What Is Lateral Movement?
Lateral movement in cybersecurity refers to the techniques used by attackers to move through a network after gaining initial access, aiming to access high-value targets like sensitive data or critical systems. It’s a crucial phase in many cyberattacks, allowing attackers to expand their reach and impact.
Key aspects of lateral movement include:
- Post-compromise navigation: Lateral movement is not the initial point of entry into a network. It’s the subsequent actions attackers take to move from the compromised system to other parts of the network.
- Objective: The goal is to discover and access valuable assets, such as sensitive databases, domain controllers, or other critical infrastructure.
- Methods: Attackers employ various techniques, including exploiting vulnerabilities, using stolen credentials, and leveraging legitimate tools for malicious purposes.
How lateral movement works:
Table of Contents
Toggle- Initial access: The attack starts with an initial compromise, like a phishing attack, malware infection, or exploiting a vulnerability.
- Internal reconnaissance: Attackers explore the compromised system and network to identify potential targets and gather information about the network’s structure, resources, and security posture.
- Credential theft/reuse: Attackers often steal credentials (usernames and passwords) to gain access to other systems and resources.
- Privilege escalation: Attackers may try to elevate their privileges to gain more control and access within the network.
- System compromise: Using the acquired credentials and vulnerabilities, attackers move to other systems, expanding their control and access.
- Targeting high-value assets: The ultimate goal is to reach critical systems or data, such as databases, servers, or domain controllers, which hold valuable information or control the network.
This is part of a series of articles about Network Security-FM
The Danger of Lateral Movement Attacks
Lateral movement is particularly dangerous because it exploits the limitations of traditional security approaches. Many security teams still focus heavily on preventing intrusions at the perimeter, but once an attacker gets inside, internal traffic, often referred to as east-west traffic, is much harder to monitor. This internal visibility gap allows threat actors to move undetected between systems for extended periods.
Most organizations rely on outdated tools such as legacy firewalls and basic allowlisting, which are not designed to detect or stop lateral movement. As a result, attackers can explore the network, escalate privileges, and access sensitive systems without triggering alerts. Detecting lateral movement requires monitoring traffic between internal applications and systems, a task that is technically complex and often overlooked.
Modern cybersecurity strategy must assume that breaches will happen and focus on identifying threats quickly. The ability to detect unusual lateral movement early is critical to reducing the scope and damage of an attack. Without visibility into east-west activity, organizations risk discovering the breach only after attackers have exfiltrated data or caused significant disruption.
How Lateral Movement Works: The Stages of Attack
Although lateral movement has many methods and tools that attackers use (discussed later), the stages of a lateral movement attack are far more standardized. Cybersecurity experts and organizations have identified three stages of lateral attacks:
1. Initial Access
Infection begins when an attacker successfully gains a foothold in the target environment. This often happens through social engineering attacks such as phishing, where users are tricked into opening malicious attachments or clicking on links that download malware. Other common methods include exploiting known vulnerabilities in web applications or using stolen credentials obtained from previous breaches.
Once inside, attackers typically deploy malware or use living-off-the-land techniques, leveraging built-in tools like PowerShell or WMI to avoid detection. Establishing persistence is critical at this stage, allowing attackers to maintain access even if the initial infection vector is closed. They may install backdoors, create new user accounts, or schedule tasks to ensure they can return later.
2. Internal Reconnaissance
Reconnaissance is the phase where attackers gather detailed knowledge of the internal network. They enumerate hosts, services, open ports, and trust relationships to understand the layout and identify the most valuable targets. The objective is to find domain controllers, file shares, backup servers, or applications storing sensitive data.
Tools used in this phase include netstat, ipconfig, nslookup, nbtstat, and more advanced frameworks like BloodHound for mapping Active Directory environments. Attackers aim to blend in with normal network traffic, often conducting low-noise scans or using built-in administrative tools to avoid triggering alerts.
Information from reconnaissance is used to plan the lateral movement path, choosing the easiest and least detectable routes between systems.
Once attackers gain network entry, they begin exploring and mapping the network, users, and devices. This information enables malicious actors to determine possible access permissions, along with policies like standardized file naming and access protocols.
3. Credential Theft/Reuse
Credential theft is a critical stage that enables deeper and more flexible lateral movement. Attackers target credentials stored in memory, on disk, or transmitted over the network. They use tools like Mimikatz to extract password hashes, plaintext passwords, or Kerberos tickets from systems they control.
They may also perform pass-the-hash or pass-the-ticket attacks to authenticate across systems without needing plaintext passwords. Attackers prioritize accounts with administrative privileges or broad access across the network.
In some cases, attackers exploit weak password policies, re-used passwords, or service accounts with excessive privileges. Successfully stolen credentials allow attackers to impersonate users, bypass security controls, and access new systems without relying on malware, making their actions harder to detect.
4. Privilege Escalation
Privilege escalation occurs when attackers elevate their permissions from a standard user account to administrative or system-level access. This is often achieved by exploiting software vulnerabilities, misconfigurations, or weak service account permissions. Common techniques include kernel exploits, bypassing user account control (UAC), and abusing scheduled tasks or services running with higher privileges.
Once higher-level privileges are obtained, attackers gain the ability to disable defenses, access sensitive data, and move laterally without restriction. Privilege escalation is often repeated throughout the attack as adversaries compromise additional systems and accounts, ensuring they always maintain a high level of access.
5. System Compromise
After securing initial access, attackers move to compromise additional systems or elevate their privileges. This stage may involve exploiting local vulnerabilities on the infected system or misconfigurations in user permissions, service accounts, or operating system settings.
Attackers look for opportunities to escalate from a regular user account to one with administrative privileges. Techniques include DLL injection, token manipulation, or exploiting services running with higher privileges. During this stage, attackers may also disable security software, clear logs, or modify configurations to evade detection and maintain control over compromised systems.
Compromise is often iterative: attackers may repeat this phase multiple times, each time moving closer to high-value systems or data.
6. Targeting High-Value Assets
After escalating privileges, attackers shift their focus to the most valuable systems and data within the environment. This typically includes domain controllers, financial systems, intellectual property repositories, or critical infrastructure servers. Gaining access to these assets allows attackers to take control of the network or exfiltrate sensitive data with significant business impact.
At this stage, attackers often establish persistence on high-value systems to ensure long-term access. They may deploy backdoors, create hidden accounts, or modify authentication mechanisms to maintain control even if part of the attack is discovered. Data exfiltration or preparation for ransomware deployment usually occurs here, marking the final and most damaging phase of lateral movement.
Common Lateral Movement Techniques
Attackers use a range of techniques to move laterally across a network after initial compromise. These methods often rely on legitimate administrative tools and protocols, making them difficult to detect. Common techniques include:
1. Pass-the-Hash and Pass-the-Ticket: Instead of cracking passwords, attackers reuse stolen hashes or Kerberos tickets to authenticate on other systems. These methods allow lateral movement without needing plaintext credentials.
2. Remote Execution and Service Exploitation: Attackers target services like SMB, RDP, and WinRM to execute commands or transfer payloads to remote systems. They may use legitimate tools such as PsExec or abuse WMI to run code remotely.
3. Man-in-the-Middle (MitM) Attacks: Attackers intercept traffic between systems to capture credentials, session tokens, or sensitive data. They may alter communications or inject malicious payloads while remaining undetected by legitimate users.
4. Lateral Phishing: Compromised accounts are used to send phishing emails internally, increasing the chance of success since messages appear to come from trusted colleagues. This allows attackers to expand access across the network with minimal suspicion.
5. Living off the Land (LotL): To stay undetected, attackers rely on tools already present in the environment (like PowerShell, WMI, or Scheduled Tasks) to execute commands and scripts across systems.
6. Credential Dumping: Tools like Mimikatz extract stored credentials from memory, registry, or files. Attackers use these credentials to log in to other systems with the same or higher privileges.
7. Exploiting Trust Relationships: Attackers take advantage of implicit or poorly secured trust relationships between systems, such as shared administrative accounts or open access to file shares and management interfaces
8. SSH Hijacking and Key Abuse: In Unix-based environments, attackers may steal SSH keys to access other servers. Weak permissions or key reuse makes it easier to move between systems unnoticed.
9.Lateral Tool Transfer: To avoid detection, attackers may transfer custom tools or malware using non-standard ports or covert channels. They might also hide payloads in documents or use built-in compression and encoding.
How to Detect Lateral Movement
Monitor Authentication Patterns
Authentication logs are one of the most valuable sources for spotting lateral movement, since attackers often rely on stolen credentials to expand access. Security teams should closely monitor for logins from unexpected geographic locations, systems, or time zones.
A common red flag is when the same user account logs in from two distant locations within minutes, something a legitimate user could not physically do. Another indicator is repeated failed login attempts followed by a successful one, which suggests brute force or credential stuffing.
Privileged accounts that suddenly access systems they have never touched before should be flagged, as this often means an attacker is testing stolen credentials to see how far they reach. Service accounts, which are typically limited to specific functions, should be monitored especially closely: if a service account is suddenly logging into administrative consoles or sensitive systems, it is a strong signal of compromise.
Baseline Normal Behavior
To detect anomalies effectively, organizations must first define what “normal” looks like in their environment. This includes tracking typical login times, frequency of access, common destinations, and regular communication patterns between systems.
For example, a user in the finance department may normally access accounting software during business hours from the office, but if the same user suddenly connects to engineering servers at night, it deviates from the baseline.
Baselines should be established not only at the individual user level but also at the system and application level. Over time, deviations from these baselines can be automatically flagged for investigation. Advanced detection platforms often use statistical models and machine learning to adapt baselines dynamically, accounting for normal variations such as seasonal changes or business cycles.
Analyze Network Traffic
Attackers moving laterally must communicate across systems, making internal network traffic a rich data source for detection. East-west traffic (system-to-system communication within the network) is harder to monitor than north-south traffic (traffic entering or leaving the network), but it often holds the strongest signals of compromise. Indicators include systems suddenly initiating connections to machines they don’t normally interact with, abnormal data transfer sizes, or unusual use of protocols such as SMB, RDP, or WinRM.
Attackers may also tunnel traffic through encrypted channels to evade inspection. Network flow data (NetFlow, sFlow) can help identify patterns like beaconing, where a compromised host regularly contacts a command-and-control server. Deep packet inspection and intrusion detection systems can add further visibility, though they must be carefully tuned to reduce false positives.
Correlate Endpoint Activity
Endpoints often show the earliest technical signs of lateral movement. Attackers frequently use legitimate tools such as PowerShell, WMI, or PsExec to execute commands remotely, so monitoring command-line activity is essential. EDR solutions provide this level of visibility by recording process creation, registry changes, file modifications, and memory injections.
For example, PowerShell execution on one workstation may be normal, but if dozens of systems execute similar commands within a short timeframe, it indicates coordinated lateral movement. Malware deployment, privilege escalation attempts, or mass creation of scheduled tasks are also common patterns that EDR tools can detect when aggregated.
Track Credential Use
Since stolen credentials are the main enabler of lateral movement, unusual authentication activity should always be scrutinized. Accounts that log in from multiple systems simultaneously, perform interactive logins on servers where they normally don’t, or suddenly access highly sensitive data stores all suggest misuse. Attackers also tend to overuse high-privilege accounts, such as domain admins, because they allow maximum reach.
Privileged account management (PAM) solutions can help by enforcing just-in-time access, rotating credentials frequently, and alerting when admin accounts are used outside of expected workflows. Kerberos authentication events are another key area to watch: anomalies like ticket-granting ticket (TGT) requests from unusual hosts or ticket reuse can indicate pass-the-ticket attacks.
Audit Changes to System Configurations
Attackers often change system configurations to maintain persistence and prepare for further lateral movement. These changes can include creating new user accounts, modifying group memberships, disabling security tools such as antivirus or endpoint protection, or altering firewall and group policy settings.
Scheduled task creation and startup script modification are also common persistence methods. Security teams should collect and centralize system logs to detect these changes quickly. File integrity monitoring (FIM) tools can provide additional visibility by alerting on unauthorized modifications to critical system files or configuration settings.
Auditing Active Directory changes is particularly important, since attackers often manipulate domain controllers, trust relationships, and policies to expand access across the enterprise. Continuous auditing ensures that unauthorized changes are caught before they can be leveraged for further compromise.
Lateral Movement Mitigation and Prevention Strategies
Here are some of the ways that organizations can protect themselves against lateral movement.
1. Enforce Network Segmentation
Network segmentation reduces the blast radius of an intrusion by limiting how far an attacker can move once they compromise a system. Flat networks allow unrestricted east-west traffic, making it trivial for attackers to pivot between hosts. Instead, organizations should implement tiered segmentation that separates workstations, application servers, databases, and domain controllers into distinct security zones.
Access between zones should only be permitted where there is a documented business requirement, and traffic should be tightly controlled with firewalls, ACLs, or software-defined networking policies. Microsegmentation goes further by enforcing controls at the workload level, restricting communication paths between specific applications or even processes. For example, a payroll application may only be allowed to query a database server over a defined port, blocking all other traffic.
This makes lateral movement far more difficult, since attackers must bypass multiple barriers rather than moving freely within a single segment. Regular testing of segmentation controls is also necessary to ensure that firewall rules, VLAN boundaries, and SDN policies remain correctly enforced.
2. Apply the Principle of Least Privilege
Excessive user and service privileges are one of the main enablers of lateral movement. To minimize risk, access rights should always follow the principle of least privilege, meaning users and processes only receive the minimum level of access required for their role.
Implement role-based access control (RBAC) to align privileges with job functions, and conduct periodic entitlement reviews to remove unnecessary rights. Dormant or orphaned accounts should be deactivated quickly, as they often become low-hanging fruit for attackers.
For administrators, just-in-time (JIT) access is highly effective. Instead of maintaining standing privileges, admin rights are granted only for the duration of a task and revoked automatically when no longer needed. This reduces the chance that stolen credentials can be reused.
Service accounts should also be tightly scoped, with limited permissions, strong password rotation, and ideally replaced by managed identities where possible. Network-level controls should restrict the use of powerful tools like RDP, PowerShell Remoting, and SSH to trusted management networks, preventing attackers from abusing them on user segments.
3. Ensure Strong Authentication
Organizations should enforce multi-factor authentication (MFA) on all sensitive accounts and systems, especially administrative accounts, VPNs, and remote access gateways. MFA ensures that even if attackers steal or guess a password, they cannot log in without the additional factor.
Where possible, passwordless authentication methods such as hardware tokens, smart cards, or FIDO2 keys provide stronger protection against credential theft. Password policies must also be hardened. This includes enforcing unique, complex passwords, preventing reuse across accounts, and requiring periodic rotation for high-privilege credentials.
Credential vaulting solutions and privileged account management (PAM) systems can further reduce risk by automatically managing and rotating credentials, ensuring they are never exposed in plaintext or reused across multiple systems.
4. Implement Monitoring and Logging
Comprehensive monitoring and centralized logging are critical for detecting lateral movement before it escalates. Security Information and Event Management (SIEM) platforms should aggregate logs from endpoints, servers, firewalls, authentication systems, and Active Directory, allowing analysts to correlate events across the environment.
Suspicious activity such as repeated failed logins, new administrative account creation, or unusual access patterns can then be flagged for investigation. To improve detection speed, organizations should implement real-time alerting with well-tuned rules that reduce noise while focusing on high-value indicators.
Endpoint detection and response (EDR) solutions provide additional visibility into command execution, process creation, and registry changes, which are common signs of lateral activity. Regular log reviews and automated threat-hunting queries help ensure that anomalies are caught before attackers can reach high-value assets.
5. Use Intrusion Detection and Prevention Systems (IDS/IPS)
IDS and IPS technologies provide another layer of defense by analyzing network traffic for signatures or behaviors that indicate lateral movement. An IDS passively monitors traffic and generates alerts on suspicious activity, while an IPS can actively block malicious traffic in real time.
These systems can detect attempts to exploit vulnerabilities, unauthorized remote execution, or brute force authentication attempts. To maximize effectiveness, IDS/IPS solutions should be deployed not just at the perimeter but also inside the network, monitoring east-west traffic where lateral movement occurs.
Regular signature updates and tuning are required to balance detection coverage with false positive reduction. Advanced IPS systems with behavior-based detection can identify novel attack patterns, providing protection against previously unseen lateral movement techniques.
6. Use Deception Technology and Honeypots
Deception technologies provide defenders with early warning signals by luring attackers into interacting with decoys that mimic legitimate assets. Honeypots can be designed to resemble real servers, workstations, or network services, while honeytokens act as fake credentials, files, or database entries. Because legitimate users never access these resources, any interaction with them is a high-confidence indicator of malicious activity.
Modern deception platforms go beyond simple honeypots by deploying distributed, lightweight decoys across the enterprise environment. These can imitate production assets such as Active Directory domain controllers, database servers, or cloud services, tricking attackers into revealing their presence during reconnaissance or lateral movement attempts.
Alerts from these systems provide defenders with detailed insight into attacker tactics, techniques, and procedures (TTPs), enabling faster incident response. Importantly, because decoys don’t host real business data, they carry minimal risk if compromised.
Gain Visibility into Your Network with Faddom
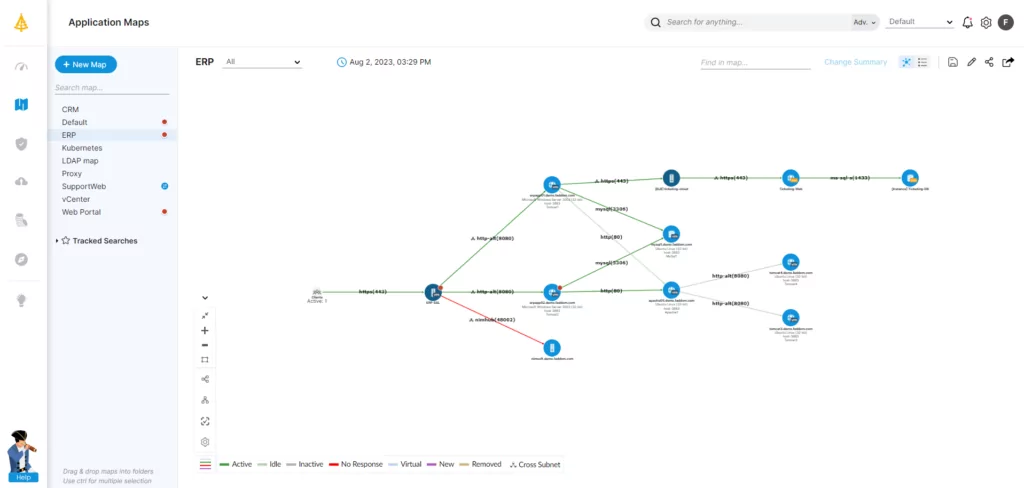
Lateral movement cybersecurity is constantly changing to meet the growing threat vectors in today’s digital ITC device world. Every organization, from SMBs to enterprises, must constantly evaluate their security strategy to include preventative, detection, and response solutions for automatic identification of threats. The more visibility organizations have into their networks with application dependency mapping, the more effective their defense will be against lateral movement.
Protect your organization from lateral movement and other pervasive security threats. Faddom supports a holistic security approach through segmentation and network visibility. Start a free trial today!








