What Are Network Security Solutions?
Network security solutions include various policies, techniques, and technologies designed to protect the integrity, confidentiality, and availability of computer networks and data. These solutions aim to guard against unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure.
As networks grow, combining on-premises infrastructure with cloud services, these security measures become more crucial in managing complex cybersecurity threats. The evolution of network security has been driven by the increasing sophistication of attacks and regulatory requirements, requiring continuous adaptation and improvement of protection strategies.
Table of Contents
ToggleToday, network security solutions extend beyond basic firewall and antivirus setups. They integrate advanced detection systems, behavioral analytics, and policy enforcement across a myriad of devices. Organizations must encapsulate a multi-layered security strategy to defend against both external intrusions and insider threats.
Types of Network Security Solutions and Technologies
Network Monitoring and Scanning
Network monitoring tools continuously observe network traffic, device behavior, and performance metrics to detect anomalies, performance issues, or signs of compromise. These systems collect logs and telemetry from switches, routers, and endpoints to provide real-time visibility, enabling early threat detection and incident response.
Network scanning technologies identify active devices, open ports, running services, and known vulnerabilities. Regular scanning helps assess the attack surface, detect unauthorized assets, and validate compliance with security policies. When integrated with asset management and threat intelligence, scanning tools support proactive risk mitigation.
Next-Generation Firewalls (NGFW)
Next-generation firewalls (NGFW) represent a leap forward from traditional firewall systems. They incorporate in-depth traffic inspection capabilities, application awareness, and integrated intrusion prevention. By doing so, they offer a more nuanced approach to threat detection and control, accommodating the dynamic nature of modern threats.
NGFWs utilize advanced intelligence to decipher encrypted threats and automate responses, reducing the manual effort required for network defense. Integration with threat intelligence feeds provides real-time updates on potential vulnerabilities, ensuring proactive threat management. Organizations benefit from improved visibility into network traffic patterns, allowing for comprehensive monitoring and precise security policy implementation.
Network Access Control (NAC)
Network access control (NAC) is crucial for managing network integrity by regulating device access based on compliance with security policies. NAC solutions assess devices seeking network entry, ensuring they meet defined security criteria before granting access. This vetting process helps prevent unauthorized devices from connecting and potentially compromising network security.
NAC is particularly effective in governing network access in environments with diverse device profiles, such as bring-your-own-device (BYOD) environments. By implementing granular access controls, NAC can enforce network segmentation, isolate non-compliant devices, and integrate seamlessly with broader security frameworks.
Remote Access VPN
Remote access VPNs provide secure connectivity for remote users, extending the corporate network’s security perimeter beyond physical office confines. By encrypting data in transit, these VPNs ensure that remote communications remain confidential and secure from eavesdropping. This function is especially vital in mobile work environments, where employees need reliable access to corporate resources from any location.
In addition to enabling secure remote access, VPNs support compliance with security standards by protecting sensitive data and supporting multi-factor authentication (MFA) measures. By doing so, they ensure that users accessing network resources are authenticated and data integrity is maintained. Remote Access VPNs are integral to continuity planning, enabling business operations during disruptions by allowing employees to work securely.
Network Segmentation
Network segmentation divides a network into smaller, isolated sections to improve performance and security. It allows administrators to apply security controls to each segment, limiting the lateral movement of threats across the network. This isolation is effective in minimizing the potential impact of a security breach, as attackers are confined to a segmented area rather than gaining full network access.
Segmentation also supports compliance by restricting data access based on regulatory requirements. By categorizing devices and users into segments based on function or trust level, organizations can better control access, reduce congestion, and bolster protection against internal and external threats.
Intrusion Prevention Systems (IPS)
Intrusion prevention systems (IPS) actively monitor network traffic for signs of malicious activities, offering protection by preemptively blocking threats. Unlike Intrusion Detection Systems, which only alert administrators of potential breaches, IPS solutions halt malicious activities in real time.
An IPS can be configured to take various actions based on defined security policies, such as blocking source IP addresses, dropping malicious packets, or logging incidents for further analysis. With continuous updates from threat intelligence sources, IPS systems stay ahead of emerging threats and vulnerabilities.
Zero Trust Network Access (ZTNA)
Zero trust network access (ZTNA) is a security model that challenges the traditional perimeter-based security approach by eliminating the notion of implicit trust. ZTNA enforces strict identity verification and access controls at every network layer. Instead of assuming internal network traffic is safe, ZTNA operates on the principle of “never trust, always verify.”
By extending granular security policies and micro-segmentation, ZTNA provides secure access to applications and data both on-premises and in the cloud. This eliminates lateral movement inside the network, a common tactic used in cyber-attacks.
Network Monitoring and Scanning Tools
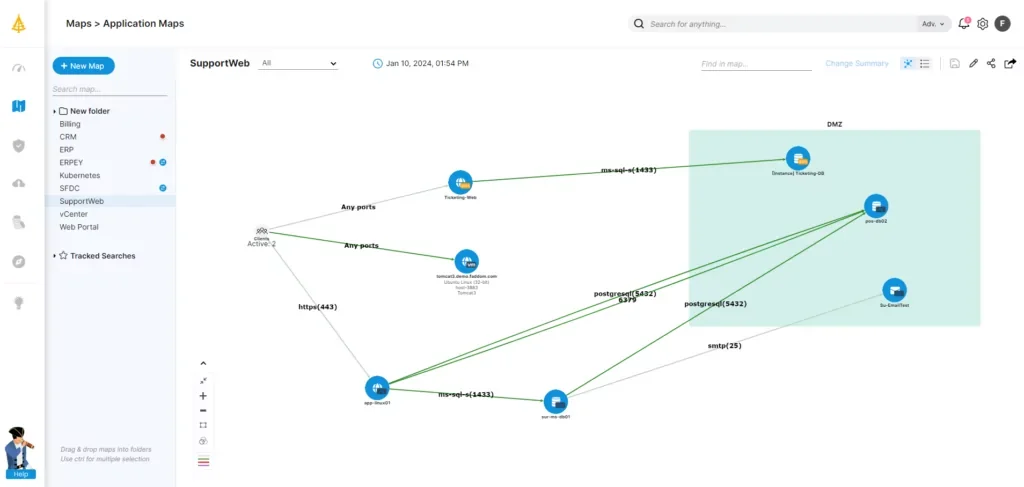
1. Faddom

Faddom is an agentless application dependency mapping and anomaly detection platform that helps organizations in securing their networks by identifying hidden risks in real-time. Rather than depending on complex configurations, it automatically maps all servers, applications, and traffic flows across hybrid environments. This enhanced visibility enables IT and security teams to detect risky east-west traffic, shadow IT, and unauthorized connections that traditional perimeter tools may overlook.
Key features include:
- Agentless & Fast Deployment: Complete infrastructure visibility in under 60 minutes without agents or disruptive configurations.
- Real-Time Application Maps: Continuously updated topology maps reveal servers, business apps, and dependencies for accurate documentation and troubleshooting.
- Segmentation & Security: Identify risky traffic patterns and support micro-segmentation strategies to enhance defenses against lateral movement.
- AI-Powered Anomaly Detection: Lighthouse AI detects unusual traffic behaviors, such as DoS attacks and rogue connections, without the need for manual threshold settings.
- Compliance & Governance: Clear visibility into communication flows to help meet security and regulatory requirements.
Discover more on how Faddom can enhance your network security strategy!
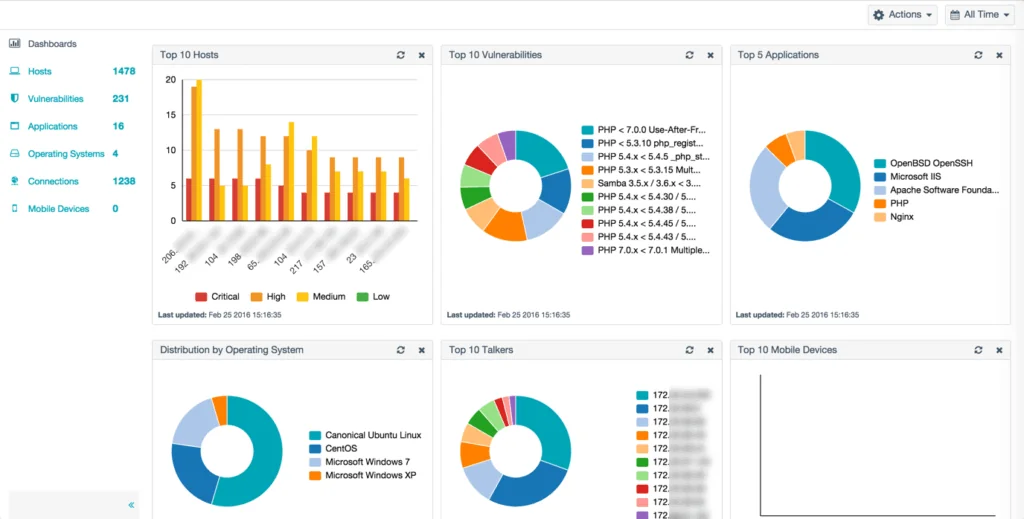
2. Nessus Network Monitor

Tenable Nessus Network Monitor delivers passive visibility across the network, uncovering both managed and unmanaged assets. By analyzing network traffic at the packet level, it continuously identifies vulnerabilities, applications, trust relationships, and potential security risks—especially in environments where traditional scanning methods may be too intrusive.
Key features include:
- Continuous monitoring: Provides passive deep packet inspection, allowing organizations to detect vulnerabilities without affecting system performance.
- Asset discovery: Automatically uncovers devices across IT, OT, virtual, cloud, and mobile environments—including endpoints, servers, databases, network gear, BYOD, and jailbroken iOS devices.
- Vulnerability detection: Identifies both server- and client-side vulnerabilities on communicating systems, including those on transient or newly connected assets.
- Threat and traffic analysis: Flags unauthorized behavior such as internal port scanning, subverted applications, or unencrypted sensitive data in transit, while mapping all encrypted and interactive sessions.
- Compliance support for PCI DSS: Helps maintain integrity of the cardholder data environment (CDE) by detecting undocumented data flows and unencrypted payment card information.
Source: Tenable
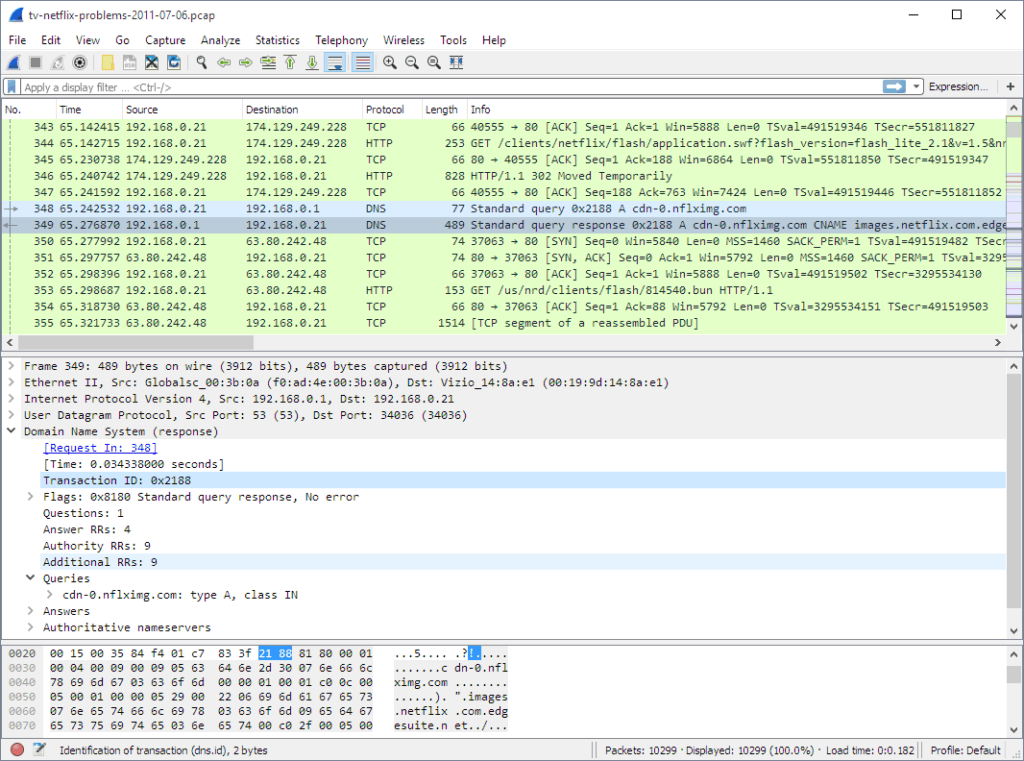
3. Wireshark

Wireshark is an open-source network protocol analyzer, enabling inspection of live and recorded network traffic across hundreds of protocols. It provides insight into what’s happening on a network at a granular level.
Key features include:
- Protocol support: Performs analysis on hundreds of protocols, with ongoing community-driven updates adding support for new and emerging standards.
- Live capture and offline analysis: Can capture real-time traffic or open previously recorded packet capture files (pcaps).
- Cross-platform compatibility: Available on Windows, macOS, Linux, and FreeBSD.
- Graphic interface: The three-pane GUI allows users to navigate captured traffic, while filtering and search tools enable data extraction.
- Display filters: The display filtering system allows users to isolate packets of interest.
Source: Wireshark
4. Nmap

Nmap (Network Mapper) is an open-source network scanning tool for mapping networks and discovering hosts and services. Created by Gordon Lyon (Fyodor), Nmap helps administrators and security professionals audit systems by analyzing how devices respond to crafted network probes.
Key features include:
- Host and service discovery: Identifies live systems, open ports, and running services across networks, using a combination of TCP, ICMP, and other protocol requests.
- Port scanning: Performs scans to enumerate open ports on target machines.
- Version and OS detection: Uses response analysis and TCP/IP fingerprinting to determine the software version and operating system running on a target.
- Nmap scripting engine (NSE): Allows users to run custom or pre-written Lua scripts to perform tasks like vulnerability detection, brute-force attacks, and backdoor discovery.
- Flexible output and reporting: Returns scan results in various formats, including plain text, XML, and grepable output.
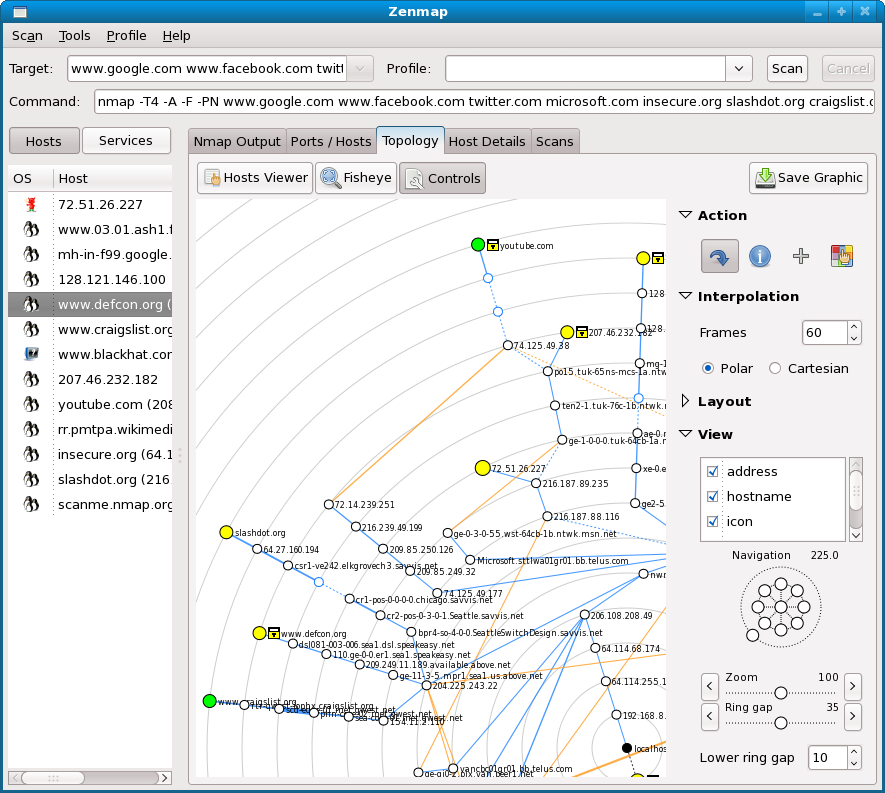
Source: Nmap
5. ZMap
ZMap is a high-speed, open-source network scanner for Internet-wide surveys and large-scale security research. Developed as a faster alternative to Nmap, it can scan the entire IPv4 address space in minutes using commodity hardware.
Key features include:
- Fast scanning: ZMap can scan the IPv4 address space on a single port in 44 minutes using a 1 Gbps connection—or under 5 minutes with a 10 Gbps setup.
- Stateless architecture: Avoids performance bottlenecks by sending probes to each IP address only once and not awaiting individual replies.
- Randomization: Uses cyclic multiplicative groups to pseudorandomly iterate through the IPv4 space, ensuring even probe distribution.
- Minimal overhead: The scanning process avoids the overhead of maintaining large response logs during the scan itself, which allows for high-speed execution with low resource consumption.
- Internet-wide research: Has been used to identify vulnerable IoT devices, track SSL/TLS key weaknesses, and estimate infrastructure outages—such as during Hurricane Sandy.
Network Perimeter Tools
6. Palo Alto Networks NGFW

Palo Alto Networks Next-Generation Firewalls (NGFWs) are intended to support proactive security through the integration of inline deep learning and automation. These ML-powered firewalls extend beyond traditional rule-based detection by analyzing data to identify unknown and evasive threats, such as zero-day attacks.
Key features include:
- Inline deep learning: Applies inline deep learning to detect and stop threats without relying solely on signature-based methods.
- Zero-delay signatures: Every internet-connected NGFW in a network is updated within seconds.
- IoT device visibility: Built-in machine learning capabilities identify and profile IoT devices.
- Operational efficiency with AIOps: Predictive analytics optimize firewall performance, helping reduce downtime and improve ROI.
- Coverage: The NGFW platform protects various environments—branch offices, campuses, data centers, public clouds, and 5G networks—with policy enforcement.

Source: Palo Alto Networks
7. Fortinet FortiGate

Fortinet FortiGate Next-Generation Firewalls (NGFWs) deliver security for hybrid environments through purpose-built hardware and AI-powered threat intelligence. They are built on Fortinet’s proprietary security processing units (SPUs), which offer speed and scalability in inspecting encrypted traffic, managing applications, and enforcing policies.
Key features include:
- Security hardware: Custom ASIC chips—including the NP7, CP9, and SP5 processors—enable high throughput, low latency, and energy efficiency.
- AI-powered protection: Backed by FortiGuard Labs, leveraging AI-driven threat intelligence to detect and prevent threats.
- Unified platform with FortiOS: A single operating system manages security across physical, virtual, and cloud deployments.
- Scalable performance: The FortiGate 200G series, powered by the SP5 chip, helps boost intrusion prevention throughput.
- Integrated ZTNA and SD-WAN: Capabilities like zero trust network access (ZTNA) and secure SD-WAN ensure secure, reliable connectivity across distributed workforces.

Source: Fortinet
8. Cisco Secure Firewall

Cisco Secure Firewall delivers adaptive protection for distributed environments—supporting secure access to applications, data, and infrastructure across hybrid and multicloud deployments. It enables organizations to anticipate threats, respond, and simplify security operations at scale.
Key features include:
- Unified security policy management: Centralizes policy control across physical, virtual, and cloud environments.
- Zero trust capabilities: Supports microsegmentation and identity-based access.
- High-visibility threat intelligence: Offers access to Cisco Talos threat intelligence, drawing from global signals.
- Orchestration with SecureX: Entitlement to Cisco’s SecureX platform boosts operational efficiency by integrating threat detection, response, and automation.
- Scalable deployment options: Options range from the 1000 Series for small offices to the 9300 Series for high-performance data centers and service providers.

Source: Cisco
9. Snort

Snort is an open-source network intrusion detection and prevention system (IDS/IPS) developed by Cisco and originally created by Martin Roesch in 1998. It is widely used for traffic analysis, packet logging, and threat detection across IP networks.
Key features include:
- Real-time threat detection: Analyzes live network traffic to identify suspicious patterns such as malware activity, intrusion attempts, and reconnaissance behaviors.
- Multiple operating modes: Can operate in three modes—sniffer mode for real-time packet capture, packet logger mode for logging packets to disk, and network intrusion detection mode, which compares traffic against user-defined rule sets to trigger alerts or defensive actions.
- Deep packet inspection and protocol analysis: Performs protocol analysis and content-based inspection, allowing for detection of anomalies, exploits, and policy violations.
- Rule-based engine: A rule system enables users to define custom rules tailored to threats or compliance requirements.
- Threat coverage: Snort can detect a range of attacks, including buffer overflows, semantic URL attacks, SMB probes, and stealthy reconnaissance techniques.
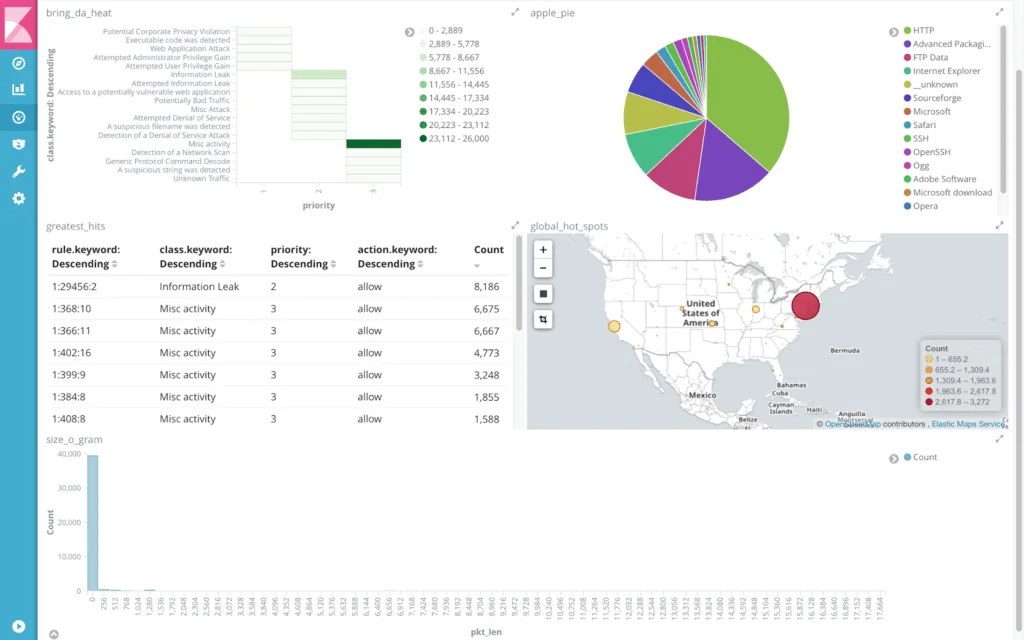
Source: Snort
Zero Trust and Microsegmentation Tools
10. Zscaler Zero Trust Exchange

Zscaler Zero Trust Exchange is a cloud-native platform for digital and distributed enterprises. Designed to replace legacy firewalls and VPNs, the platform minimizes risk, reduces complexity, and improves user experiences by brokering secure, identity-based connections directly between users and applications.
Key features include:
- Zero trust-first architecture: Acts as a switchboard that connects users to applications based on identity, context, and business policy—without placing users on the network.
- End-to-end threat protection: Provides TLS/SSL traffic inspection and threat detection, preventing compromise and blocking malware and ransomware across traffic.
- Lateral movement prevention: Eliminates network-level access, which stops attackers from moving laterally once inside.
- Data loss prevention: Built-in controls identify and secure sensitive data across various states—whether in motion, at rest, or in use.
- Cloud-native scalability: Supports dynamic workforces, workloads, and IoT/OT environments with infrastructure that adapts to business needs.
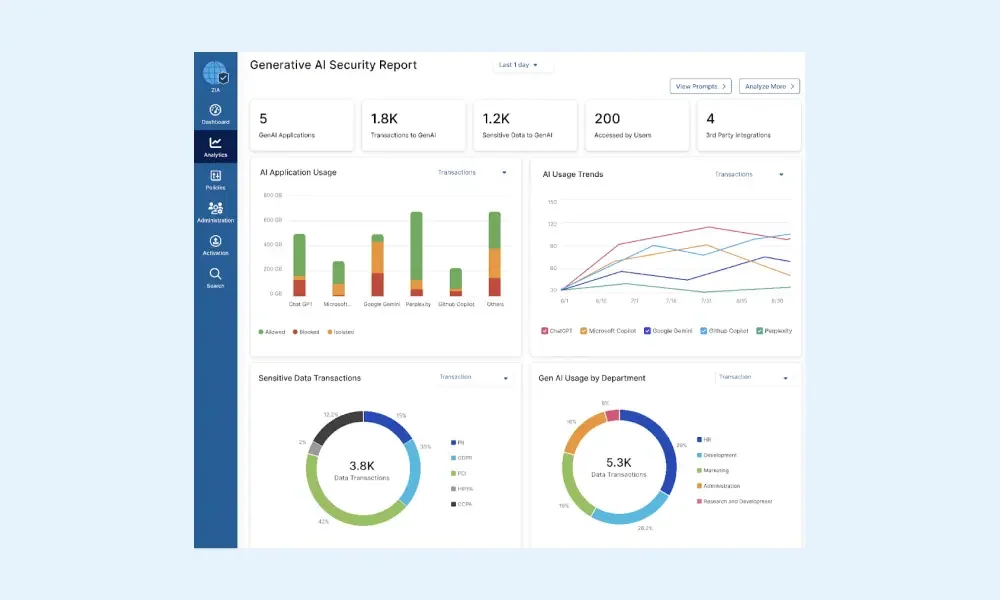
Source: Zscaler
11. Illumio

Illumio provides microsegmentation capabilities that limit lateral movement across hybrid and multicloud environments. It segments workloads and devices based on visibility into traffic flows, enabling organizations to isolate high-value assets and restrict access based on application context rather than network topology.
Key features include:
- Application dependency mapping: Visualizes communications between workloads to identify unnecessary or risky connections.
- Policy-based segmentation: Applies granular segmentation rules across data centers, clouds, and endpoints without requiring changes to the underlying network.
- Breach containment: Limits the spread of ransomware or unauthorized access by preventing lateral movement between compromised systems.
- Platform coverage: Supports environments including Linux, Windows, containers, and Kubernetes, across public cloud, private cloud, and on-premises infrastructure.
- Zero trust alignment: Enforces least-privilege access using identity, role, and workload behavior rather than IP addresses.
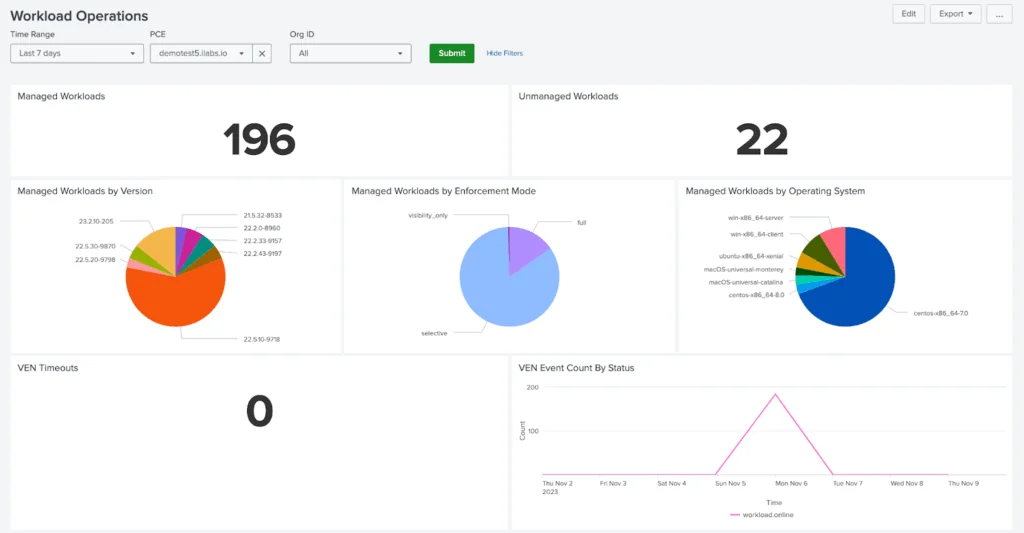
Source: Illumio
12. Akamai Guardicore Segmentation

Akamai Guardicore Segmentation is a software-defined microsegmentation solution designed to contain breaches and reduce attack surfaces in complex IT environments. It provides visibility into application dependencies and enforces granular access policies without requiring network redesign.
Key features include:
- Flow visualization: Maps traffic flows between workloads, applications, and systems to identify risk and support policy creation.
- Granular policy enforcement: Implements segmentation rules based on users, roles, processes, and labels rather than IP or VLAN-based controls.
- Support for diverse environments: Works across hybrid cloud, on-premises data centers, containers, and legacy systems.
- Rapid incident response: Isolates compromised systems quickly to contain threats without disrupting business operations.
- Integration with identity systems: Supports enforcement tied to Active Directory, Okta, and other identity providers for user-based access control.
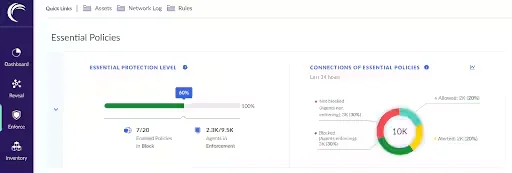
Source: Akamai
Conclusion
As cyber threats continue to grow in complexity and frequency, organizations must adopt a comprehensive, layered approach to network security. By combining advanced technologies, proactive policies, and continuous monitoring, businesses can better defend against both known and emerging threats. A strong network security strategy not only protects critical assets but also ensures regulatory compliance and supports long-term operational resilience.