization, Asset Panda supports a range of use cases, helping organizations manage assets without altering their operational processes.
Key features:
-
- Configurable platform: Can be customized for different asset types and tracking needs, enhancing accuracy.
-
- Integrations: Offers integration with software such as Cisco Meraki, DocuSign, Jira, and Microsoft Azure Active Directory, enhancing data consistency.
-
- Asset tracking: Enables tracking of both digital and physical assets including contracts, software licenses, laptops, and vehicle fleets. Supports detailed management of each asset type.
-
- Cloud-based solution: Provides a centralized platform for asset management accessible from anywhere.
-
- Mobile app availability: Features mobile applications for Android and iOS devices, allowing on-the-go asset management including barcode scanning for quick data access.
-
- Custom field creation: Allows users to create custom fields tailored to their operational needs.
Source: Asset Panda
4. Zluri

Zluri is a SaaS management platform designed to provide IT teams with visibility into their organization’s software landscape. It centralizes the management of both managed apps and those installed on individual devices, offering insights into user activity, license utilization, spend analysis, and security assessments in real time.
Key features:
-
- 360° visibility: Offers a holistic view of all applications, users, and associated costs within the SaaS ecosystem.
-
- Categorization by importance and risk: Supports control over all applications by categorizing them according to their importance and associated risks. This helps in prioritizing management efforts.
-
- Administrative controls for critical applications: Allows assignment of owners, setting up notifications and alerts, automating tasks where possible.
-
- Shadow IT monitoring: Identifies unauthorized software usage across the organization, helping mitigate security risks associated with unsanctioned applications.
-
- License and cost optimization: Enables optimization of software licenses by identifying unused or underutilized licenses.
-
- SaaS spend management: Provides tools for tracking and optimizing SaaS spending across the organization. Helps in avoiding budget overruns and ensures financial efficiency in SaaS investments.
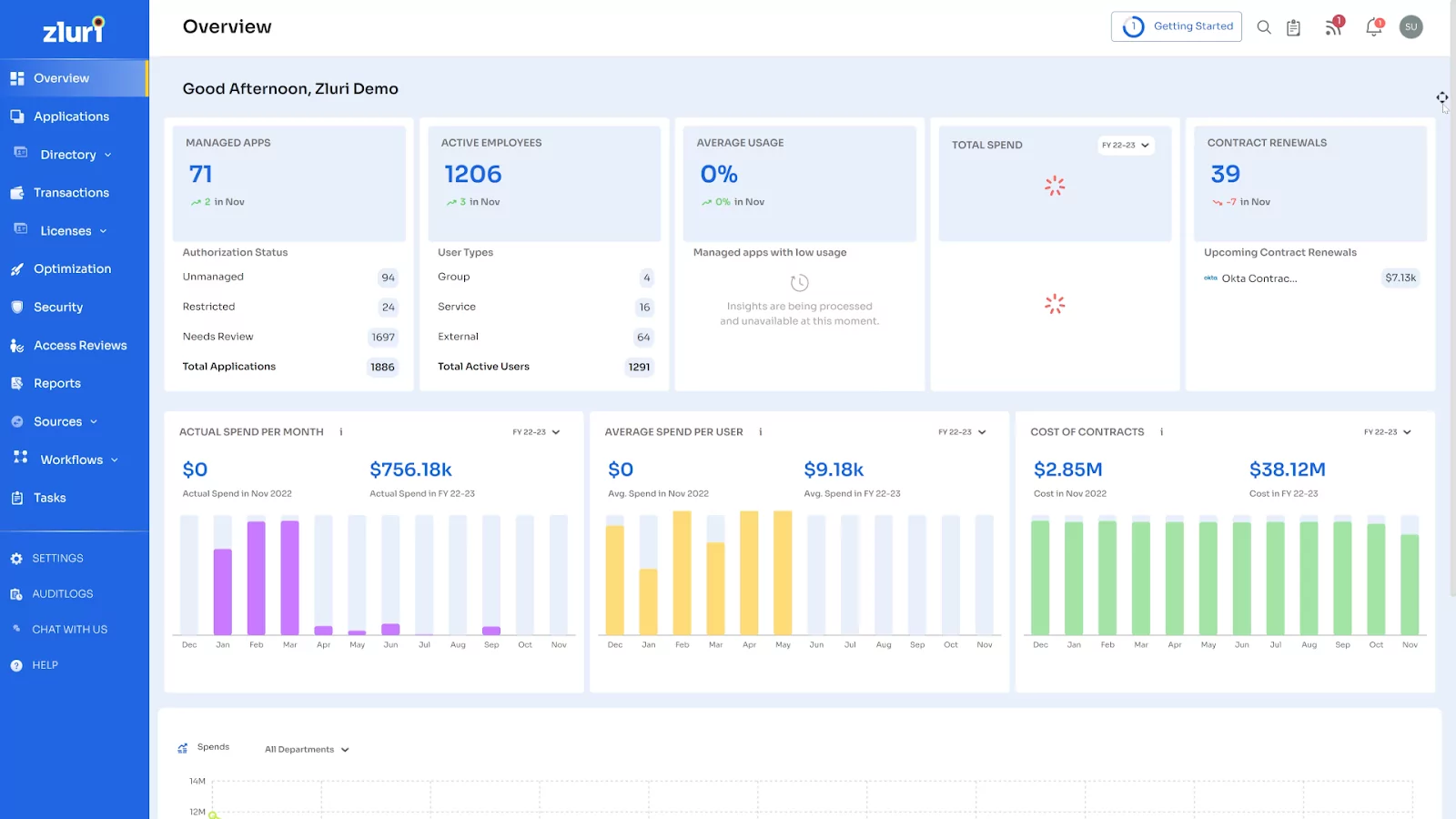
Source: Zluri
5. Invicti

Invicti offers a solution for identifying and managing web-facing assets. It automates the process of finding lost, forgotten, or unauthorized web assets, including websites, applications, APIs, and cloud services. This continuous scanning ensures that all potential security vulnerabilities across an organization’s digital presence are identified and addressed.
Key features:
-
- Continuous web asset discovery: Automatically identifies all web-facing assets associated with an organization to ensure comprehensive security coverage.
-
- Website crawling: Utilizes crawling techniques to analyze websites and applications for vulnerabilities.
-
- Deployment options: Offers various deployment methods to suit different organizational needs, including on-premises or in the cloud.
-
- Scanning coverage: Provides scanning capabilities that cover every aspect of an organization’s web presence. This includes detailed analysis of APIs, web services, and virtual servers in cloud environments.
-
- Automated notifications: Sends automatic alerts when new web-facing assets are discovered.
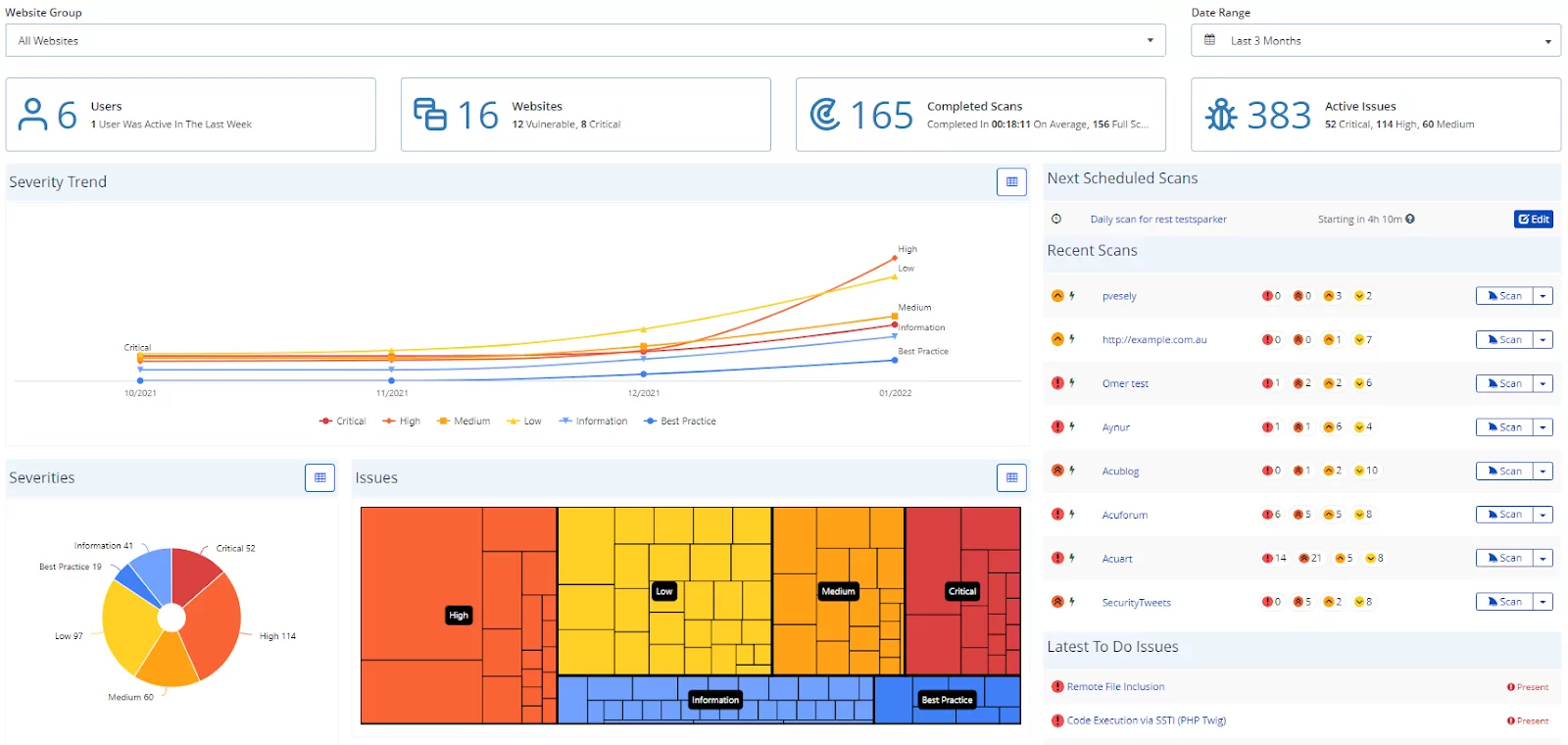
Source: Invicti
6. Paessler PRTG

PRTG is a network monitoring tool designed to automatically discover and monitor every device within your network. It aims to provide a user-friendly approach to network management by simplifying the detection, visualization, and monitoring process of network devices and services. With its auto-discovery feature, PRTG ensures that new devices are promptly identified and integrated into the monitoring setup.
Key features:
-
- Automatic network discovery: Automatically identifies all devices within specified IP ranges.
-
- Custom alerts and notifications: Tailors notifications to meet specific needs, ensuring immediate awareness of issues or changes in the network environment.
-
- Monitoring: Monitors various device types across different vendors, offering insights into each asset’s status and performance.
-
- Visualization tools: Features like device tree structures and custom dashboards provide an intuitive overview of your network’s health, making it easier to identify and address issues.
-
- Compatibility: Compatible with major vendors and systems, helping avoid vendor lock-in.
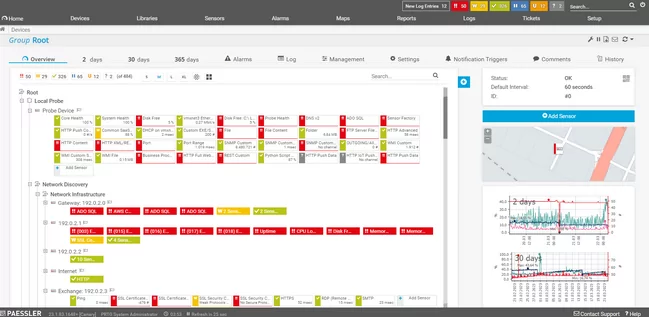
Source: Paessler
7. Auvik

Auvik aims to simplify network monitoring and troubleshooting, offering real-time insights to keep business-critical connections up and running. It supports the management of IT assets, visualizes network topology, and aids in problem resolution. This tool is suitable for IT departments aiming to maintain high availability and performance of their network infrastructure.
Key features:
-
- Real-time monitoring: Provides immediate alerts for over 50 pre-configured network events, ranging from informational to emergency, customizable to meet specific needs.
-
- Centralized syslog management: Offers a centralized view of syslog messages from all network devices, enhancing the speed of troubleshooting efforts.
-
- VPN capacity monitoring: Enables monitoring of SSL VPN sessions on firewalls, alerting when approaching license limits to prevent downtime due to capacity issues.
-
- Internet connectivity checks: Quickly determines if connectivity problems are network or ISP-related, aiding in fast resolution of common issues like VoIP call failures or video conferencing lag.
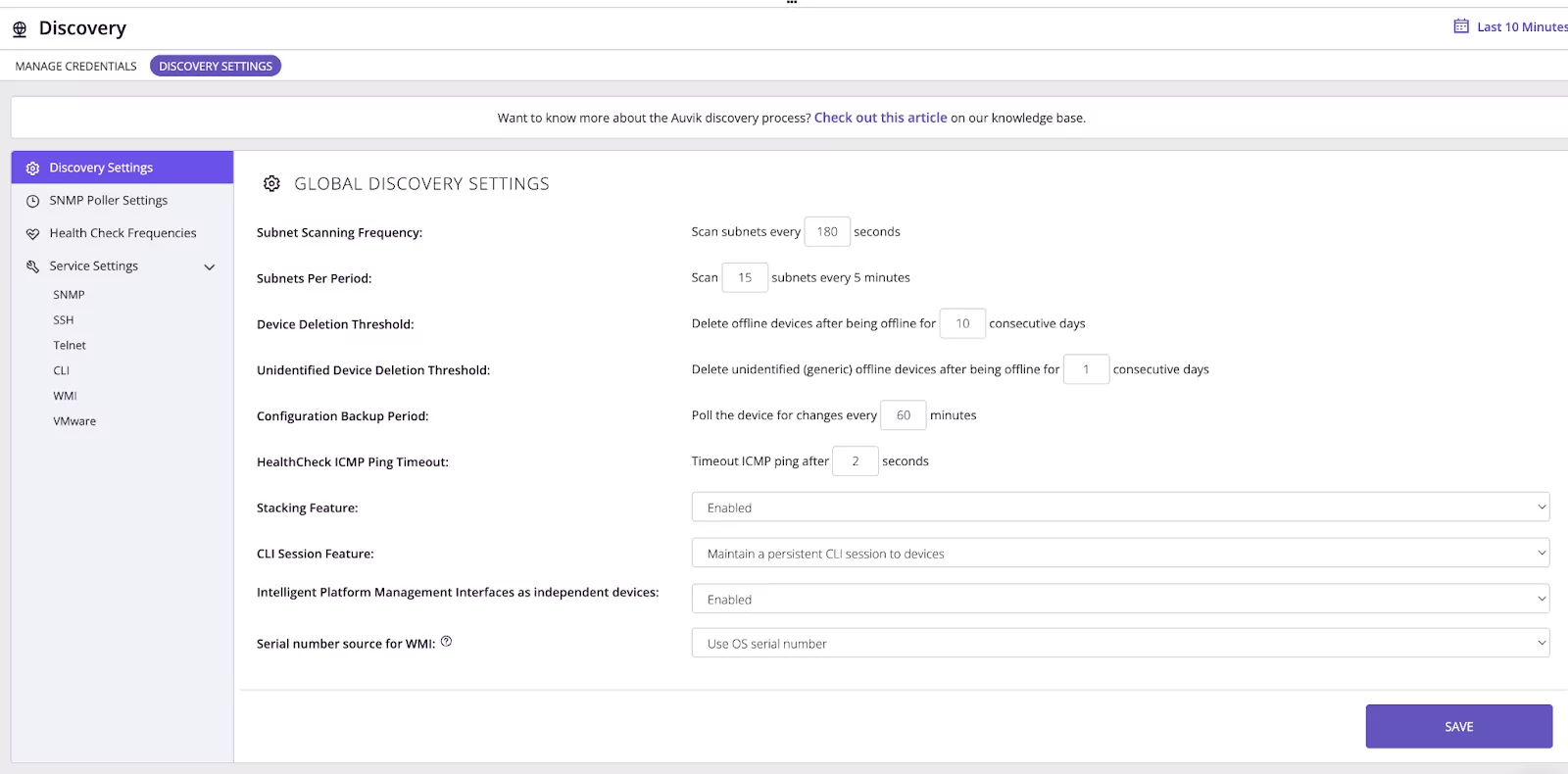
Source: Auvik
8. SysAid

SysAid is an IT service management solution that incorporates a network discovery feature, enabling organizations to automatically identify and catalog connected devices. This tool simplifies the deployment of the SysAid Agent on various operating systems such as Windows, Linux, Mac, and Unix, leveraging agent-based and agentless scanning methods.
Key features:
-
- Network discovery: Utilizes WMI scans and the SysAid Agent for detailed discovery of networked devices. This dual approach ensures accurate asset tracking and inventory management.
-
- Agentless network discovery: Offers an option for agentless discovery using WMI and SNMP protocols to gather full hardware and software inventories without installing agents on devices.
-
- Remote discovery service (RDS): Supports network discovery across remote networks or segments behind firewalls, optimizing communication in large-scale environments.
-
- SysAid agent features: Provides capabilities beyond inventory management such as remote control sessions, chat conversations from service records, and self-service ticket submission with screenshot capture via hotkey (F11).
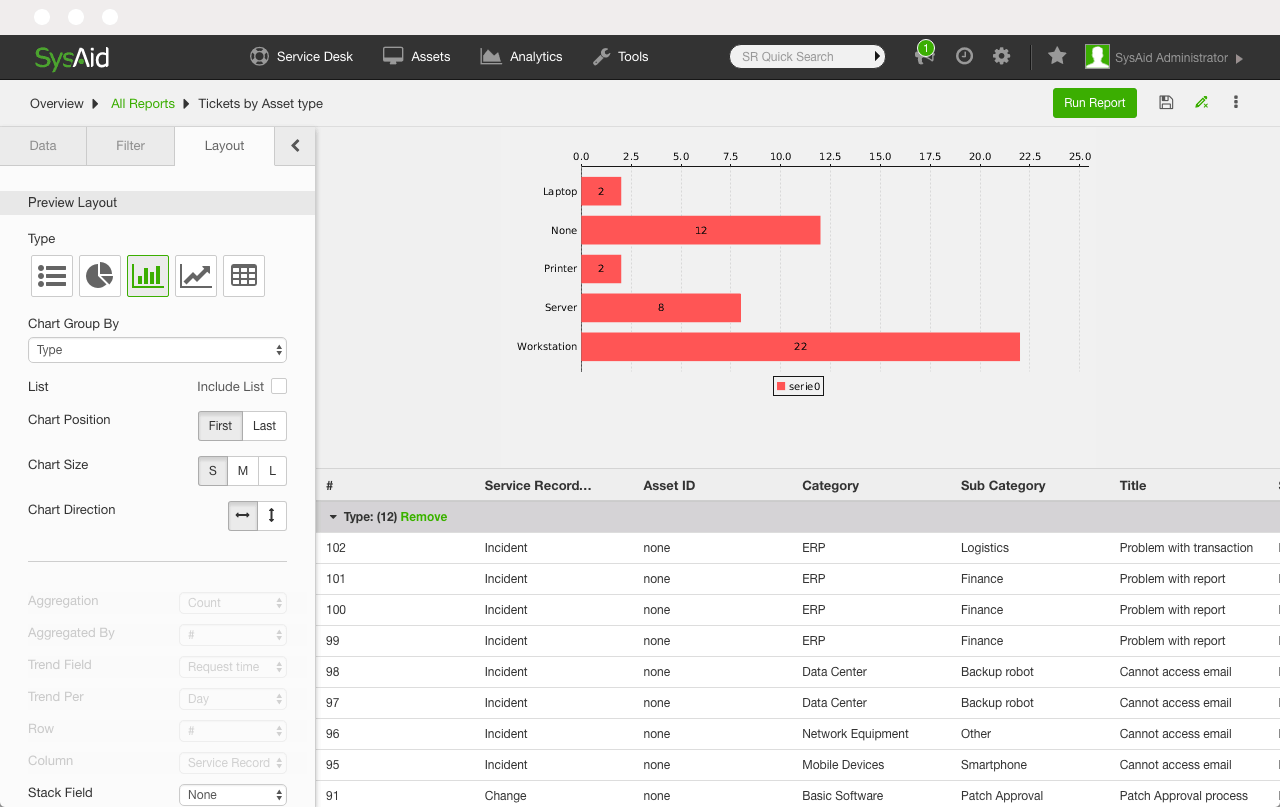
Source: SysAid
9. InvGate Insight

InvGate Insight is an IT asset discovery tool designed to automate the inventory management process across an organization’s network. It identifies and catalogs connected devices, including workstations, servers, mobile devices, and IoT assets, without requiring agent installation. This tool offers visibility into both managed and unmanaged endpoints, enabling detailed analysis and control of IT infrastructure.
Key features:
-
- Automated asset discovery: Automatically discovers and catalogs every device connected to the network, including unmanaged endpoints.
-
- Network scanning: Scans the network to identify assets in both on-premises and cloud environments, centralizing asset data for better visibility.
-
- External discovery sources: Integrates data from external sources such as AWS, Azure, virtual machines, and mobile devices.
-
- Device management: Allows users to select which devices are added to the network inventory and excludes non-essential assets. Provides flexibility in managing network composition.
-
- Security compliance: Identifies unauthorized or rogue devices posing security threats. Enables proactive measures against unpatched devices or outdated software to maintain security compliance.
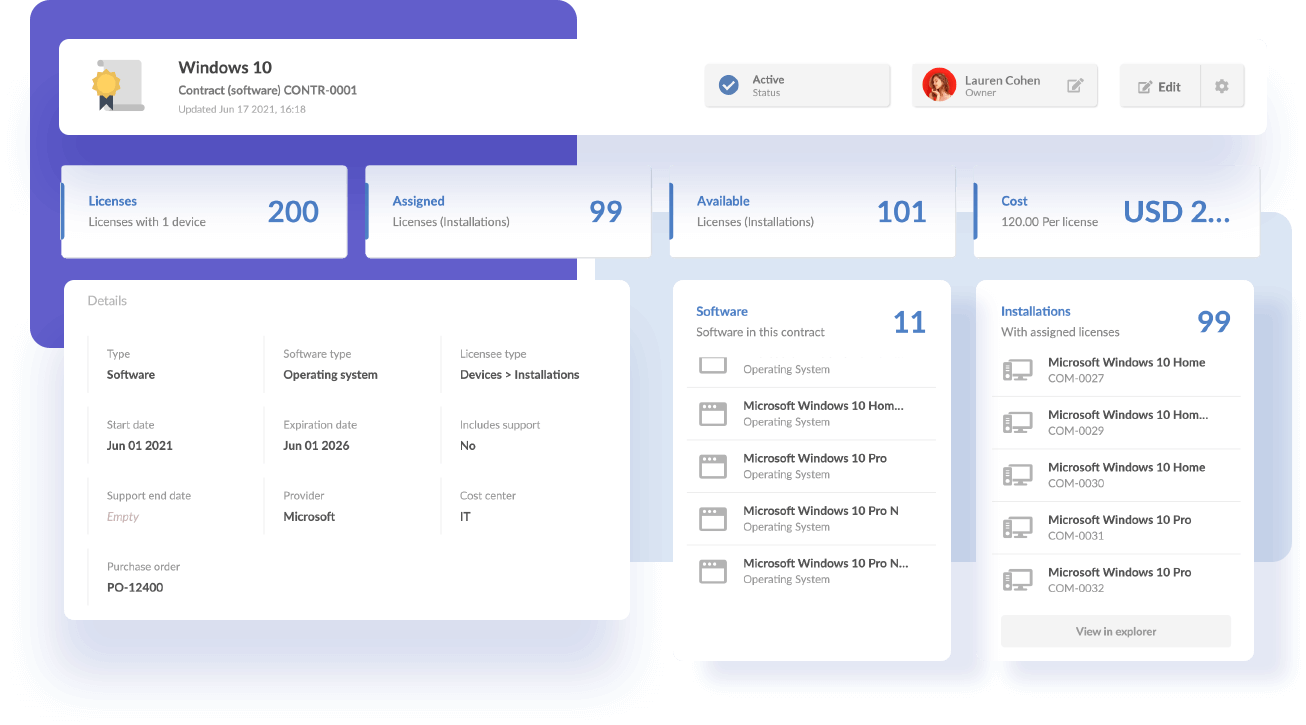
Source: InvGate
Conclusion
Asset discovery tools are essential for maintaining an accurate and comprehensive inventory of an organization’s IT assets. They automate the discovery process, improve security by identifying unauthorized devices, and ensure compliance with regulatory standards. By providing real-time visibility and detailed insights into asset configurations and usage patterns, these tools enable better management and optimization of IT resources.
Learn more about Faddom for asset discovery or start a free trial to the right!