Legacy applications are outdated, inefficient, and a potential source of risk, such as from old security vulnerabilities that can no longer be patched. Many organizations are thus choosing migration rather than continuing to make do, moving legacy applications to a new platform or environment.
However, some organizations decide that migrating legacy applications is too difficult a task despite the benefits it can offer, including improved performance, security, and scalability. One way to simplify the migration process is to choose a strategy best suited to the needs and priorities of an organization’s application and overall business.
Table of Contents
ToggleTo help organizations choose the most effective migration strategy, this post will discuss the process of legacy application migration in detail, including the pros and cons of the available strategies, along with tips for success in any legacy application migration project.
What Is Legacy Application Migration and Why Migrate?
Legacy applications refer to programs that no longer meet the needs of a business or are simply outdated. Migration is the process of moving these legacy applications to a new platform or environment. Several options exist for this transition, as will be explored below.
Legacy application migration can be complicated, but with the challenges come several benefits.
Lower Costs
Legacy applications can be costly to maintain and support; migration makes them easier for today’s teams to use, upgrade, and configure.
Improved Compatibility
Legacy applications may not be compatible with newer technologies and operating systems; migration ensures that apps can integrate and interoperate with a variety of leading and industry-specific business applications.
Better Performance
Legacy applications may not be able to meet the performance and scalability demands of modern businesses; migration can build in resilience and elasticity to rapidly grow and scale back based on demand.
Enhanced Security
Legacy applications may be vulnerable to security threats; migration integrates today’s security best practices, ensuring a safer, more robust application.
The Process of Migrating Legacy Applications
As with any type of major IT transition, a well-planned process can ensure that problems are identified ahead of time, with the goal of eliminating surprises and providing the greatest chance for success. There are five main steps in any migration process, explained below.
Assessment
A legacy application migration always starts with determining the application’s current state. This includes identifying its dependencies, performance bottlenecks, and security vulnerabilities.
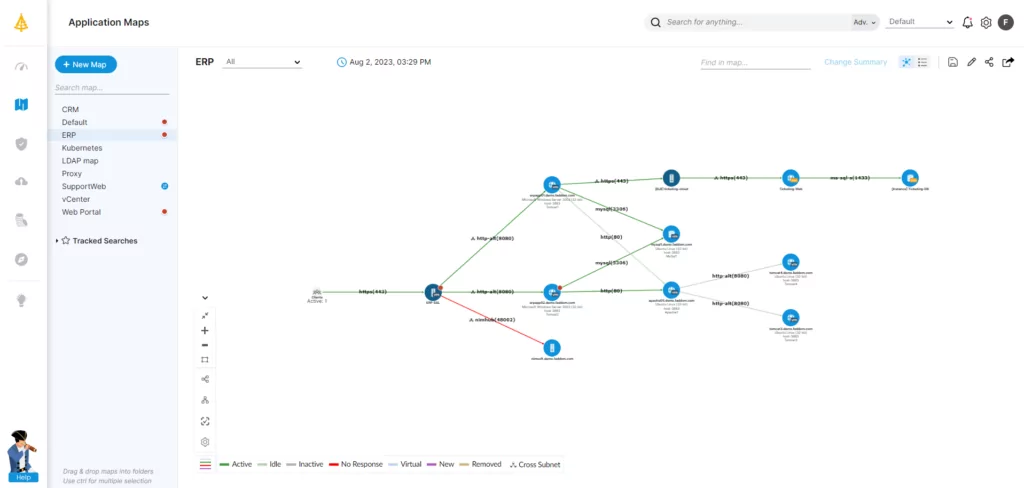
Application discovery mapping (ADM) tools can be used at this stage to identify relationships between the legacy application and other systems; this helps to inform the assessment process and determine requirements for the migrated application.
Development or Modification
In this step, the application is either developed or modified for the new platform or environment. The following section explores the types of development or modification that are available. Options include refactoring the code, rewriting the application from scratch, or using a cloud-based migration platform. Each of these strategies involves a different degree of effort and will therefore carry a different price point.
Testing
Before deployment, the application should be thoroughly tested in its new environment to ensure that features and functionality all work as expected. Testing also guarantees the application’s performance and security under live conditions.
Deployment
At this point, the new or modified application is deployed to production. This may also involve migrating the application’s data (e.g., any databases used) to the new environment, as well as updating any configuration settings.
Monitoring
Finally, administrators should continue monitoring application performance and security closely to ensure that the migration was successful and that the application is operating properly.
An ADM tool is once again helpful at this stage, letting organizations pinpoint problems with the migrated app, such as broken dependencies and bottlenecks; it can also report on the overall performance and health of the environment.
Types of Legacy Application Migration Strategies
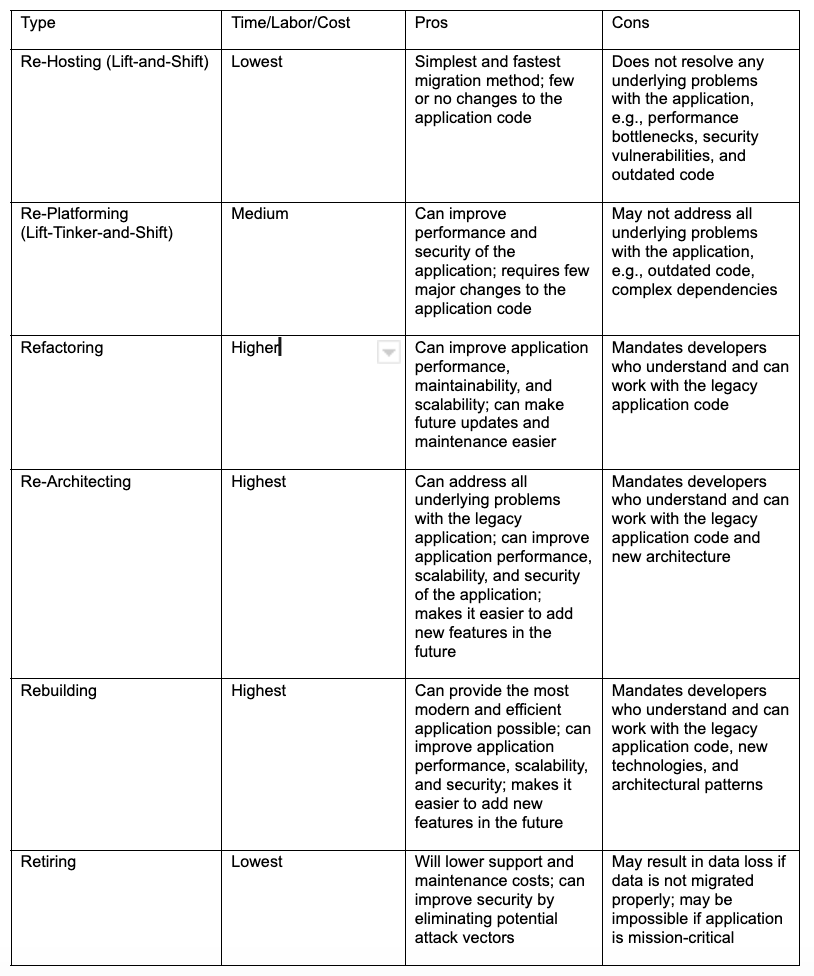
There is no one-size-fits-all solution when it comes to choosing a strategy to deal with an outdated legacy application. However, the most common application migration strategies are outlined in the table below:
Refactoring, Re-Architecting, and Rebuilding: How They Differ
Three of these strategies in particular—refactoring, re-architecting, and rebuilding—have such similar names that they are often confused. However, there are a few key concepts that differentiate them:
- Refactoring:
- Goal: Making the code better without changing what the application does
- Different from re-architecting because it does not change the functionality of the application
- Different from rebuilding because it does not involve rewriting code from scratch
- Re-architecting:
- Goal: Making the design better to boost the application’s overall quality
- Different from refactoring because it makes major changes to the design of the application
- Different from rebuilding because it does not involve rewriting code from scratch
- Rebuilding:
- Goal: Making a new application using the latest and greatest technologies
- Different from refactoring because it involves rewriting code from scratch
- Different from re-architecting because it is not limited to making changes to the application’s design
Use Cases
The following use cases help clarify each strategy. Note: Any of the strategies could in fact be used for each situation.
Re-Hosting (Lift-and-Shift)
This method could work well for migrating a legacy application to the cloud to reduce operational costs and improve scalability.
Re-Platforming (Lift-Tinker-and-Shift)
Re-platforming might give the best results when the goal is to improve security and compliance through more sophisticated built-in security features and configuration options.
Refactoring
This can be the best option for a legacy application written in Java, which is difficult to maintain, update, and scale. Developers change the code to improve its structure, readability, and maintainability while also removing unused and duplicate code. The refactored application is easier to maintain, update, and scale, and may also perform better.
Re-Architecting
This is a good strategy for organizations looking to redesign a legacy application to take advantage of modern microservices and containerized architectures, which provide improved scalability, reliability, and agility.
Rebuilding
Rebuilding is appropriate when a company is willing to invest a lot of time and money to recreate a legacy application from scratch. Using modern technologies to rebuild the app will improve performance and scalability, as well as provide for future expansion. If major changes are required to the app, then rebuilding is ideal.
Retiring
An organization could consider retirement for a legacy customer order application that is difficult to maintain and update; has failed to scale as the company has grown; or does not support new features, and its interface can’t be updated. A company may also decide to retire an application and implement order functionality through customizations of its cloud-based CRM.
Best Practices for Legacy Application Migration
Regardless of which strategy an organization ultimately selects, the following best practices will help ensure the migration process goes as smoothly as possible:
Involve Stakeholders Early
Ensure that everyone is on the same page and that the migration plan considers all stakeholders’ needs.
Create a Detailed Migration Plan
Determine the timeline, budget, and risk assessment at the start of the migration journey. An application dependency mapping tool can help organizations create the simplest migration plan by:
- Identifying which legacy applications are critical to business operations
- Identifying legacy applications that are bottlenecks or security risks
- Helping plan and execute legacy application modernization safely and efficiently
Establish a Rollback Plan
If the migration does not go as planned, a rollback plan will outline steps to restore the legacy application to its previous functional state.
Implement Version Control
Establish strong, consistent version control for legacy application code and data; this allows teams to track changes and roll back to a previous version if necessary.
Document Everything
Document all aspects of the legacy application migration process, including assessment, development or modification, testing, deployment, and monitoring phases.
Conduct a Post-Migration Review
It is important to conduct a post-migration review to identify any areas for improvement; this should include the use of ADM to track efficiency and effectiveness post-migration.
The Role of ADM in Legacy Application Migration
As seen above, ADM should be a built-in component of every legacy application migration project. Organizations can use it before, during, and after a migration to gain comprehensive insights into an application’s performance and security, keeping the migration on track and ensuring minimal disruption to the business.
Here are some of the most popular uses of ADM as part of legacy application migration.
Before Migration
ADM will assess the current state of a legacy application. This will include its dependencies, performance bottlenecks, and security vulnerabilities to help determine an optimal migration strategy and develop a detailed migration plan.
It can also identify components of a legacy application that need to be modified or rewritten to help formulate a more efficient and effective migration plan.
During Migration
Organizations should implement ADM to understand which components have already been migrated; which are still in process; and any errors, problems, or bottlenecks occurring during the migration process.
After Migration
ADM enables the monitoring of migrated apps to identify any problems with the migration and ensure that they are running as expected. This will include both performance monitoring, e.g., response times, throughput, and resource utilization, as well as security monitoring, e.g., keeping a lookout for suspicious activity and potential vulnerabilities.
Get Ahead of the Curve with Faddom
Legacy application migration is a must for any business that wants to stay ahead of the curve—not only as a way of ensuring tighter security, but also because it helps achieve an app that looks, feels, and performs the way today’s users expect. Given the many other benefits of modernization, most organizations recognize it as the best path forward.
Each legacy application migration strategy has advantages and disadvantages. However, regardless of the strategy chosen, following the tips outlined in this post will increase the chances of a successful legacy application migration. That includes making application dependency mapping (ADM) a key component of the process.
An ADM tool such as Faddom will identify potential problems early on to ensure the smoothest possible journey before, during, and after migration. Faddom helps organizations get started with ADM easily—in under one hour. Just fill out the form on this page to get started for free!









