As network environments become more complex and demanding, organizations need effective monitoring methods to simplify IT tasks.
NetFlow and IPFIX are network flow monitoring protocols for the collection of network traffic data. Because they simply watch existing traffic, collecting and analyzing current data to monitor network usage trends, they are considered “passive” network monitoring—as opposed to “active” network monitoring, which introduces its own packets to routinely test the network.
Table of Contents
TogglePassive network monitoring has a number of distinct advantages, making it a long-standing, reliable, and extremely popular method of collecting information about network performance. Firstly, it is non-intrusive; since it adds no additional traffic to the network, it does not impact performance. Also, due to its zero or near-zero performance impact, it is also scalable, allowing it to handle today’s large and complex network environments. Finally, passive monitoring can be very cost-effective because it is simple to set up, learn, and manage and requires no specialized hardware or software.
Compared with protocols like Simple Network Management Protocol (SNMP), which generally track only device information, network flow monitoring additionally provides more data about actual network traffic.
With a relatively low price point and low to no overhead, network monitoring protocols such as NetFlow and IPFIX can give network administrators and security pros a wealth of data to help troubleshoot problems, identify security threats, and plan for capacity.
In this post, we will explore the major differences between NetFlow and IPFIX, the benefits of transitioning from NetFlow to IPFIX, potential speedbumps along the way, and best practices when making the transition.
Head to Head: NetFlow vs. IPFIX
Two of today’s leading network monitoring protocols are NetFlow and IPFIX.
The most important thing to know about network monitoring protocols is that they are distinct from the tools and platforms that organizations use to actually collect network data. Instead, these protocols define standards: methods that network hardware and software can use to collect and transmit traffic flow data.
Because NetFlow and IPFIX are very well-established standards, organizations can choose from a wide range of compatible tools (software collectors), both open-source or vendor-specific, to monitor and analyze the data produced by network devices.
Understanding the advantages of IPFIX in today’s networks requires some familiarity with essential background information about each of these protocols.
NetFlow
NetFlow was originally introduced by Cisco in 1996 as a network protocol for collecting IP traffic information. Having been developed by Cisco, it is a proprietary protocol that collects a range of information: ports, protocols, source and destination IP addresses, bytes transferred, and other IP traffic data.
The NetFlow protocol allows data to be exported to a variety of monitoring and analysis tools.
The diagram above shows the three primary components that make up the basic NetFlow architecture. The flow exporter collects packets and passes them on to the flow collector. The flow collector receives, stores (in a database), and preprocesses flow data. Finally, the analysis application, shown here as a console, performs in-depth analysis on the aggregated flow data—for instance, to detect anomalies such as an intrusion on the network.
IPFIX
The Internet Engineering Task Force (IETF) developed the IP Flow Information Export (IPFIX) protocol as an evolution of NetFlow in the early 2000s. Their goal was to expand the capabilities of NetFlow, offering an approach that would be both more comprehensive and more standardized.
Having been built from NetFlow, IPFIX is naturally similar, but it offers a number of advantages, including:
- Greater flexibility in the types of data it can export
- More powerful customization features
- Improved interoperability with other network monitoring tools
- Better performance and scalability
Like NetFlow, IPFIX collects flow data from network devices and exports it to a collector for analysis. However, IPFIX collects not only the general information collected by NetFlow, but a broader range of data types as well, along with data volume; it can also collect information such as TCP flags, packet timestamps, and other custom fields, including application-layer data, giving it a higher degree of extensibility.
With these extended capabilities, particularly its ability to collect application-layer data, IPFIX is particularly useful for detecting anomalies, identifying traffic patterns, and optimizing network performance. IPFIX can also help security teams analyze network behavior to uncover potential threats.
NetFlow vs. IPFIX: Key Differences
The following table presents the most important differences between NetFlow and IPFIX.
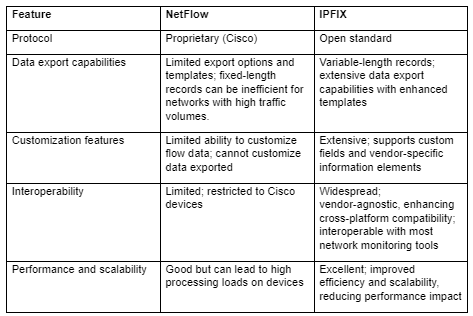
Use Case Scenarios
IT professionals have developed a wide range of use cases for network traffic flow analysis. We briefly cover the most common that function well with either NetFlow or IPFIX.
Troubleshooting
Network monitoring protocols can help track down the root cause of network problems, including slow performance or denial-of-service attacks.
Capacity Planning
Network monitoring protocols assist in forecasting future network traffic needs. Data collected by monitoring tools help organizations plan for increased capacity requirements, thus avoiding network congestion.
Security Analysis
Network monitoring protocols can identify potential security threats, such as unauthorized access to network resources or denial-of-service attacks.
With the advent of IPFIX, many additional use cases have been developed that are better suited to its advanced capabilities.
IPFIX Use Case #1: Traffic Engineering
Traffic engineering refers to optimizing network traffic flow to improve performance and reliability. With its ability to collect detailed information about network traffic, IPFIX can help IT departments identify network bottlenecks and reroute traffic. NetFlow does not collect as much information about network traffic, so it is not as well-suited for traffic engineering applications.
IPFIX Use Case #2: Compliance Reporting
Many organizations today face complex reporting requirements, especially if they’re working in regulated industries. IPFIX can collect more detailed information about network traffic, which may simplify compliance reporting requirements.
IPFIX Use Case #3: Application Performance Monitoring
Application performance monitoring can identify and fix problems such as slow response times, high CPU usage, and memory leaks before they impact users. Being able to collect application-layer information, IPFIX can provide the data necessary to monitor application performance and identify bottlenecks if applications are not performing as expected.
Further Use Cases for IPFIX
IPFIX also outshines NetFlow when it comes to security because it can be configured to collect additional information, providing more insights for security purposes. Use cases here include tracking traffic of unauthorized users who may be trying to access sensitive data, identifying the source of distributed denial-of-service (DDoS) attacks that may be flooding the network, and identifying malware traffic such as intruders attempting to exfiltrate data.
As it is compatible with a greater range of devices on the network, IPFIX also offers more diverse and comprehensive insights into the organization’s entire security posture. And with more data sources such as TCP flags, packet timestamps, and user-defined fields, IPFIX provides richer context for threat detection and investigation.
Transition from NetFlow to IPFIX
It’s clear that IPFIX offers a more flexible, powerful, and interoperable protocol. Due to its greater degree of compatibility with a wider range of modern devices, IPFIX is probably a better bet for future-proofing any organization’s IT department, with all the scalability and other advantages of a passive network monitoring protocol.
IPFIX also has a template-based structure for exporting flow data, which enables greater flexibility in defining what data fields are included in flow records, including standard fields and vendor-specific extensions; this allows organizations to tailor exported data to their specific monitoring needs.
An additional reason that many organizations are transitioning to IPFIX is that its specifications are well-documented and stable, helping companies confidently build long-term IT plans. Interoperability is another advantage. In today’s complex, multi-vendor network environments, the flexibility of IPFIX means organizations can choose from a wide range of network devices and monitoring tools, avoiding single-vendor lock-in.
IPFX’s standardized template structure also makes data compression and export more efficient, enabling better scalability and reducing the impact on network devices when exporting flow data. This is especially important in large and complex network environments.
However, while IPFIX may be a winner in terms of its benefits to an organization, as with any large-scale IT changes, there may be challenges along the way.
Challenges in Transition
One of the main challenges that organizations encounter when transitioning from NetFlow to IPFIX is the need to upgrade network devices to support IPFIX.
Data Upgrades and Data Reformatting
The greater complexity of IPFIX demands more processing power and other capabilities on network devices. In addition, any device upgrade could lead to disruptions including planned outages, traffic disturbances, and the risk of upgrade errors impacting the network.
Organizations will also need to migrate older NetFlow data to the updated IPFIX format since IPFIX collectors can’t read the older format. Data will need to be exported, converted, and re-imported—a time-consuming process, especially for large datasets. During any migration project, there is the chance of data loss as well, underscoring the need for careful planning and thorough testing.
Training and Planning
Often overlooked in the transition is the need for training and knowledge transfer. Teams must be capable of ensuring a smooth transition; they must be trained to handle the correct setup and maintenance of IPFIX, along with any new tools and platforms being implemented.
Finally, many organizations begin complex transition projects without a clear picture of their entire network configuration and dependencies. This gives the transition project a greater risk of failure—and of impacting operations, including downtime.
Best practices for transition
Here are a few tips from experienced IT professionals to help ensure that the transition from NetFlow to IPFIX proceeds as smoothly and efficiently as possible.
Assess
Before even planning the transition, conduct a thorough assessment of the existing NetFlow deployment. This will include full network mapping using a fast, agentless network application dependency mapping tool. Mapping assists in proper planning and will head off any unforeseen consequences of the transition.
Plan
Based on the insights gained through network mapping, develop a migration plan to address decisions such as where heightened visibility is required and which types of information should be collected. Organizations also need to be aware of technical details such as which types of traffic should be monitored (ingress, egress, or both) and which packet headers will provide the most valuable data for analysis.
Planning for the transition will additionally involve determining which third-party tools or platforms will be used to monitor and analyze the data collected. Several good options are available, including open-source and commercial options at a variety of price points.
Implement
A gradual, phased transition will create the least possible disruptions. With the comprehensive network picture received during the assessment stage, organizations will have a better understanding of which areas of the network need to be transitioned first, or together.
Ensure that IT staff is trained and up to speed so they can oversee the rollout and ongoing maintenance of IPFIX. This will include empowering teams to not only monitor the system regularly to ensure it is delivering meaningful data and results, but to also adjust it as needed for ongoing optimization.
Meet Faddom
Today’s IT professionals are handling a variety of challenges and more complex, dynamic networks than ever before, with a massive variety of applications, servers, cloud services, databases, middleware, and endpoints. The need for network flow monitoring has never been greater, and it’s easy to see why older monitoring protocols like NetFlow might not be up to the task.
This is also true of older application dependency solutions. Today’s networks are too complex to keep track of manually. And with the elasticity of cloud, assets and networks can change from one day to the next, or even one minute to the next.
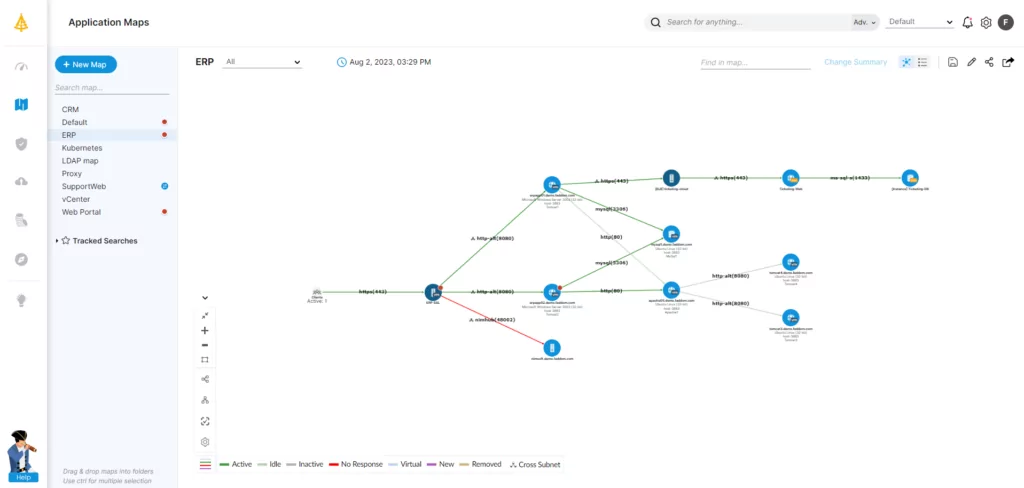
Getting the big picture of a network environment through IT system mapping is the best way to understand clearly and simply what’s happening across the entire network before embarking on any change, major or minor.
Today’s simplest, most affordable way to achieve that big-picture view, before a transition to IPFIX or any other IT change project, is with Faddom. Faddom maps servers, applications, and dependencies across your entire environment, including cloud and on-premises, regardless of vendor.
Faddom requires no special training; it’s easy to use and works quickly, delivering results in under an hour. And since it doesn’t require agent installation, credential storage, or firewall changes, Faddom is highly secure.
Faddom helps you achieve the smoothest transition from NetFlow to IPFIX, helping your business prepare today for the future of IT. To start a free trial and see how simple it can be to get the data you need, just fill out the form on this page.









