
Monitoring Meets Mapping: Faddom Now Has a Zabbix Integration
We’re excited to announce that
IT Academy
Guides and Whitepapers
Meet Faddom
Matt Mauchley
Systems Engineer Manager, CHG Healthcare
Pricing
Managing cybersecurity is an ongoing battle against constantly evolving threats and expanding attack surfaces.
Without a comprehensive real-time view of your infrastructure, how can you effectively enforce
micro-segmentation, prioritize vulnerabilities, or
identify unexpected risks before they lead to breaches?
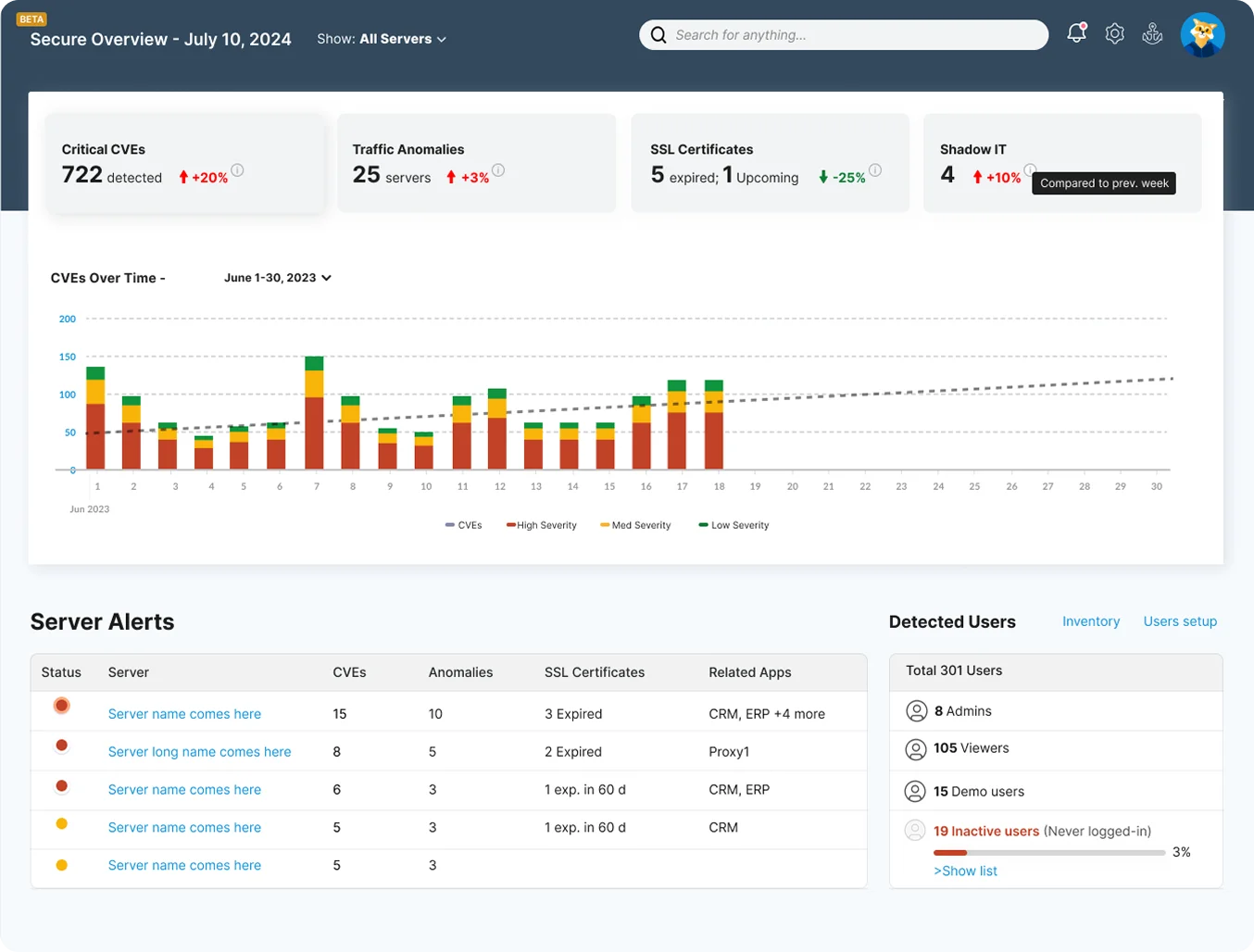

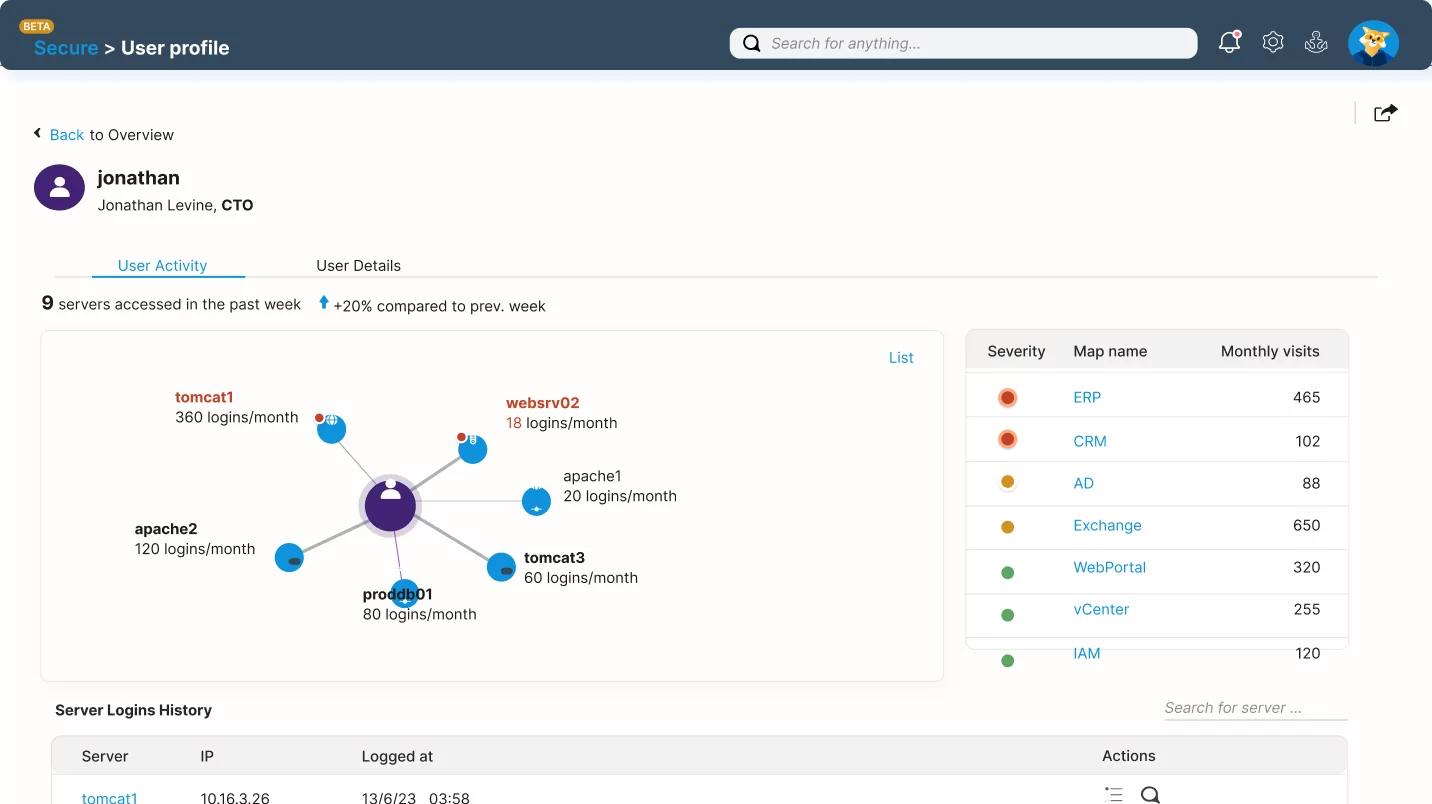
A single unknown connection can become an entry point for cyber threats. Security teams struggle to detect vulnerabilities, enforce policies, and prevent breaches without complete visibility into your network. Hidden dependencies and misconfigurations increase risk, making it challenging to maintain a strong security posture. Common security challenges include:
Faddom’s agentless, non-intrusive platform provides real-time and complete visibility into network connections and dependencies, helping organizations strengthen their security posture and maintain compliance in minutes.
Its unique scoring mechanism simplifies complex network activity into actionable insights, prioritizing risks based on severity to help teams first address the most critical threats.
Whether planning micro-segmentation or reinforcing security policies, it gives teams the clarity and control to proactively stay ahead of evolving threats.

Schedule an IT consultation with our expert team to explore how
Faddom can transform your Network Security!
Map all your on-prem servers and cloud instances, applications, and dependencies
in under 60 minutes.
Get a 14-day FREE trial license.
No credit card required.
