IT departments are managing an ever-growing number of assets, both on-premises and in the cloud. With each new tool and system comes its own naming conventions, making it challenging to track what software and operating systems are in use. Departments often use different systems and standards, leading to confusion and delays in resolving security vulnerabilities. For example, a hospital IT team may need to search through multiple systems to identify which devices are affected by a specific vulnerability, wasting hours and leaving data at risk.
A standardized naming scheme for IT assets—like software, hardware, and operating systems—can streamline workflows and enhance security operations. Among the available options, Common Platform Enumeration (CPE) is one of the most widely used standards.
Table of Contents
ToggleIn this post, we’ll break down how CPE works, the cybersecurity benefits it offers, and a key best practice for getting started.
CPE Structure and Components
All of the naming conventions available today, such as SWID, PURL, and CPE, use a structured, machine-readable format, similar to a web address.
The basic idea behind this format is to let users drill down quickly to identify the exact hardware, software, or operating system in use. This is somewhat like listing a used vehicle for sale by make, model, and year, but for digital assets in which version number can change far more frequently than once a year.
The structure of CPE includes details like vendor, product name, version, and operating system. Together, this structure is known as a well-formed CPE name (WFN), with all the pieces fitting together to complete the puzzle of the organization’s digital landscape.
This is the basic structure of a CPE WFN:
cpe:/{part}:{vendor}:{product}:{version}:{update}:{architecture}:{language}:{modifier}
- part: Defines the type of system detected and can have one of the following values:
- a – for Application
- h – for Hardware
- o – for Operating System
- vendor: The software developer responsible for the product
- product: Name of the product
- version: Version number of the product
- update: Update/revision of the product
- edition: Edition of the product
- language: Language of the product (used only if different language versions are available)
Several other fields aren’t commonly used: sw_edition, target_sw, target_hw, and other. These are usually left blank with a * symbol in the relevant location. As a result, most CPE WFNs have a lot of * symbols.
Here are a few examples of WFNs within CPE. Note that all CPE WFNs begin with “cpe:” followed by the CPE version number, e.g., “cpe:2.3:” This has been omitted from the following examples.
| Well-Formed Name (WFN) | Part | Vendor | Product | Version | Update |
| a:apache:log4j:2.0:-:*:*:*:*:*:* | a | apache | log4j | 2.0 | – |
| a:microsoft:internet_explorer:8.0.6001:beta:*:*:*:*:*:* | a | microsoft | internet_explorer | 8.0.6001 | beta |
| o:redhat:enterprise_linux:4:update4 | o | redhat | enterprise_linux | 4 | update4 |
| h:intel:3450_chipset:-:*:*:*:*:*:*:* | h | intel | 3450_chipset | – |
CPE in Cybersecurity and IT Management
Understanding how CPE works is essential for IT security management. That’s because, in general, a security vulnerability is problematic only for certain versions.
By correlating the CPE information with the Common Vulnerabilities and Exposures (CVE) system, the global vulnerability database maintained by NIST, organizations receive valuable information to help them mitigate or remediate vulnerabilities in their environment.
For example, it’s not enough to know that CVE-2023-36397 is a critical vulnerability (with a CVSS score of 9.8) in the Microsoft Windows Pragmatic General Multicast (PGM) system.
Having to mitigate or patch every single Windows system within a given organization would be far too much work for the IT team. Yet without CPE, that’s exactly what would need to happen. Fortunately, CPE information is included in each CVE, providing essential data on which systems are affected by any given vulnerability, broken down by vendor, product, and version number.
In the example above, for instance, the CVE entry for CVE-2023-36397 lists all specific updates of Windows 10, Windows 11, and Windows Server that are affected by this vulnerability. One of the many vulnerable operating systems is listed as
cpe:2.3:o:microsoft:windows_11_23h2:*:*:*:*:*:*:arm64:*
| Well-Formed Name (WFN) | Part | Vendor | Product | Version | target_hw |
| o:microsoft:windows_11_23h2:*:*:*:*:*:*:arm64:* | o | microsoft | windows_11_23h2 | * | arm64 |
Note that in this case, no version is listed because “23h2” is already part of the product string.
In this way, the CPE provides a unique fingerprint, helping security tools and databases understand an organization’s systems quickly and efficiently to determine which assets need attention when a new vulnerability comes to light.
By correlating vulnerabilities by CVE with affected assets by CPE, organizations can:
- Track vulnerabilities: Identify outdated software and patch it before hackers can exploit it.
- Streamline compliance: Meet security regulations and reporting requirements more easily.
- Automate tasks: Manage complex IT environments with tools that understand CPE language.
This last point is perhaps the greatest benefit of CPE. When used with automated platforms, CPE data enables automated inventory generation for a total picture of the IT infrastructure, simplifying asset management. It also enables pinpoint identification of vulnerable hardware and software and prioritized remediation. Finally, it allows companies to take a proactive approach to threat mitigation, leveraging real-time threat intelligence to preemptively block known vulnerabilities before they can exploit the network.
Further analysis and analytics on CPE data can also help eliminate silos; optimize big-picture processes; assess vendor security track records based on CPE data (guiding procurement and partnership choices); analyze historical trends to anticipate threats; improve compliance with regulations and internal policies for simplified auditing and reporting; and allocate security resources more efficiently, with greater focus on higher-risk devices and vulnerabilities.
Challenges and Limitations of CPE
Obviously, no system is perfect, and CPE faces some challenges. The vector structure can be daunting for beginners; not all vendors or products have valid CPEs, and in the quickly evolving software landscape, keeping up with new software and updates can be a constant struggle. (This is where automation can also play a useful role.) As with any IT transformation, rolling out CPE across an organization can be a complex project that must be undertaken carefully over multiple stages:
Groundwork
Before undertaking any change, IT must perform an inventory of all assets, network mapping. The IT team will also need to determine which CPE data sources will be used, along with the data format selection. The organization will also need to choose which tools it will use to catalog and track its assets by CPE data.
Initial Deployment
A pilot deployment is probably the best way to begin. At this stage, IT will ingest asset data for initial pilot departments and begin configuring security tools to work with the CPE data.
Rollout at Scale
Once the pilot has been tested successfully, the IT team will begin a phased expansion to all departments. At this point, they can also begin setting up automation for common tasks in related security tools—and reaping the benefits described above of standardizing IT asset names.
Ongoing Monitoring
IT personnel will need to assess performance and success metrics in all relevant areas, such as security, while also taking steps towards continuous improvement.
Making the Leap, Avoiding the Pitfalls
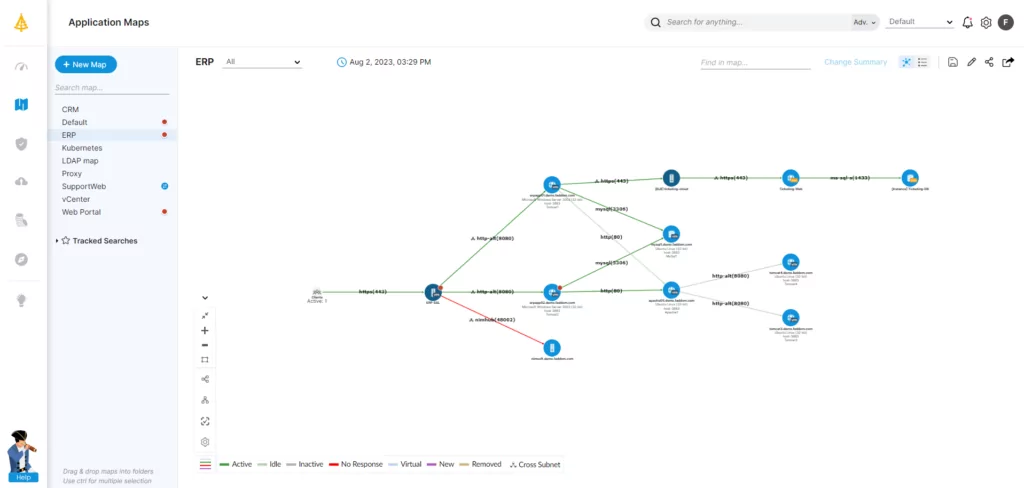
As discussed above, making the leap to CPE can fuel a wide range of associated improvements for IT departments and security teams. But the transition to tracking products and devices using CPE can be challenging.
To make the leap simpler and ensure that no assets fall through the cracks, organizations should begin the transition process with application dependency mapping (ADM). ADM tools build a comprehensive map of applications and their connections, providing crucial visibility before beginning the CPE rollout.
Faddom is a fast, effective way to get started with ADM. With no agents or configuration changes required, Faddom gets to work mapping the entire network—even the most complex dependencies—in under an hour.
In addition to having the world’s fastest and most secure and affordable application dependency mapping platform, Faddom has also released a new cybersecurity module that comes with cutting-edge vulnerability detection, severity scoring, actionable insights – and a lot more. All without using any agents!
To start a free trial today, just fill out the form in the sidebar!









