In today’s digital age, it’s no secret that technology plays a pivotal role in business operations. However, the intricate web of devices, software, and networks that enable these operations is often overlooked. That’s where IT topology comes in. It creates the blueprint that defines how these components fit together in an organization’s infrastructure.
Understanding IT topology is a critical factor in optimizing operations and improving efficiency. By identifying potential areas for improvement, organizations can make the most of cloud technology and virtualization, ultimately reducing the risk of cyber threats.
Table of Contents
ToggleThis article explores how a clear understanding of an organization’s IT topology can revolutionize its business operations.
What is an IT Topology?
IT topology refers to the overall arrangement or organization of the different components of an information technology infrastructure, encompassing both physical and logical aspects. This covers the hardware, software, and network components, how they are interconnected, and their relationships and dependencies on one another. IT topology covers a range of assets, including on-premises, cloud, and virtual resources.
Understanding an organization’s IT topology is essential to identifying potential vulnerabilities and assessing the overall attack surface. According to a 2021 survey cited by IBM, over the previous year, 69% of organizations were “compromised via unknown, unmanaged, or poorly managed” assets that could be accessed via the internet.
Increasing visibility and ensuring it remains current is necessary for companies to take proactive steps toward enhancing their security posture. By clearly understanding IT topology, businesses can optimize their IT infrastructure, improve system reliability, and ensure better security. (On a related topic, learn more about IT documentation examples and best practices.)
What is an IT Topology Map?
A map is a powerful tool for organizations to visually represent their entire IT topology. It displays how different infrastructure components are interconnected and dependent on one another. By providing a bird’s-eye view of the whole system, a map enables administrators to understand the flow of information and identify potential issues or bottlenecks.
With this level of visibility, IT teams can quickly locate problem areas and take the necessary steps to address them, improving system performance and reducing the risk of potential security threats. Visualizing IT topology can be invaluable for ensuring that infrastructure runs smoothly and the business’s assets are being used to their full potential.
What Does an IT Topology Mapper Do?
IT topology mappers have become essential for organizations that want to better understand their IT infrastructure. Automated detection and analysis can help overcome the lack of documentation that often plagues many IT environments. By crawling through an organization’s existing IT infrastructure, these mappers enable auto-discovery for all assets and their interconnections, creating accurate documentation of what assets exist on networks at any given point in time.
This helps administrators identify and resolve any issues or vulnerabilities quickly. Additionally, these tools can uncover shadow IT, which refers to the use of unauthorized or unapproved devices, applications, or software within an organization. This information can be crucial for understanding security posture and preventing potential security breaches.
Another key role of IT topology mappers is to provide essential information for decision-making. By identifying and mapping core infrastructure in relation to other assets, these tools help companies understand the dependencies between different parts of their IT infrastructure. This is essential data for planning staffing requirements and making decisions related to modernization or virtualization.
IT topology mappers can also aid in disaster recovery planning, as they provide a comprehensive understanding of the organization’s IT infrastructure and how all assets are interconnected. This enables administrators to make informed decisions about protecting their assets during a disaster or outage.
What Are the Purposes and Benefits of IT Topology Mapping?
Overall, IT topology mapping helps organizations make better decisions and improve operational efficiency. Aside from the advantages already mentioned, the better optics achieved via topology mapping can also deliver the following benefits across a business.
Improved Network Performance
Topology mapping is a valuable tool for businesses to clearly represent their network’s structure and flow of information. By identifying the various components and connections within the network, topology mapping allows businesses to comprehensively understand their infrastructure and identify potential issues.
With topology mapping, businesses can quickly identify areas where possible bottlenecks and suboptimal routing occur. This information is crucial, as it enables them to make informed decisions about optimizing their network architecture. Businesses can achieve better performance and reliability by making changes to their infrastructure based on topology mapping insights.
For instance, topology mapping may reveal that specific devices or components are overloaded with traffic, causing slow or unstable network performance. By reconfiguring the network, such as adding more devices or rerouting traffic, businesses can improve overall network performance and reduce the likelihood of disruptions.
Enhanced Security
Topology mapping provides businesses with a comprehensive illustration of their network’s structures and dependencies. By analyzing this information, teams can identify potential security risks, such as unsecured network segments and vulnerable devices. This information is critical, as it allows them to prioritize remediation efforts based on risk and exposure, achieving maximum security improvements with the least investment and maximizing ROI.
For instance, topology mapping may reveal that a particular network segment is unsecured, making it vulnerable to cyberattacks. By identifying this weakness, teams can prioritize remediation efforts, such as adding encryption, implementing access controls, and securing the network segment. Additionally, they may find that specific devices, such as outdated routers or firewalls, have vulnerabilities that must be addressed to prevent security breaches.
Prioritizing security improvements based on risk and exposure allows businesses to allocate their resources effectively, first addressing the most critical issues. This approach reduces the likelihood of security incidents and ensures the company gets the most significant return on investment from its security efforts.
Increased Reliability
Topology mapping is an effective method businesses use to discover potential points of failure within their network infrastructure. This process helps to identify components and connections that, if disrupted, could cause significant impacts on business operations, resulting in costly downtime.
By using topology mapping, businesses can proactively identify and resolve potential points of failure that may arise due to incidents or maintenance. This approach ensures their network infrastructure is highly resilient and can withstand outages without causing business disruptions. Additionally, it enables businesses to avoid costly, time-consuming remediation efforts after an incident.
For instance, topology mapping may identify a key network switch that supports critical applications and services, which, if disrupted, could cause significant impacts on business operations.
Better Troubleshooting
IT topology mapping helps organizations understand their infrastructure and relationships, leading to more efficient issue identification and resolution. By creating a visual representation of the network infrastructure, topology mapping helps administrators identify potential issues and dependencies and thus facilitates pinpointing the root cause of problems.
Moreover, IT topology mapping allows organizations to optimize their infrastructure by identifying potential points of failure and implementing measures to prevent disruptions. This approach streamlines the troubleshooting process and reduces the risk of related issues arising in other IT assets, rendering future troubleshooting more straightforward.
By using IT topology mapping to optimize their infrastructure, organizations can reduce downtime, increase productivity, and save costs associated with remediation efforts.
Improved Scalability
With the assistance of IT topology mapping, organizations can make informed decisions and implement necessary changes to enhance their infrastructure. By doing so, they can reduce costs associated with modernization and ensure their infrastructure is efficient and scalable enough to support future growth.
Moreover, optimizing IT infrastructure can significantly improve the performance and reliability of the network, minimizing the risk of disruptions and downtime. This, in turn, helps businesses maximize their productivity and operational efficiency.
Efficient Planning and Design
IT topology mapping helps companies gather and analyze relevant data to make informed decisions when planning their IT infrastructure. This results in an optimal design that fully factors in business objectives, budget constraints, and technical requirements.
For example, choosing the most appropriate network topology, such as star, mesh, or hybrid, can impact the network’s scalability, reliability, and performance. Similarly, selecting the proper hardware and software components, like servers, routers, switches, and firewalls, based on compatibility, performance, and cost-effectiveness is critical to ensure smooth and efficient operation. Configuring the network in the most efficient way possible can also maximize throughput and minimize bottlenecks.
What to Look for in IT Topology Mapping Tools
When it comes to mapping tools, not all are created equal. A combination of speed, accuracy, and the ability to continuously update findings is essential to achieve the best results. However, ensuring that the company’s IT assets aren’t impacted negatively during the mapping process is equally important.
Software that performs well in all of these areas is required for keeping maps up-to-date and accurate—something that is especially important in today’s fast-paced business environment, where changes can occur quickly and unexpectedly. With the right mapping tool, you can stay on top of these changes and make informed decisions based on current data.
When selecting a topology mapping tool, organizations should seek out the following attributes.
Speed for Effective Mapping
For maintaining effective mapping, speed is of the essence. It is important to use fast and efficient scanning tools to gather information and compile it in a timely manner. Delays can be costly for IT working to keep up with the fast pace of business. Other teams cannot wait while technology teams gather the data necessary for accurate assessments.
Slower scanning processes can also lead to incomplete or inaccurate assessments, as changes may occur before the scan is completed. This can make it challenging to take action based on the results. Staff members who rely on mapping tools need results quickly to make assessments and take action as required.
So it’s vital to use mapping tools that can deliver results rapidly in near real-time while maintaining accuracy. By doing so, the organization can be certain they are taking action based on the most current data available.
Accuracy to Reduce the Attack Surface
Accuracy is about the depth of visibility and ensuring that all assets are mapped—and nothing is missed. Failing to detect assets can result in shadow IT or production assets existing without oversight or necessary controls, such as patching to ensure security posture. Due to an inaccurate assessment, undetected assets create a broad unseen attack surface.
Business-critical applications may not always show dependencies, reducing the organization’s ability to plan for disaster recovery (DR) scenarios. For example, critical infrastructure may not be brought up in the proper order. This can lead to failures on startup or errors that require troubleshooting and management. These failures increase the time to properly recover, magnifying the overall impact of a disaster.
When implementing IT topology mapping for physical-to-virtual (P-to-V) migrations, any missing assets can damage the transformation process. Critical infrastructure can also be missed, losing essential functionality. If P-to-V planning fails to account for all assets, it can result in erroneous cost estimates, incorrect prioritization, or a less-efficient final cloud transformation. This is why the most highly sought-after solutions have a track record of 100% detection accuracy.
Automation to Optimize Operations
Automated assessments are valuable for organizations that want to improve the efficiency of their asset-mapping processes. By taking on repetitive tasks, automation frees up staff members to focus on other high-value tasks while maintaining current and accurate mapping.
Another key benefit is that it can automatically update and revise mapping in response to changes in the IT infrastructure. This is critical due to the dynamic nature of modern IT infrastructure, especially in the cloud, and ensures that the organization’s asset mapping remains up-to-date and accurate.
In contrast, manual updates are insufficient for tracking IT topology, especially as the time between manual updates can allow for potential attack surfaces to form. By using automation to maintain mapping, organizations can reduce the risk of security incidents and improve the efficiency of their IT operations.
Mastering the IT Topology Challenge
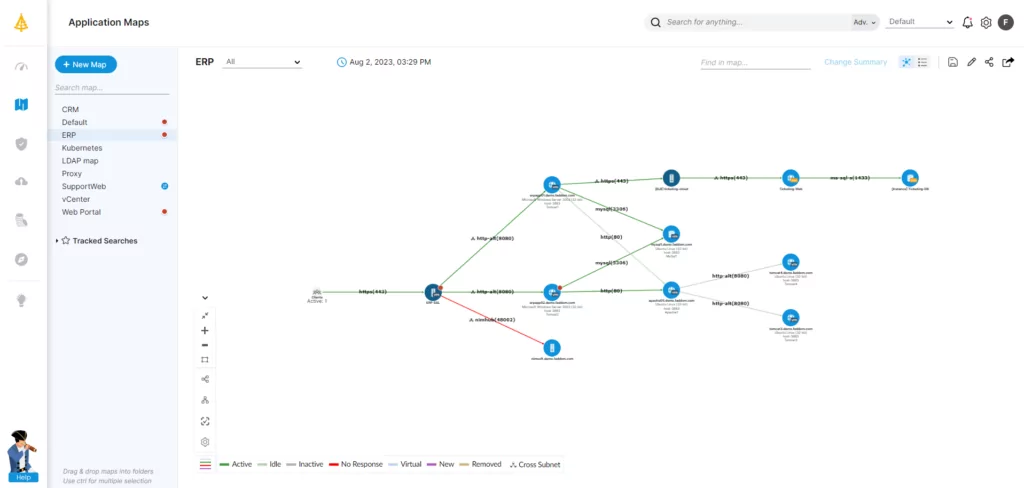
IT topology mapping is an essential tool for modern organizations looking to optimize their infrastructure, improve efficiency, and enhance their security posture. By using such tools, organizations can gain valuable insights into their IT environment, identify potential vulnerabilities, and make informed decisions around staffing, modernization, and disaster recovery.
Visualizing IT topologies can improve network performance, enhance security, increase reliability, enable better troubleshooting, and support efficient planning and design. Faddom’s IT topology mapping helps you visualize your on-premise and cloud infrastructure with continuous, automatic updates — in as little as 60 minutes and without agents. Start a free trial today!









