What Are Ransomware Protection Solutions?
Ransomware protection solutions are comprehensive tools and strategies designed to defend organizations against ransomware attacks. These attacks occur when cybercriminals encrypt an organization’s data and demand payment to restore access.
Ransomware solutions address the full spectrum of the ransomware threat lifecycle, including prevention, detection, response, and recovery. Their main role is to reduce the risk of infection, minimize disruption during an attack, and enable rapid restoration of operations.
Modern ransomware solutions combine multiple layers of protection, such as endpoint security, real-time threat detection, automated backup, privilege control, and incident response. They are frequently updated to counter evolving tactics used by attackers. They also help organizations avoid the severe financial and reputational impacts associated with ransomware incidents.
Table of Contents
ToggleThis is part of a series of articles about Ransomware-FM
Key Features of Ransomware Protection Solutions
Ransomware solutions typically offer the following capabilities.
Real-Time Threat Detection and Prevention
Real-time threat detection and prevention features monitor network traffic, file activities, and user behaviors using advanced technologies such as machine learning, behavioral analytics, and threat intelligence feeds. They can identify suspicious patterns, block known malware signatures, and flag unexpected file encryption before significant damage occurs.
Effective real-time prevention often includes sandboxing, isolating potential threats for analysis, and heuristic scanning, which detects unknown or zero-day ransomware variants. This proactive approach ensures that even new or modified attack techniques don’t bypass security controls.
Endpoint Protection
Endpoint protection secures user devices such as laptops, desktops, smartphones, and servers. These solutions use antivirus engines, exploit prevention modules, and application allowlisting to neutralize payloads before they can trigger encryption. They also block malicious downloads, prevent lateral movement across the network, and manage device security configurations to address vulnerabilities that ransomware often exploits.
This broad coverage ensures consistent application of security controls, even for remote or bring-your-own-device (BYOD) users. By placing security directly at the endpoint, organizations strengthen their overall posture and reduce risk at the most common points of compromise.
Automated Backup and Recovery
Automated backup and recovery solutions continually create copies of critical data and configurations, storing them securely, often offline or in the cloud. Should a ransomware attack occur, organizations can quickly restore clean, uninfected data without succumbing to ransom demands. These systems regularly test backup integrity, ensuring that recovery points are viable and reliable during an emergency.
Schedules and policies are customizable, letting administrators balance recovery point objectives (RPOs) and recovery time objectives (RTOs) to meet business needs. Advanced solutions may offer immutable storage, which protects backup files from being altered or deleted by malware. Automated orchestration further reduces manual steps, enabling rapid, consistent recovery at scale.
Learn more in our detailed guide to ransomware recovery
Access Control and Privilege Management
Access control and privilege management limit ransomware’s impact by enforcing the principle of least privilege: users and applications only have access rights strictly necessary for their tasks. Security solutions monitor account activity, flag privilege escalations, and automatically block risky behaviors such as unauthorized access attempts or credential misuse.
Role-based access, just-in-time privilege elevation, and multifactor authentication (MFA) are key tools within this category. They bolster defense by making it harder for ransomware to exploit compromised credentials or move laterally within a network. Regular audit logs and comprehensive reporting help with compliance requirements.
Incident Response and Containment
Incident response and containment features detect incidents, isolate infected endpoints, and activate playbooks that guide security teams through mitigation steps. Automated containment may involve killing malicious processes, disconnecting systems from the network, or rolling back unauthorized changes, halting the spread of ransomware before encryption completes.
Integration with ticketing systems, SIEM platforms, and threat intelligence sources allows for a coordinated incident response. Rapid communication and reporting enable incident teams to analyze attacks, identify their origin, and initiate remediation. Post-incident forensics and root cause analysis further strengthen long-term resilience.
Notable Ransomware Protection Solutions
1. Faddom

Faddom enhances ransomware protection by providing complete, real-time visibility into all application and server dependencies across on-premises, hybrid, and multicloud environments with application dependency mapping. By automatically mapping east-west and north-south traffic, it enables organizations to identify vulnerable connections, shadow IT, and unexpected communication paths before attackers can exploit them.
In the event of a ransomware incident, Faddom acts as a dynamic blueprint of your IT environment. This allows teams to isolate affected systems, verify clean recovery points, and restore services without any guesswork. Its agentless, continuous discovery process ensures that the maps are always accurate, supporting prevention, response, and post-attack analysis.
Key features include:
- Agentless and continuous discovery: Map your entire environment safely in under 60 minutes without installing agents or disrupting operations.
- Hybrid and multicloud coverage: Unify visibility across on-premises, virtual, and cloud infrastructures for a complete defense picture.
- Real-time dependency mapping: Instantly visualize how ransomware could spread across interconnected systems.
- Security posture enhancement: Detect risky lateral movement paths and unauthorized services before attackers do.
- Incident containment and recovery: Identify impacted servers and validate dependencies for faster, safer restoration.
- AI-powered anomaly detection: Faddom’s Lighthouse AI flags unusual traffic and behavioral patterns, enabling faster containment before systems are encrypted.
Book a demo to get your live dependency map in under an hour!
2. NinjaOne

NinjaOne’s Ninja Protect offers a ransomware defense platform for managed environments. It combines prevention, detection, response, and recovery capabilities to help organizations reduce exposure, stop active threats, and recover from ransomware incidents.
Key features include:
- Endpoint management: Centralized management of endpoints with security features to simplify visibility and control.
- Automated patch management: Keeps systems up to date with timely patches.
- Endpoint backup: Regular, automated backups of endpoint data ensure recovery without paying ransom.
- Bitdefender GravityZone integration: Provides layered protection with threat prevention, detection, and behavioral analysis.
- Threat security: Stops ransomware variants using scanning, behavioral detection, and heuristic analysis.
Source: NinjaOne
3. ManageEngine
ManageEngine’s Ransomware Protection Plus is a multi-layered defense system to detect, neutralize, and recover from ransomware attacks. The solution combines behavioral detection, fileless malware protection, and autonomous response to stop ransomware before it causes serious damage.
Key features include:
- Behavioral detection engine: Identifies abnormal file changes, deletions, and process behaviors without relying on static malware signatures.
- Fileless malware protection: Detects ransomware executing from memory or scripts, bypassing traditional antivirus detection methods.
- Offline and edge-based detection: Offers protection without constant network connectivity or regular signature updates.
- Device isolation: Automatically quarantines compromised devices to contain ransomware spread across the network.
- Root cause analysis and attack mapping: Tracks the ransomware kill chain, mapping TTPs using MITRE ATT&CK and VirusTotal data for deeper investigation.
Source: ManageEngine
4. Fortra

Fortra Ransomware Defense offers a layered solution to detect, prevent, and mitigate ransomware threats across the security lifecycle. It delivers protection through early threat detection, prevention mechanisms, and recovery support.
Key features include:
- Layered prevention approach: Combines vulnerability management, secure file transfer, data protection, and email security to block ransomware.
- Threat detection: Continuously monitors for ransomware indicators using detection capabilities that surface threats.
- Data protection and access control: Uses encryption, digital rights management, and data classification to secure sensitive information and enforce compliance policies.
- Vulnerability management: Identifies and prioritizes exploitable weaknesses with tools for web application scanning, application security testing, and system-level assessments.
- Digital risk protection: Detects and neutralizes external threats like brand impersonation, data leaks, and account takeovers.
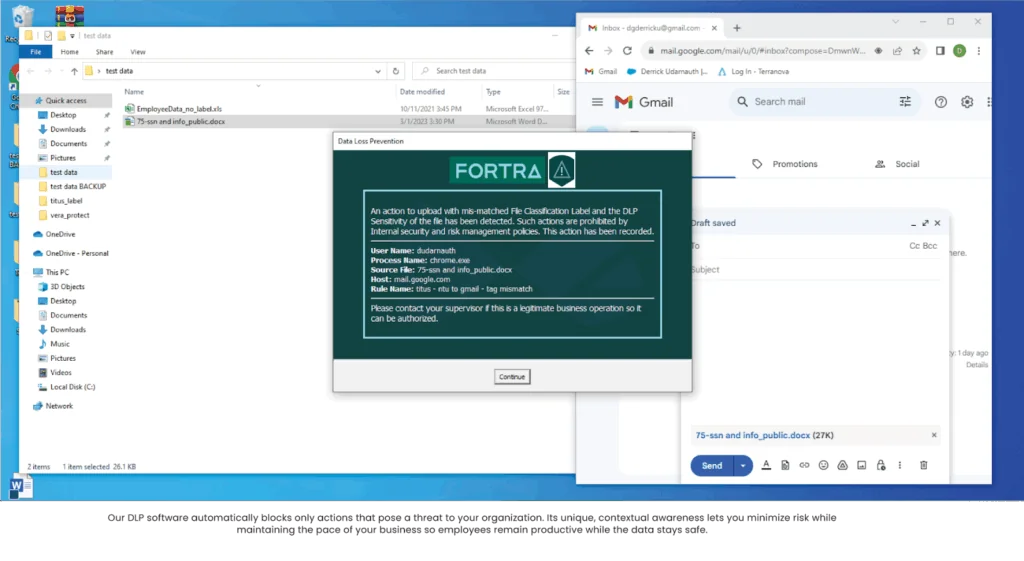
Source: Fortra
5. Malwarebytes

Malwarebytes offers an anti-ransomware solution for individuals, small businesses, and IT security teams. It focuses on simplicity, automation, and proactive threat elimination. It delivers ransomware protection that fits into the security stack without requiring extensive setup or dedicated security staff.
Key features include:
- Ransomware protection: Continuously scans for and blocks ransomware threats before they can encrypt files or lock devices.
- Lightweight scanning: Malwarebytes Premium performs rapid scans with low resource consumption, maintaining system performance during regular use.
- Automated threat removal: Once threats are detected, users can remove ransomware and associated malware.
- Behavior-based detection: Identifies suspicious behaviors and patterns tied to ransomware attacks.
- Three-step recovery: Includes a simple process: scan, review threats, and remove ransomware.
Source: Malwarebytes
Endpoint Security Solutions with Ransomware Protection
6. Acronis

Acronis delivers a ransomware protection platform that merges cybersecurity with data backup and disaster recovery. It protects endpoints and data through AI-driven threat detection, automated recovery, and integrated protection policies.
General features:
- Integrated cyber protection: Combines data backup, cybersecurity, and endpoint management in one platform.
- Automated patch management: Identifies and installs missing patches to reduce system vulnerabilities.
- Forensic backup: Captures disk images for use in investigations and compliance.
- Data loss prevention: Monitors sensitive data movement to prevent leaks or unauthorized sharing.
Ransomware protection features:
- AI-based detection: Uses machine learning to identify ransomware activity before damage occurs.
- Automatic recovery: Restores affected files from secure backups without manual intervention.
- Behavioral monitoring: Tracks processes in real time to block abnormal encryption patterns.
- Safe recovery: Ensures restored systems are malware-free before bringing them back online.
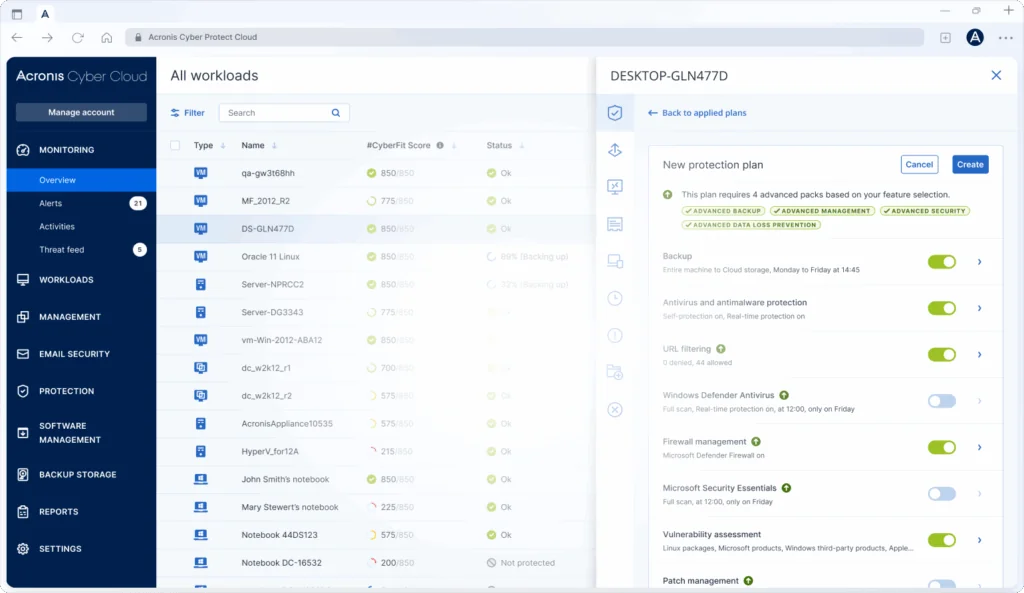
Source: Acronis
7. CrowdStrike Falcon

CrowdStrike Falcon delivers ransomware protection by combining AI-powered prevention, detection, and threat hunting. Designed to stop both known and emerging ransomware threats, the Falcon platform gives security teams visibility into endpoint activity and equips them with the tools to respond.
General features:
- Ransomware prevention: Uses machine learning, behavioral analytics, and threat intelligence to prevent both known and unknown ransomware from executing.
- Endpoint monitoring: Provides continuous visibility across endpoints.
- Incident visualization: Features process graphs and activity trees that show ransomware tactics.
- Cloud-native platform: Delivers protection without on-premises infrastructure or signature updates.
- Scalable deployment: Supports thousands of endpoints with a lightweight agent.
Ransomware protection features:
- Threat hunting: Falcon OverWatch teams search for threats using tailored intelligence.
- Unified security operations: Integrates prevention, detection, and response into a single platform.
- Malware-free attack detection: Identifies ransomware delivered through fileless or script-based methods.
- Automated response actions: Isolates compromised systems and removes malicious files with minimal delay.
Source: CrowdStrike
8. Sophos Endpoint

Sophos Endpoint provides behavior-based ransomware protection to stop threats, including remote encryption attacks, before they can lock down data. Using technologies like CryptoGuard and anti-exploit mechanisms, it blocks ransomware, reverses damage automatically, and prevents threat actors from spreading across the network.
General features:
- Anti-exploitation engine: Includes over 60 preconfigured exploit mitigations to stop common attacker techniques without requiring manual tuning or prior knowledge of the threat.
- Synchronized security: Shares threat intelligence between Sophos endpoint and firewall products, enabling coordinated defense and auto-isolation of infected systems.
- Endpoint protection: Requires no manual intervention during detection or rollback.
- Web filtering and control: Blocks access to malicious websites and restricts risky web categories.
- Application control: Prevents execution of unauthorized applications across endpoints.
Ransomware protection features:
- CryptoGuard technology: Detects and halts ransomware by analyzing behavior, not just signatures, and automatically rolls back encrypted files to their original state.
- Remote ransomware defense: Blocks attacks attempting to encrypt files over the network from compromised external devices.
- Automated damage reversal: Restores affected files without requiring backup systems.
- Anti-lateral movement: Stops ransomware from spreading to other devices in the network.
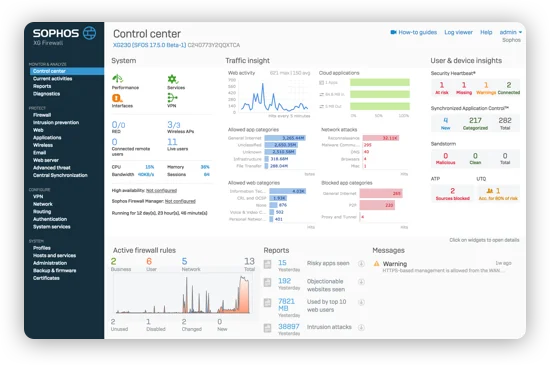
Source: Sophos
9. SentinelOne Singularity

SentinelOne Singularity Complete is an AI-enabled security platform that offers protection for endpoints, servers, and cloud workloads. By combining prevention, detection, response, and recovery into a lightweight agent, it helps organizations to stop ransomware.
General features:
- AI-driven prevention: Uses on-device machine learning to detect and block known and unknown ransomware.
- Behavioral detection: Identifies malicious activity like encryption patterns and zero-day behaviors using static and behavioral AI models across endpoints and workloads.
- 1-click rollback: Automatically restores systems to their pre-attack state.
- Autonomous response: Automates containment actions such as killing malicious processes, isolating devices, and blocking lateral movement).
- Unified agent and console: Manages endpoint, cloud, and identity protection from a single agent and centralized interface.
Ransomware protection features:
- Real-time behavioral AI: Monitors all activity to stop encryption-based attacks before damage occurs.
- Storyline technology: Builds context around processes to reveal how ransomware enters and spreads.
- Fileless attack defense: Detects ransomware that operates in memory without leaving a file trace.
- Distributed recovery: Restores systems across an organization from tamper-proof local snapshots.
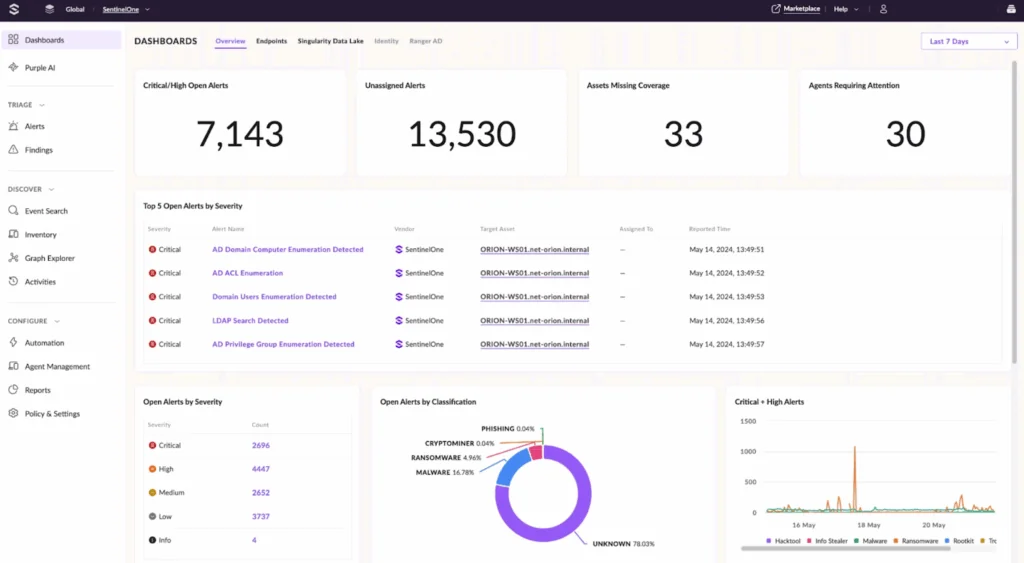
Source: SentinelOne
10. Spin.ai

Spin.AI delivers Ransomware Detection & Response (RDR) as part of its SpinOne platform, offering SaaS-native ransomware protection purpose-built for Google Workspace and Microsoft 365. It is specifically designed to stop ransomware attacks inside cloud environments, where many business operations now live.
General features:
- Detection and response: Leverages machine learning algorithms to identify ransomware behaviors and automatically trigger a response without human intervention.
- Source blocking and access revocation: Stops attacks by revoking API access to malicious apps or browser extensions.
- Data audit and compliance reporting: Provides visibility into SaaS data usage and supports regulatory compliance.
Ransomware protection features:
- Ransomware monitoring: Continuously scans SaaS environments using heuristic and behavioral analysis to detect ransomware.
- 2-hour recovery SLA: Reduces ransomware-related downtime from the industry average of 21–30 days to under 2 hours.
- Automated file recovery: Restores compromised data from immutable backups, preserving original folder structure, sharing permissions, and file integrity.
- Granular recovery options: Allows administrators to restore individual files, folders, or entire user accounts.
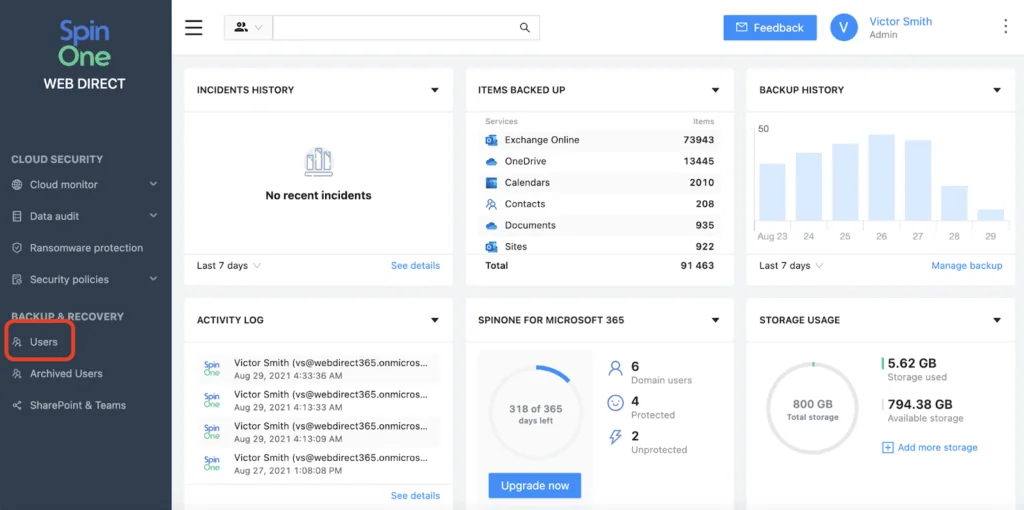
Source: Spin.AI
Conclusion
Ransomware solutions provide layered protection that spans prevention, detection, containment, and recovery. By combining technologies such as behavioral monitoring, automated response, and resilient backup, they minimize the impact of attacks while enabling rapid restoration of business operations. As ransomware tactics continue to evolve, adopting a multi-faceted defense strategy ensures that organizations can maintain resilience, protect critical data, and reduce downtime in the face of ongoing threats.



