What Is Nmap (Network Mapper)?
Nmap, short for Network Mapper, is an open-source network scanning tool widely used in cybersecurity, network administration, and system auditing. Originally designed for Linux, it is now cross-platform, supporting major operating systems like Windows and macOS.
Nmap’s primary function is to discover hosts and services across large-scale computer networks, identify open ports, detect security risks, and assist in asset management through fast, flexible scanning techniques. Over time, Nmap has evolved from a basic port scanner to a comprehensive network exploration and security assessment suite.
Nmap offers both command-line and graphical user interfaces, making it accessible for users with varying technical backgrounds. Its extensibility through scripting supports complex automation needs and specialized tasks, reinforcing its role as a cornerstone in vulnerability assessments, penetration testing, and routine network inventory activities.
Table of Contents
ToggleKey Features and Functionalities of Nmap
1. Host Discovery / Network Discovery
Host discovery, also known as network discovery, is one of Nmap’s core features. It enables administrators to find live hosts on a network by sending various probe packets (such as ICMP echo requests, TCP SYN, or ARP requests) to targeted address ranges. This capability ensures that only responsive systems are scanned further.
In addition, Nmap supports multiple discovery techniques for environments with restrictive firewall rules or non-standard configurations. By combining different packet types and adjusting timing parameters, Nmap maximizes the likelihood of detecting active nodes even when network defenses try to mask them.
2. Port Scanning
Port scanning is arguably Nmap’s most recognized functionality. Through this process, Nmap determines which network services are accessible on a target by probing the status of thousands of TCP and UDP ports. Nmap supports multiple scanning methodologies, such as SYN scan (stealth), connect scan, and UDP scan, each tailored for specific operational contexts, speed requirements, and permission levels.
Effective port scanning provides critical insight into a network’s attack surface by revealing services that may be susceptible to exploitation, misconfiguration, or unauthorized exposure. Nmap allows customizable scan options to refine accuracy and throughput, enabling operators to balance stealth, comprehensiveness, and performance.
3. Operating System and Device Fingerprinting
Nmap can deduce operating system platforms and sometimes device types using OS fingerprinting. This technique analyzes network responses to specially crafted probes, matching them against a regularly updated database of known behaviors for various operating systems and devices.
The results provide OS identification and often granular details like kernel versions and device roles. By correlating detected services and their hosting platforms, security professionals can prioritize risks, track unauthorized devices, and gain a nuanced understanding of their network environment.
4. Nmap Scripting Engine (NSE)
The Nmap Scripting Engine (NSE) significantly expands the tool’s capabilities beyond basic scanning, allowing users to write or utilize scripts for automation, deeper analysis, and active response. NSE leverages the Lua scripting language, enabling custom test development, exploitation checks, vulnerability detection, and even more advanced tasks like brute-forcing or protocol emulation.
NSE is organized into script categories such as “safe,” “intrusive,” “vuln,” and “auth,” enabling users to control risk and resource consumption in script selection. This engine lets Nmap perform a wide array of functions, from banner grabbing to SSL/TLS certificate validation, on a per-service basis.
5. Scan Result Comparison (Ndiff) and Scripting Automation
Ndiff is a utility that comes with Nmap, designed to compare network scan outputs from different time points. By highlighting added, removed, or changed hosts and services, Ndiff enables administrators to monitor changes in network exposure and service availability effectively. This enables audit compliance, incident response, and ongoing asset tracking by flagging new vulnerabilities or unauthorized modifications.
Automating scans and result analysis is critical for maintaining security in dynamic environments. Nmap’s scripting ecosystem, in conjunction with Ndiff, allows integration into scheduled tasks, CI/CD pipelines, and custom alerting workflows. Security teams can build proactive monitoring systems or integrate scan data into broader SIEM and incident management solutions.
Quick Tutorial: Getting Started with Nmap
Before diving into scans and scripting, it’s important to ensure Nmap is installed and working correctly on your system. Many Unix-based distributions already include Nmap or offer it via package managers, though it may not be installed by default. To check, open a terminal and run:
nmap –version
If Nmap is installed, this will return version information. Otherwise, you’ll see an error like “command not found.” Even if Nmap is present, consider downloading the latest version from the official Nmap site, as it often includes updated detection databases and performance improvements.
Nmap supports both command-line and graphical interfaces. The command-line version is widely used for scripting and automation. However, users who prefer a GUI can use Zenmap, the official graphical frontend. Zenmap simplifies scan configuration and offers visual tools for browsing and filtering results.
To install Nmap, choose from pre-built packages or source code:
-
- Windows: Use the NSIS installer
-
- Linux: Install via RPM or compile from source
-
- macOS: Use the .dmg installer
Make sure to verify the integrity of your downloads. Nmap provides PGP signatures and cryptographic hash files (MD5, SHA1, SHA256) to confirm the authenticity of its packages. Use GPG to verify signatures or tools like sha256sum to compare checksums.
For those who want access to the latest development features, Nmap’s source code is also available via Subversion (SVN). This option is best for contributors or advanced users who need fixes before official releases.
Once installed, you can begin scanning with simple commands. For example:
nmap scanme.nmap.org
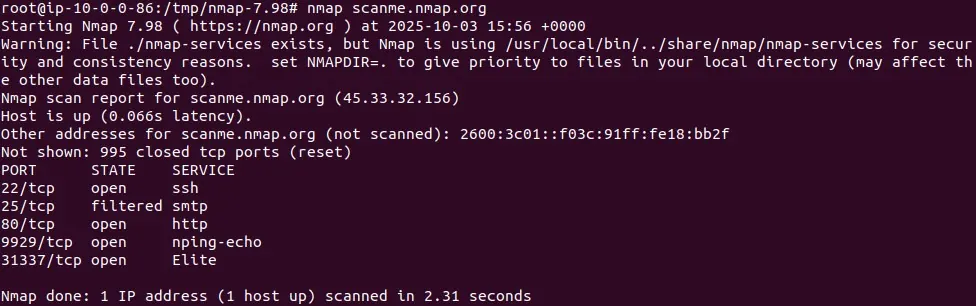
This scans a test server provided by the Nmap project and demonstrates basic functionality. As you explore more features, like port scanning, OS detection, or using the scripting engine, both the CLI and Zenmap provide flexible ways to analyze your network.
Installing Nmap on Linux and Unix systems
Start by downloading the latest Nmap release from the official site (https://nmap.org/download.html). Choose either the .tar.bz2 or .tgz archive format.
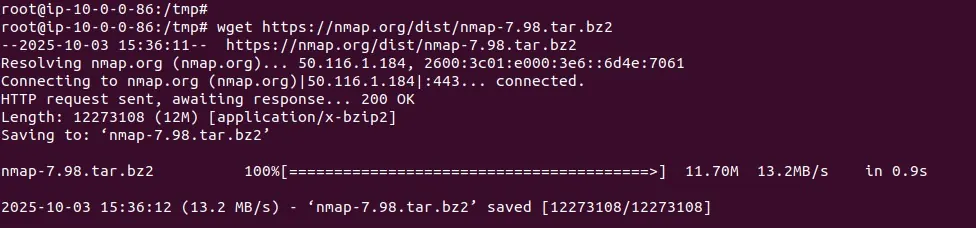
To extract the archive, use:
tar xvjf nmap-.tar.bz2
or, for gzip-compressed files:
tar xvzf nmap-.tgz
Then move into the source directory:
cd nmap-<VERSION>
Run the configuration script to detect system features and prepare the build:
./configure
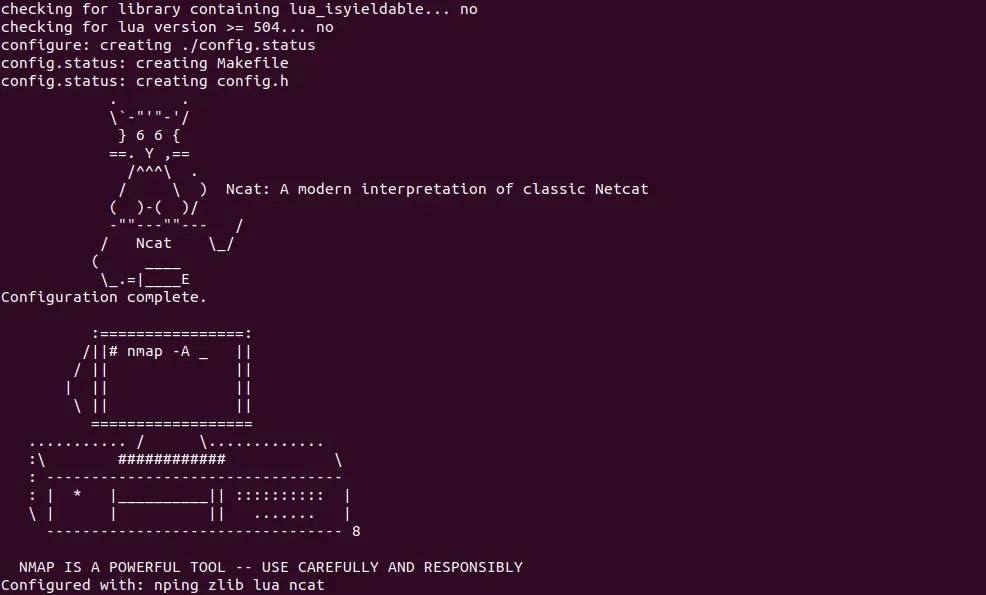
If successful, you’ll see a message warning you about Nmap’s power and giving the go-ahead to compile. Now build the binaries:
make
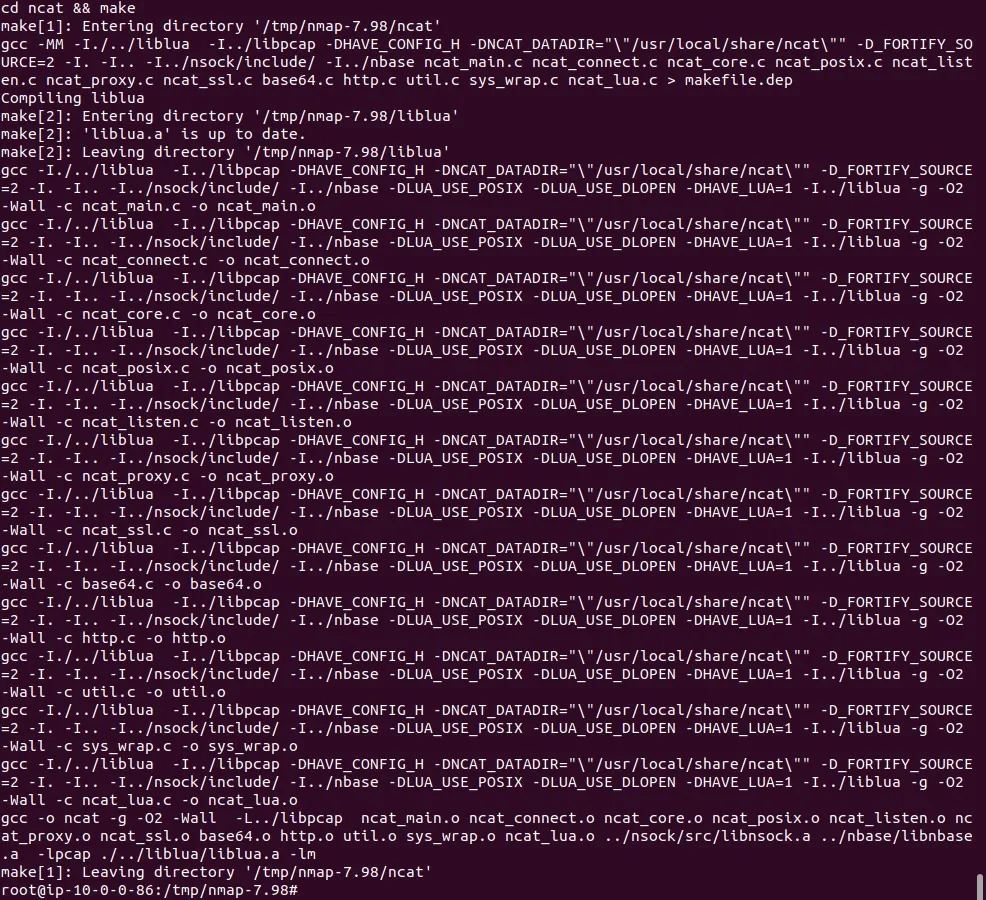
To install system-wide (requires root privileges), run:
sudo make install
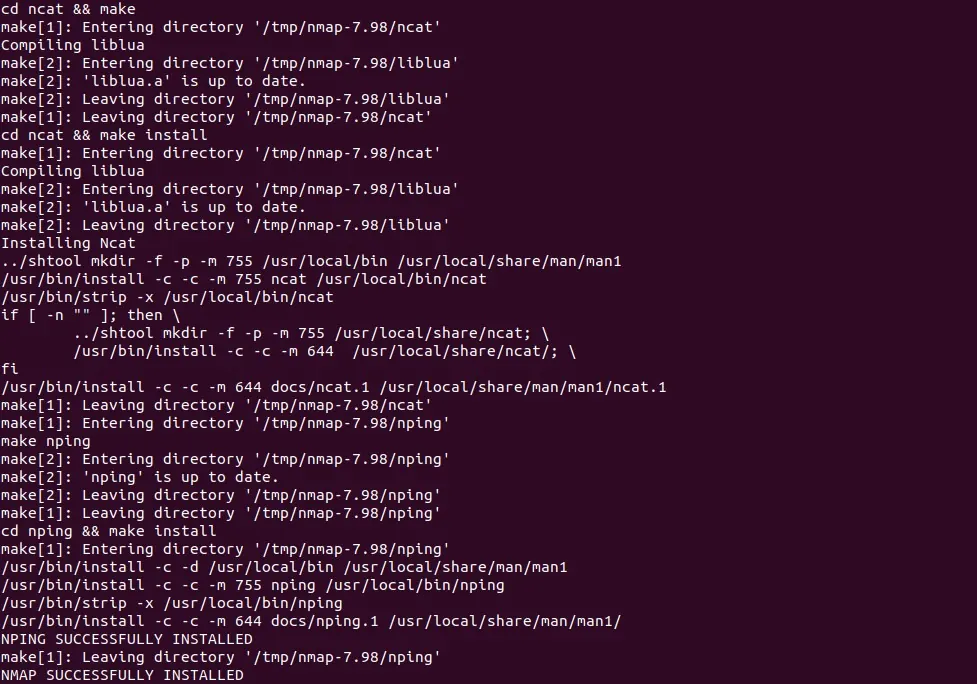
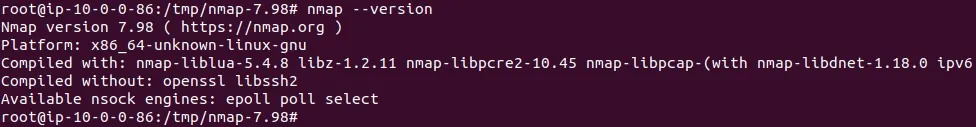
This installs Nmap to /usr/local/bin/nmap by default. You can test it by running:
nmap --version
Nmap Limitations
Nmap has practical limits that affect when and how it should be used. The points below summarize the main risks and shortcomings to keep in mind when planning scans or integrating Nmap into security workflows:
-
- Potential for service disruption: Aggressive or unusual scan techniques can destabilize fragile or legacy devices (for example, industrial controllers or old network gear). Because Nmap actively probes targets, poorly chosen scan types or timings can cause crashes or outages on sensitive systems.
-
- Detection and evasion complexity: Modern IDS/IPS and firewalls are built to spot and block scanning. Although Nmap offers evasion options, getting past advanced defenses reliably takes deep skill and is never certain. Failed evasion attempts commonly result in blocking or alerting security teams.
-
- Legal and ethical constraints: Scanning without clear authorization is unlawful in many places and ethically wrong. Only run Nmap against networks and hosts for which you have explicit permission. Unauthorized scans can cause serious legal, professional, and employment consequences.
-
- Steep learning curve: Basic scans are easy, but mastering Nmap’s many scan modes, timing controls, and the NSE is challenging. Understanding nuanced results and using advanced features safely requires time, study, and hands-on practice.
-
- Incomplete vulnerability analysis: The NSE can find many issues, but Nmap is not a complete vulnerability-management product. It lacks the broad, continuously updated vulnerability databases, risk scoring, and reporting features found in dedicated scanners, so it should be one part of a larger security assessment toolset.
Notable Nmap Alternatives and Competitors
1. Faddom

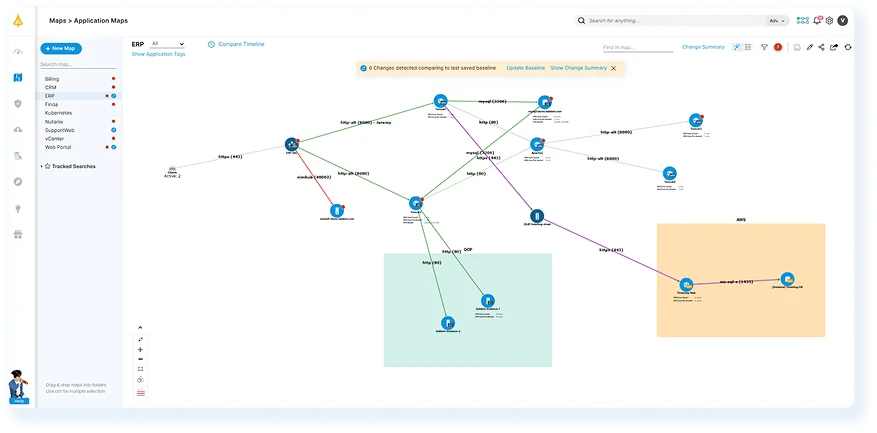
Faddom is an agentless application dependency mapping and network visualization platform that automatically discovers and maps servers, business applications, and traffic flows across hybrid and multicloud environments.
Unlike traditional scanning tools, Faddom delivers continuous, real-time visibility without installing agents, opening ports, or disrupting performance. By providing a complete and always-accurate picture of your infrastructure, Faddom helps IT, Cloud, and Security teams plan changes, strengthen defenses, and maintain control across dynamic environments.
Key features include:
-
- Agentless discovery: Map your entire network safely in under 60 minutes with zero installation or active scans.
-
- Real-time visibility: Always up-to-date maps that reflect every dependency and traffic flow.
-
- Security insights: Detect unauthorized connections, shadow IT, and east-west and north-south traffic for stronger segmentation.
-
- Lighthouse AI: Intelligent anomaly detection that identifies unusual network behavior before it becomes problematic.
-
- Change and migration planning: Understand upstream and downstream impacts before implementing changes.
-
- Data sharing and integrations: Export maps or connect with CMDBs, SIEM, and ITSM tools for consistent documentation.
See Faddom in action, book a demo with our experts!
2. Masscan

Masscan is a port scanner built for breadth rather than deep per-host analysis. It uses asynchronous packet transmission and an independent TCP/IP stack to probe large address ranges at high rates, so it can discover open ports across millions of hosts faster than a traditional scanner.
Key features include:
-
- Internet-scale performance: Can transmit millions of packets per second (configurable via –rate/–max-rate) to scan very large address space quickly.
-
- Asynchronous design: Built on an async transmission model (similar to scanrand/ZMap) to maximize parallelism and speed.
-
- Own TCP/IP stack: Sends raw packets using a separate stack; requires –source-ip or –source-port (or firewall rules) to avoid interference from the host OS.
-
- Nmap-style usage: Command syntax and many options are nmap-compatible, making it familiar to nmap users while remaining focused on wide scans.
-
- No default ports: Users must explicitly specify ports to scan (-p), preventing accidental full-port sweeps.
3. ZMap

ZMap is a high-performance, stateless network scanner built for internet-wide measurement studies. It sends single probe packets (for example, TCP SYNs) across address spaces rather than maintaining per-host state, which lets it sweep the entire public IPv4 space on a single port in minutes on commodity hardware.
Key features include:
-
- Stateless, single-packet design: Sends probes without keeping per-host state to maximize throughput and scale.
-
- Internet-scale speed: Can scan the full public IPv4 space on one port in under 45 minutes on a gigabit desktop; with 10GbE plus netmap or PF_RING, scans complete in under 5 minutes.
-
- Multi-platform: Runs on GNU/Linux, macOS, and BSD.
-
- Probe modules: Fully implemented modules for TCP SYN, ICMP, DNS queries, UPNP, BACNET, and high-volume udp probing.
-
- Pairs with ZGrab 2 for stateful scans: Delegate banner grabbing or full application-layer handshakes to ZGrab 2 when deeper interaction is required.
4. Tenable Nessus

Tenable Nessus® Network Monitor is a passive monitoring solution that analyzes network traffic to deliver continuous visibility into managed and unmanaged assets. Unlike active scanners, it inspects packets non-intrusively, making it safe to use with sensitive systems. It uncovers hidden assets, applications, and trust relationships, to help maintain accurate inventories.
Key features include:
-
- Packet inspection: Continuously analyzes traffic to reveal users, applications, cloud services, trust paths, and vulnerabilities.
-
- Asset discovery: Identifies IT and OT devices, servers, endpoints, databases, hypervisors, web apps, cloud instances, mobile/BYOD devices, and even jailbroken iOS devices.
-
- Continuous visibility: Monitors traffic at packet level for both server- and client-side vulnerabilities; scales to virtual and cloud-heavy environments.
-
- Vulnerability detection: Flags vulnerabilities on new and transient systems, detects compromised applications, and monitors protocol and application behavior.
-
- Suspicious traffic detection: Highlights unencrypted sensitive data, discovers port scans from internal hosts, tracks encrypted and interactive sessions, and maps port usage per system.
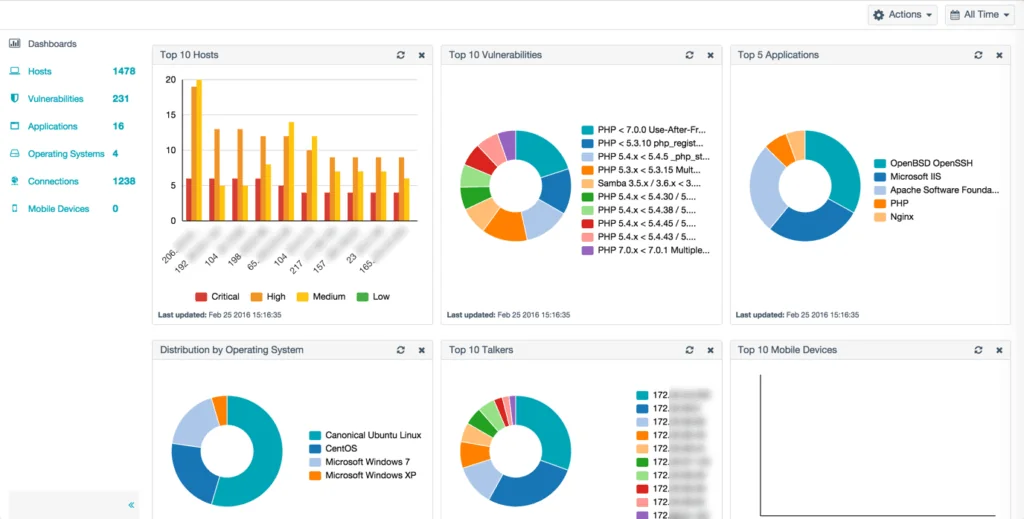
Source: Tenable
5. SolarWinds Network Performance Monitor

SolarWinds Network Performance Monitor (NPM) is a hybrid IT observability solution that provides visibility into network performance across on-premises, multi-vendor, and hybrid environments. By continuously monitoring availability and performance, it helps IT teams detect and resolve issues before they disrupt operations.
Key features include:
-
- Availability monitoring: Continuously tracks network uptime and performance to detect and resolve issues before they affect users or operations.
-
- NetPath™ visualization: Maps and visualizes critical end-to-end network paths to identify bottlenecks and simplify root cause analysis.
-
- Network mapping: Automatically builds and updates topology maps for hybrid and on-premises networks, simplifying management.
-
- PerfStack™ analytics: Correlates and analyzes network performance metrics in real time, enabling deeper troubleshooting and performance optimization.
-
- Advanced alerting: Supports anomaly-based alerts with AIOps and customizable conditions to accelerate response and reduce downtime.
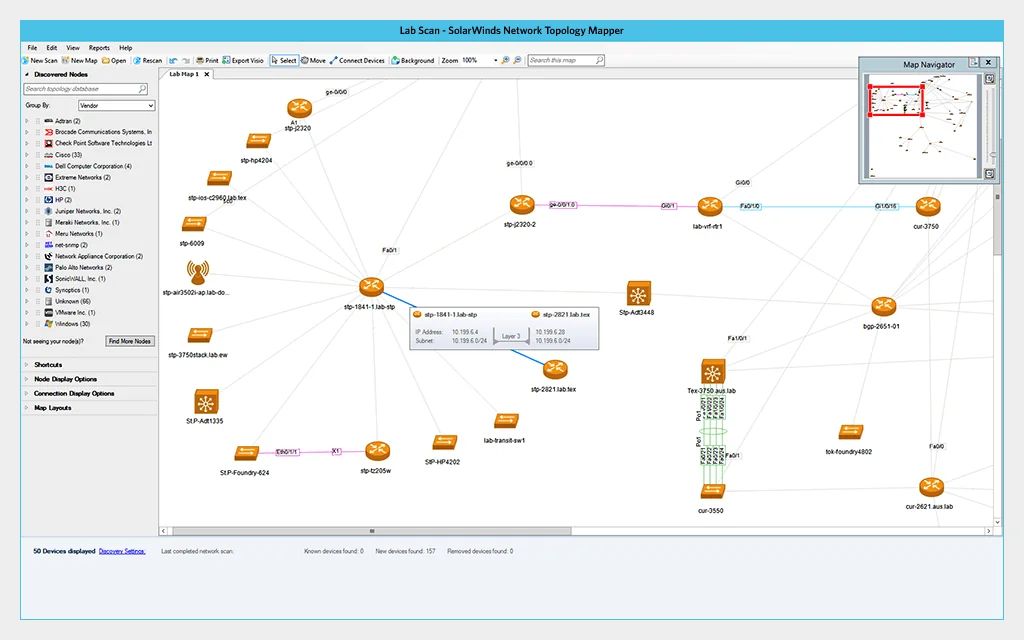
Source: SolarWinds
Related content: Read our guide to Nmap alternatives
Conclusion
Nmap remains a versatile and widely trusted tool for network exploration and security assessments, but it is not the only option available. Depending on factors such as scale, speed requirements, depth of analysis, or integration with broader security workflows, other solutions may be a better fit. The most effective approach is to evaluate what you need, whether that is rapid internet-wide scanning, continuous monitoring, or advanced vulnerability detection, and choose a tool that balances functionality, efficiency, and operational risk for your environment.



