Microsoft Active Directory grants users access to IT resources, and functions as the gatekeeper for verifying user identity and access permissions. It also routes all the activity on an organization’s network and provides permissions security as defined by administrators.
The Active Directory Migration Tool, also known as ADMT, is a Microsoft-developed solution that aids in the migration of Active Directory AD objects. These objects can include users, computers, groups, and other AD objects from one domain (a logical group of objects within AD) to another. ADMT not only transfers the objects but also preserves the permissions and properties associated with these objects.
ADMT’s main advantage is its ability to restructure your AD environment without significant disruption. The tool uses a method known as SID (Security Identifier) history to ensure that migrated users still have access to resources in the source domain. This means that, as a network administrator, you can run the migration process without worrying about user access issues.
For more information, see The Complete Guide to Application Mapping.
Table of Contents
Toggle- Why Perform Active Directory Migration?
- Why Do You Need Azure Directory Migration Tool? Challenges of Active Directory Migration
- How to Install and Use the Active Directory Migration Tool
- Tips from the Expert
- Best Practices for Running an Active Directory Migration
- How Can IT Infrastructure Mapping Support Active Directory Migration?
- Pre-Migration Application Mapping with Faddom
Why Perform Active Directory Migration?
Organizations undergo AD migrations for a variety of reasons that can include:
- A website domain migration
- Merging two AD environments into one during an M&A process
- Domain controller server upgrades
Any one of these reasons can have an on-premises focus or involve migration from an on-premises Microsoft Active Directory environment to a cloud-based Azure Active Directory environment.
Why Do You Need Azure Directory Migration Tool? Challenges of Active Directory Migration
The general process of AD migration seems simple on the surface with the automated Active Directory migration tool. However, things get much more complex when factoring in the constantly changing devices, databases, applications, and user permissions. There are additional challenges due to shadow IT. Devices can be undiscovered or have outdated permissions in a remote workforce and bring-your-own-device (BYOD) work environment.
Since Active Directory migrations are critical to business operations, the migration process cannot introduce flaws. These could interrupt business operations and lead to major productivity and business process losses.
Data Loss or Corruption
During an AD migration process, it’s possible for data to get lost or corrupted due to network failures, power outages, or other unforeseen issues. Losing critical Active Directory data can have severe consequences, including disrupted operations and loss of business.
To mitigate the risk of data loss or corruption, it’s important to perform regular backups of your Active Directory data before, during, and after the migration process. It’s also advisable to use a reliable migration tool with built-in features to protect data during the migration.
Learn more in our detailed guide to application topology
Compatibility Issues
When undertaking an Active Directory migration, compatibility issues can arise that significantly impact the process. These issues may stem from differences in operating system versions, application requirements, or domain functional levels between the source and target environments. For instance, certain applications integrated with AD may only support specific versions or configurations, leading to challenges in maintaining functionality post-migration.
Moreover, directory schema extensions or custom attributes added to the AD in the source environment may not be present or compatible with the target environment. This can lead to data loss or corruption if not properly handled during the migration.
To mitigate these risks, thorough pre-migration testing and validation of each application and service against the target environment’s specifications are essential. Additionally, ensuring that the target domain meets or exceeds the functional level of the source domain can help avoid compatibility problems. Finally, the Active Directory Migration Tool, which supports schema migration, can avoid schema incompatibility issues.
Shadow IT
Shadow IT refers to information technology (IT) systems and solutions built and used inside organizations without explicit organizational approval. It often arises from employees seeking more efficient ways to complete their work, bypassing IT department protocols and solutions. Migrating Active Directory requires a comprehensive understanding and documentation of all IT assets. Shadow IT complicates this process, as these assets are not always visible to IT administrators, thus risking incomplete migrations or security vulnerabilities.
During an AD migration, discovering and integrating shadow IT into the official IT portfolio can mitigate risks and ensure a more seamless transition. This integration also provides an opportunity to review and potentially adopt innovative solutions that employees have found effective, enhancing overall IT service delivery.
Remote Work and Bring Your Own Device (BYOD)
The rise of remote work and BYOD policies has dramatically changed the landscape of IT infrastructure and security. Remote work allows employees to access corporate resources from anywhere, while BYOD policies enable employees to use personal devices for work purposes. Both trends offer flexibility and productivity benefits but introduce significant challenges for Active Directory migrations.
Ensuring secure and efficient access to resources in a remote or BYOD environment requires meticulous planning and execution. Migrating AD objects must account for diverse device types, operating systems, and network connections, all while maintaining strict security standards to prevent unauthorized access and data breaches.
For successful AD migrations in remote work and BYOD contexts, organizations must adopt robust identity and access management (IAM) solutions, implement multi-factor authentication (MFA), and ensure secure VPN connections or use zero trust network access (ZTNA) models.
How to Install and Use the Active Directory Migration Tool
Before installing the Active Directory Migration Tool (ADMT), you must have an active directory domain in place where ADMT can be installed. The server where ADMT will be installed requires access to both the source and target domains to facilitate the migration process. Ensure the installation server runs a supported version of Windows Server.
After verifying that all prerequisites are met, download the latest version of ADMT from the official Microsoft website. Run the installer on the designated server, following the on-screen instructions to complete the installation. Once installed, ADMT can be accessed through its dedicated console.
To begin using ADMT, start by configuring the tool to connect to both the source and target domains. This involves setting up proper permissions and ensuring connectivity between the two domains.
After configuration, use the ADMT console to select the objects you wish to migrate, specify any special options or mappings, and initiate the migration process. Monitoring the migration through ADMT’s interface allows for real-time tracking and addressing any issues that arise during the migration.

Lanir specializes in founding new tech companies for Enterprise Software: Assemble and nurture a great team, Early stage funding to growth late stage, One design partner to hundreds of enterprise customers, MVP to Enterprise grade product, Low level kernel engineering to AI/ML and BigData, One advisory board to a long list of shareholders and board members of the worlds largest VCs
Tips from the Expert
In my experience, here are tips that can help you better adapt to Active Directory (AD) migration using ADM tools:
-
Conduct a thorough pre-migration assessment
Before starting the migration, perform a detailed assessment of the current AD environment. Identify all dependencies, custom attributes, and critical applications to ensure nothing is overlooked during migration.
-
Utilize a pilot migration
Run a pilot migration with a small, controlled group of users and computers. This helps identify potential issues in a controlled environment, allowing for adjustments before a full-scale migration.
-
Implement role-based access control (RBAC)
Define clear roles and access controls in both source and target domains. This ensures that only authorized personnel have access to migration tasks, reducing the risk of accidental disruptions.
-
Monitor real-time migration logs
Use tools that provide real-time logging and monitoring during the migration process. This enables quick identification and resolution of issues as they arise, minimizing downtime.
-
Plan for rollback scenarios
Develop and test rollback procedures in case the migration encounters critical issues. Having a well-defined rollback plan ensures you can revert to the original state without significant disruptions.
Best Practices for Running an Active Directory Migration
Moving users, computers, and applications to a new domain makes for a complex process. This is because AD migration is a process of migrating a complex AD DS environment that can have thousands of objects and countless attributes and dependencies. Because domain names and directory schemas are the foundation of an organization’s directory, they are difficult to change.
Document the Organization’s Desired End State
Carefully plan the migration and define your use cases to determine which departments are most resilient to possible disruptions. The organization must start with a clear blueprint for its post-migration end state. Group policies, group policy objects, forest, domain-level configuration, applications, and scripts connected to AD may require changes, so current directory configuration analysis is imperative. IT leaders may also need to consider other business and legal requirements that may come into play in M&A.
Clean the Current AD Environment
Mapping of the current IT infrastructure and AD environment will inform the desired state of post-migration AD. This will reveal any areas that need cleanup or right-sizing such as permissions, inactive accounts, etc. It’s important to involve department heads in this process for granular insight that admins can merge into their view.
Have a Rollback and Recovery Plan
It’s imperative to develop a backup, rollback, and recovery plan to move past any problems that occur during the migration process. The process itself should start with a test environment if workable to mirror the production environment before the cutover.
Consider Alternatives for Microsoft ADMT
There are many tools for AD migration, beyond Microsoft Active Directory Migration Tool (ADMT) and Azure AD Connect.
Many organizations use Quest Migration Manager for Active Directory along with BitTitan, AvePoint, CodeTwo, Transcend, SysTools, or Proventeq. Others include SkySync, Tervela, CloudM, SkyKick, Dell SecureCopy, Sys-Manage CopyRight2, NetIQ Domain Migration Administrator, and Binary Tree Migrator Pro.
Make Sure the Discovery Phase is Comprehensive
It’s vital to perform a thorough discovery that includes group policy reviews, device deployment, user/group changes, mailbox provisioning, HR onboarding and offboarding applications, and IT scripts for AD object cleanups. Also, check device registration and management parameters such as encryption settings and VPN certificates.
Organizations should check for SSO, identity access management (IAM), and multi-factor authentication for possible upgrade needs. They should also look for shadow IT and any non-Windows systems that may rely on AD.
Develop an Active Directory Checklist
As part of your Active Directory migration strategy, every organization should develop an AD migration checklist. This provides an ongoing guide to ensure that the organization doesn’t overlook any aspects of the process.
The following checklist, as recommended by Microsoft, is a good start when planning your Active Directory migration:
- List of requirements to migrate
- Existing AD health check
- Migration plan
- Check of all physical and virtual resources for the domain controller
- Windows Server 2022 Standard installed
- Windows update patches applied
- Dedicated domain controller IP address
- AD DS role installed
- Application and server roles migrated from existing domain controllers
- FSMO roles migrated to new domain controllers
- New domain controllers added to monitoring system and DR solution
- All old domain controllers decommissioned
- Functionality of domains and forests optimized
- Maintenance schedule for review of group policy, new features, and AD infra fixes
This checklist is a reminder of each primary step in the Active Directory migration, which should be backed by detailed processes in the full plan and strategy. While each step in the checklist and the plan is crucial, their success and that of the overall migration hinges on the comprehensive discovery and mapping of the objects and dependencies in the IT infrastructure.
How Can IT Infrastructure Mapping Support Active Directory Migration?
Even the most comprehensive migration tool cannot ensure the discovery of all aspects of the environment as part of the migration process. Therefore, mapping IT infrastructure is paramount to success with an automated mapping and discovery tool. Devices may not be visible when they are using an old or incorrect domain controller, but the right network mapping tool and IT infrastructure mapping tool can reveal them.
The evolution of business operations, devices, users, applications, and access permissions is an ongoing part of every organization. This makes having a standalone, cloud-based discovery and mapping solution necessary to help the organization and IT stay one step ahead of changes.
The right tool can inform service mapping and discovery to help with the most crucial parts of AD DS, which are SSO, IAM, and permissions. The goal is to make sure that applications dependent on security management from Active Directory are visible, accurate, and in place, so users have the right post-migration access.
Applications may rely on service accounts like SQL servers for database access, so the apps must be able to see these changes. Other applications like OKTA have standalone ecosystems that link to Active Directory, so manual changes to maintain access may be necessary.
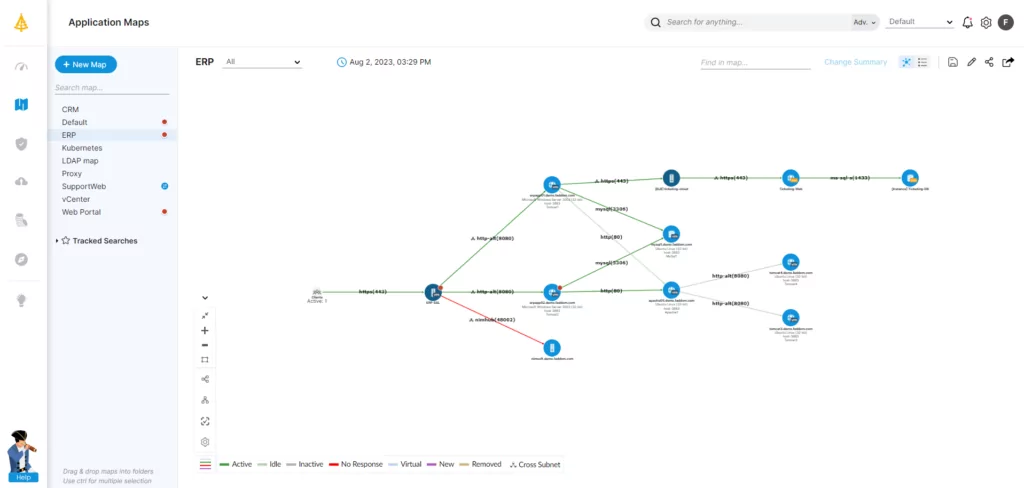
Pre-Migration Application Mapping with Faddom
Faddom is an agentless IT infrastructure discovery and mapping solution which makes sure that every device, object, and dependency is visible before Active Directory migrations. This is critical to prevent outages, which can occur when some servers are still using the old AD server. Faddom provides the data necessary for a smooth migration, with ongoing visibility of on-premise and cloud-based infrastructure.
Faddom offers the fastest mapping capabilities in the market: it takes under an hour to map your entire infrastructure. It is fully agentless, making it highly secure, and is also affordable, starting at $10K/year.